in --> HERE and--> HERE. Please bear for I will not include the previous exposed details.
Background
Again, do not believe on what you read without checking, like this AV marketing issue-->HERE
The post is without any technical analysis background specifically of the threat's sample on its malicious PoC, nor the share information of the verdicted subject's hashes. Not to mention the "huge intolerable research term miss" by mistaking ZeroKit(root/boot kit) as ZeroAccess..=sigh=
I wrote the above statement as a productive criticism to demand an improvement and a fix on current technical level of quality insurance form a technical post that coming from a "reliable" "big brand" in security industry which many people count, trust and generously pay in yearly basis for its licenses.
And additionally, in the country where I live and grow, if such vendor, if a maker made such mistake, it will be a press conference to make public apology to restore the trust of the market back, which in this case the appointed security maker is not. If in my company, the person in charge for those errornous "technical white paper" will be fired for sure!
This post is a PoC to counter the statement that says that "ZeroAccess was 50% neutralized" from a same maker appointed above. Is actually a lesson to all of us to be more criticized on such statement, specially to the one who has not publicly announce its blocking list, samples of what had been blocked, and so on. What we have found shows that ZeroAccess is out there active in distribution in same volume of P2P or domains, and improving its malicious act by using accompanied trojans. My question is simple: "What had been blocked???" < You all have your right judge it yourself after reading the below details.
Just when I hope to find alive PoC of ZeroAccess (or Sirefef), our crusader friend found it first and mentioned: VERY ALIVE:
Wasting no time, I went deep dive and surprised to the fact of what I found.Sirefef / ZeroAccess found on 158.255.6.116 (Russian Federation) VT: 29/45 https://t.co/s5ARSXa38N #MalwareMustDie CC:@Trojan7Sec
— Mosh (@nyxbone) October 7, 2013
The Infection Source
The IP: 158.255.6 .116 is actively distributing ZeroAccess among other threats. URLQuery report is -->HERE Below is Virus Total's passive DNS report for the IP Address, link is--->HERE
2013-09-27 [34]fseggs2.aasdgaa.info 2013-10-07 [35]gtrfeds.artisanent.info 2013-09-28 [36]mgthnse.artisanent.info 2013-09-27 [37]mscderg.artisanent.info 2013-10-07 [38]rewdert.aasdgaa.info 2013-09-27 [39]rsdfcs1.artisanent.info 2013-09-25 [40]swdasc1.aasdgaa.info 2013-09-28 [41]ytedvh2.artisanent.info 2013-09-26 [42]zdegfsg.artisanent.info 2013-09-28 [43]ztgdbsw.artisanent.infoList of the downloaded URL:
6/38 2013-10-07 01:35:29 h00p://rewdert.aasdgaa.info/explorer.exe 7/38 2013-10-07 01:33:38 h00p://gtrfeds.artisanent.info/m.exe 2/39 2013-09-28 11:16:46 h00p://mgthnse.artisanent.info/ 7/39 2013-09-28 11:16:52 h00p://ztgdbsw.artisanent.info/z.exe 5/39 2013-09-28 10:16:18 h00p://mgthnse.artisanent.info/m.exe 2/39 2013-09-28 10:16:11 h00p://ytedvh2.artisanent.info/zs.exe 10/39 2013-09-27 13:15:46 h00p://mscderg.artisanent.info/m.exe 2/39 2013-09-27 11:56:04 h00p://ytedvh2.artisanent.info/z.exe%5B/code%5D 5/39 2013-09-27 11:29:16 h00p://ytedvh2.artisanent.info/z.exe 3/39 2013-09-27 02:35:59 h00p://rsdfcs1.artisanent.info/m.exe 2/39 2013-09-26 11:41:46 h00p://fseggs2.aasdgaa.info/iexplorer.exe 3/39 2013-09-26 11:35:55 h00p://zdegfsg.artisanent.info/z.exe 1/39 2013-09-25 21:17:10 h00p://mscderg.artisanent.info/Strong verdict of hashes:
