The Background
With the thankfully good effort from our credited brothers, we MalwareMustDie, NPO (read: Malware Research Group & Anti Cyber Crime Workgroup) herewith disclose the existence of an evil service contains the full codes of malicious tools, in details: exploitation tools to distribute malware, hack tools, bruting tools, shell exploitation tools, spam bot tools, malware crypter, malware binary protector and binary packer, password cracking tools and its wordlists, some hacking and infection tools manuals and blackhat's howto picture and texts, that are mostly shared by the known hack group ANTICHAT.RU.The data or the contents itself is varied from 2011 and 2012 (mostly) with some new tools or manuals made in 2013.
What service?
The domain name owned and contains these data is (REDDACTED).XAKEP(.)BIZ (see the pictures snapped for the PoC) which the name explains more than words to all of us. For the law enforcement friends you will be sent email from our side contains the case's cyber crime investigation evidence which leading to the suspect ID of the site's owner. Noted the real domain name was a bit different (in purpose), is covered for law enforcement work purpose.
Please noted: Your direct access to the site is monitored by the related crook and there ARE accidents reported after accessing the site, that's why I announced the below warning:
Friends. For your safety. DO NOT access directly to the xxx(.)xakep(.)biz source of the malware tools disclosed in http://t.co/PmOFJmVKt1
— MalwareMustDie, NPO (@MalwareMustDie) April 14, 2014The Shares
We close the direct download sharing of this case: http://t.co/PmOFJmVKt1 since the majority of the industries downloaded the tars. Thank's.
— MalwareMustDie, NPO (@MalwareMustDie) April 14, 2014For security purpose the further data will be informed by mostly pictures and video as per following sections. We packed everything that we could fetch in a tarball as per snapshot in the picture below. This tarball is shared in very closed security industry ONLY via our colleague's mail list (please make sure you join the mail list, and I am sure you know what I mean if you follow our previous disclosures). So if you are in AntiVirus, Malware Filter, or Web/Proxy Attack Filtration (+IDS/IPS) industry's/entity's researchers and want to have the sample but not getting it yet, you can send request by writing comment below this post (it will be not published, explaining yourself and legit/non-free entity's email addresses will make the vetting process faster) and your request will be followed properly. The same goes to Government Security Agencies and Law Enforcements Agency's researchers.
The reason why we are limiting the shares is not for being "a picky" to whom to share the materials to, like we always do with the malware samples, but we just want to do the responsible and right sharing. This case is sensitive under below two points. (1) There is an active investigation on this case. (2) These are not malware samples to be sharable to be learned to crack/reverse/analyze to, but these are the real malware source codes, malicious tools and account hacking tools.. in ready to use form, shortly the real stealer tools! These tools are the subject against the law and order in many countries, even to just owning them can make yourself being jailed in my country. Some of these tools are still actively spotted in crime operation scene in the internet. Which means: IF these tools got leak or go to the irresponsible hands..this can be used for the VERY VERY BAD purpose and MalwareMustDie doesn't hold any responsibility or risk for it.
In some countries that we are actually living it is forbidden to pass around these kind of tools w/o strict permission to the appointed limited entities only. So we are sorry for the bummer to the researcher friends, we do want to share everything, but in this case we have to do it right. If you eager to have these materials, please kindly contact to your known security entity to contact us for you then we can discuss the legit possibility for the purpose.
Why did we post here and announce "the sharing" then? Because in reality there are many security legit entity which haven't seen these materials that actually being used by a cyber crime member, the knowledge and this awareness is a must share (to entities and to user level). We are trying to do that right here, with responsibility. So we assure you, we vetted the contacts, we monitor the download log strictly to make sure unnoticed party not to access, we don't share to unknown person and we deal with legit entity for sharing on this level to the widest reachable target in security community.
We are sorry if our share scheme is not satisfactory for some security researchers friends. For them, be free to send us comment in the below of this post with explaining the real identification then I am assuring you you will be assisted.
Thank you.