15/48 2013-10-07 01:35:46 [57]67e11fab0bff36a256e003b00658e11e9ef68c07bd30279ba2dc5da0c8379fee 29/45 2013-10-07 01:34:41 [58]9dcbb64f365fdf6f80607d297d88134efa4a74ebadc3cc3c5effa9c4f8625937 25/48 2013-09-28 11:16:54 [59]b9e7adce23242e501ad04fd3c8dec6feeaddee9a7ef799879ffbaf9f6b67f594 4/48 2013-09-28 10:16:54 [60]6369f432a8383b3e802c2db0f69503f09bd047ddbe02d4fe971826c8ac29adfb 17/48 2013-09-27 13:16:32 [61]4c42befd1f6392339f6a4333642ad3a27ca16312616c83eb2586de63b275faae 16/48 2013-09-27 02:45:46 [62]c0b1fac70a57c7b23c4640d7049cbb91890d650bbfdf44e02143ba3e8c9038b5 8/47 2013-09-26 11:41:59 [63]dc5f3a223bf9a2ea3131a218472a3dfd2dfc9d628476e85376570d91c8ddcc4aWhile OpenDNS recorded also the infection requests to the below domains:
huyftdr.artisanent.info rewdert.aasdgaa.info jihuyg1.aasdgaa.info egthyrf.aasdgaa.info hytgder.artisanent.info ztgdbsw.artisanent.info mgthnse.artisanent.info rsdfcs1.artisanent.info fretsdf.aasdgaa.info grsjli1.aasdgaa.info mscderg.artisanent.info zdegfsg.artisanent.info fseggs2.aasdgaa.info gedsetu.aasdgaa.info swdasc1.aasdgaa.infoIt is all served in HOSTKEY.RU
inetnum: 158.255.0.0 - 158.255.7.255 netname: RU-HOSTKEY-20111114 descr: Mir Telematiki Ltd country: RU org: ORG-MTL21-RIPE admin-c: PC7356-RIPE tech-c: PC7356-RIPE tech-c: PC7356-RIPE status: ALLOCATED PA mnt-by: RIPE-NCC-HM-MNT mnt-lower: MTLM-MNT mnt-routes: MTLM-MNT remarks: abuse-mailbox: abuse@hostkey.com source: RIPE # Filtered organisation: ORG-MTL21-RIPE org-name: Mir Telematiki Ltd org-type: LIR address: Mir Telematiki Ltd Petr Chayanov Lva Tolstogo, 19/2 119021 Moscow RUSSIAN FEDERATION phone: +74992463587 fax-no: +74992463587 mnt-ref: MTLM-MNT mnt-ref: RIPE-NCC-HM-MNT mnt-by: RIPE-NCC-HM-MNT abuse-mailbox: abuse@hostkey.ru abuse-c: HA2800-RIPE source: RIPE # Filtered person: Peter Chayanov address: Moscow, Russia phone: +7 499 246 3587 nic-hdl: PC7356-RIPE mnt-by: MTLM-MNT abuse-mailbox: abuse@hostkey.ru source: RIPE # FilteredSame actors controls these domains, non-hacked site:
Domain ID:D48479867-LRMS Domain Name:ARTISANENT.INFO Created On:24-Nov-2012 12:27:33 UTC Last Updated On:24-May-2013 12:39:48 UTC Expiration Date:24-Nov-2013 12:27:33 UTC Sponsoring Registrar:GoDaddy.com, LLC (R171-LRMS) Status:CLIENT DELETE PROHIBITED Status:CLIENT RENEW PROHIBITED Status:CLIENT TRANSFER PROHIBITED Status:CLIENT UPDATE PROHIBITED Registrant ID:CR143925388 Registrant Name:wu liao Registrant Organization: Registrant Street1:xinyierbai 1-203 Registrant Street2: Registrant Street3: Registrant City:beijing Registrant State/Province:beijing Registrant Postal Code:10000 Registrant Country:CN Registrant Phone:+86.13564859684 Registrant Phone Ext.: Registrant FAX: Registrant FAX Ext.: Registrant Email:wuliaijod20d13@hotmail.com Name Server:NS71.DOMAINCONTROL.COM Name Server:NS72.DOMAINCONTROL.COM Domain ID:D48479867-LRMS Domain Name:ARTISANENT.INFO Created On:24-Nov-2012 12:27:33 UTC Last Updated On:24-May-2013 12:39:48 UTC Expiration Date:24-Nov-2013 12:27:33 UTC Sponsoring Registrar:GoDaddy.com, LLC (R171-LRMS) Status:CLIENT DELETE PROHIBITED Status:CLIENT RENEW PROHIBITED Status:CLIENT TRANSFER PROHIBITED Status:CLIENT UPDATE PROHIBITED Registrant ID:CR143925388 Registrant Name:wu liao Registrant Organization: Registrant Street1:xinyierbai 1-203 Registrant Street2: Registrant Street3: Registrant City:beijing Registrant State/Province:beijing Registrant Postal Code:10000 Registrant Country:CN Registrant Phone:+86.13564859684 Registrant Phone Ext.: Registrant FAX: Registrant FAX Ext.: Registrant Email:wuliaijod20d13@hotmail.com Name Server:NS71.DOMAINCONTROL.COM Name Server:NS72.DOMAINCONTROL.COM