The Tarball:
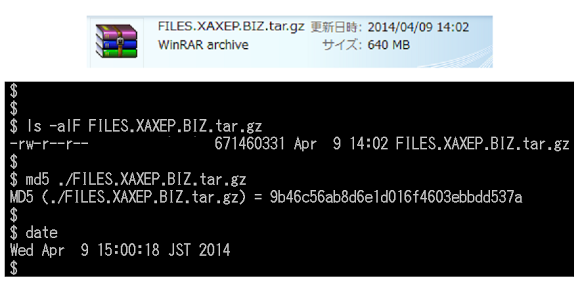
Full Directory Structure

Noted: New released directories were wrapped in additional package, if you don't get it contact us.
The Pictures & Video of the Evil Contents
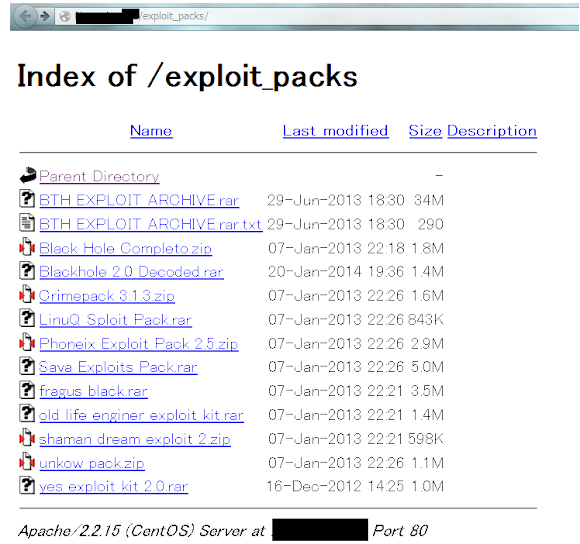
Various Exploit Kit's installer packages:
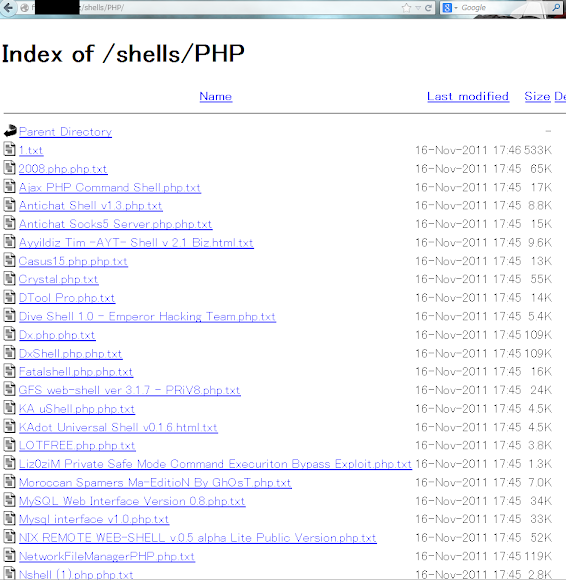
Web Shell in various scripts with or w/o CGI, below is PHP ones only:
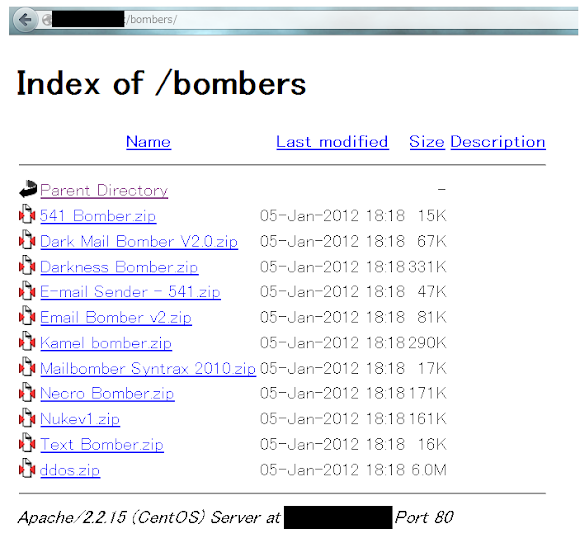
Various tools of DDoS, Spammer & Bruter/Bombers:
Various Hack and Infection tools:
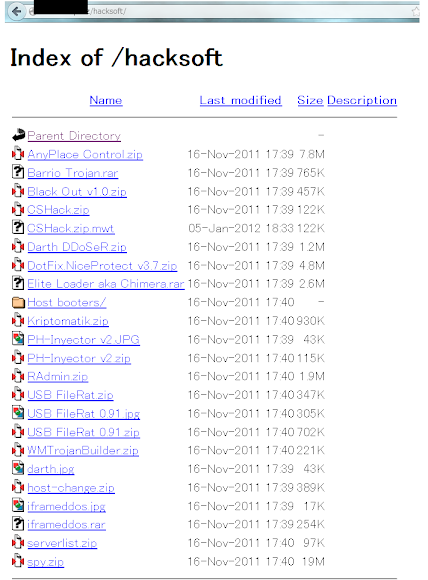
Various Malware Binary packers
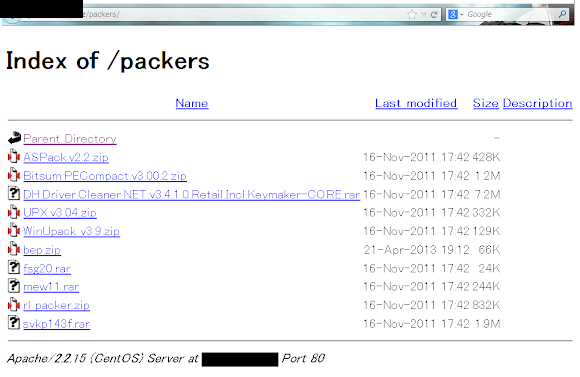
Various Malware Binary Crypters and Protectors
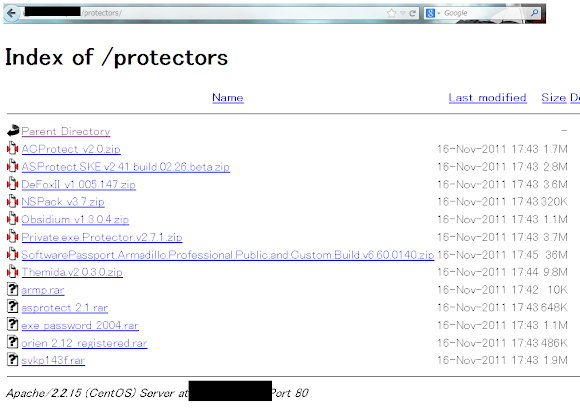
Additionals
Account hacking tools
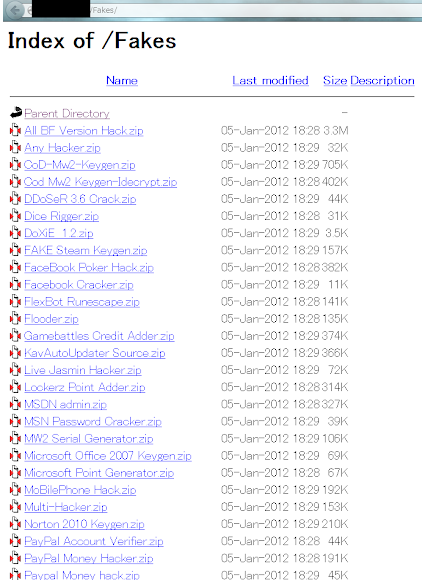
DDoS/Blackhole Decoded
Botnet Installers & Source Codes

Common Proxy Tools used by Malware Crooks

And believe us, there are MANY MORE of those malicious tools than these pictures can show. The video (below) we recorded after collecting all of the content's data right before archiving will show more details:
Epilogue
This information is shared for the effort in suppressing cyber crime activities in the internet. We do not keep and own the malicious contents found, as experts we confirmed the information's credibility and as good citizens we follow with the share effort accordingly. Using this very precious information the filtration scheme can be applied better for the security and filtration products to protect innocent people from being abused by these malicious tool's users.
MalwareMustDie is working close and supporting to law enforcement agencies to deeper investigation upon mentioned threats. And we against any act that made our beloved internet becoming a junk places for malware, exploitations, extortion and stealing playground for cyber crime crooks.
We will continue to share important findings like this. Please support us.
Credit: Mr. Adam Ziaja of ComCERT, Poland.
Additional Credit: Mr. Mohab Ali of Synapse-Labs.
All materials checked and tarballed by @unixfreaxjp "as per it is" to support cyber crime investigation.
Stay safe always, friends. We have an uncivilized "jungle" claimed name of "internet" out there.
#MalwareMustDie!