The Verdict
Downloaded PoC:
--2013-10-07 15:29:00-- h00p://gtrfeds.artisanent.info/m.exe Resolving gtrfeds.artisanent.info... 158.255.6.116 Connecting to gtrfeds.artisanent.info|158.255.6.116|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 211968 (207K) [application/x-msdownload] Saving to: `m.exe' 100%[=================================>] 211,968 110K/s in 1.9s 2013-10-07 15:29:03 (110 KB/s) - `m.exe' saved [211968/211968] --2013-10-07 15:29:12-- h00p://gtrfeds.artisanent.info/zs.exe Resolving gtrfeds.artisanent.info... 158.255.6.116 Connecting to gtrfeds.artisanent.info|158.255.6.116|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 52736 (52K) [application/x-msdownload] Saving to: `zs.exe' 100%[=================================>] 52,736 56.4K/s in 0.9s 2013-10-07 15:29:14 (56.4 KB/s) - `zs.exe' saved [52736/52736]These are the samples:
2013/10/01 00:58 211,968 m.exe 8df1f6f7cf864df50f02cbab508564b0 2013/09/30 00:58 52,736 zs.exe 872031e4b8f8abfcadecb754a4f383a2And the evidence of my download:


In Virus Total the report it shows:
URL: https://www.virustotal.com/en/file/9dcbb64f365fdf6f80607d297d88134efa4a74ebadc3cc3c5effa9c4f8625937/analysis/
SHA256: 9dcbb64f365fdf6f80607d297d88134efa4a74ebadc3cc3c5effa9c4f8625937
SHA1: d015651dbaeb2a43dd70731af2ab0c7a5ddd9086
MD5: 8df1f6f7cf864df50f02cbab508564b0
File size: 207.0 KB ( 211968 bytes )
File name: m.exe
File type: Win32 EXE
Tags: peexe
Detection ratio: 29 / 45
Analysis date: 2013-10-03 05:47:16 UTC ( 4 days, 1 hour ago )
---------------------------------------------------------------------
Antivirus Result Update
---------------------------------------------------------------------
Bkav HW32.CDB.5ccc 20131002
MicroWorld-eScan Trojan.Generic.9635821 20131003
McAfee ZeroAccess-FBJ!8DF1F6F7CF86 20131003
Malwarebytes Rootkit.0Access.RC 20131003
K7AntiVirus Riskware 20131002
K7GW Riskware 20131002
Norman ZAccess.BHJZ 20131002
TrendMicro-HouseCall TROJ_GEN.F0C2C00J213 20131003
Avast Win32:Malware-gen 20131003
Kaspersky Backdoor.Win32.ZAccess.ecid 20131003
BitDefender Trojan.Generic.9635821 20131003
SUPERAntiSpyware Trojan.Agent/Gen-ZAccess 20131003
Sophos Mal/ZAccess-BL 20131003
Comodo UnclassifiedMalware 20131003
F-Secure Trojan.Generic.9635821 20131003
AntiVir TR/Rogue.9635412 20131002
TrendMicro TROJ_GEN.F0C2C00J213 20131003
McAfee-GW-Edition Artemis!8DF1F6F7CF86 20131003
Emsisoft Trojan.Generic.9635821 (B) 20131003
Antiy-AVL Backdoor/Win32.ZAccess.gen 20131003
Kingsoft Win32.Troj.Generic.a.(kcloud) 20130829
Microsoft TrojanDropper:Win32/Sirefef 20131003
AhnLab-V3 Backdoor/Win32.ZAccess 20131002
GData Trojan.Generic.9635821 20131003
ESET-NOD32 Win32/Sirefef.FY 20131002
Ikarus Trojan.Crypt2 20131003
Fortinet W32/ZAccess.AX!tr 20131003
AVG Crypt2.BJIS 20131002
Panda Trj/Genetic.gen 20131002
and...
URL: https://www.virustotal.com/en/file/8b807576a649a8a6c00ce8b4c655a050ac791ce0dfe1d99fae0d6e4467e069c1/analysis/
SHA256: 8b807576a649a8a6c00ce8b4c655a050ac791ce0dfe1d99fae0d6e4467e069c1
SHA1: a4b84fb5f160bc68ce6f6200c2aba05648909ec4
MD5: 872031e4b8f8abfcadecb754a4f383a2
File size: 51.5 KB ( 52736 bytes )
File name: zs.exe
File type: Win32 EXE
Tags: peexe aspack
Detection ratio: 32 / 48
Analysis date: 2013-10-07 05:42:45 UTC ( 1 hour, 56 minutes ago )
--------------------------------------------------------------------------------
Antivirus Result Update
--------------------------------------------------------------------------------
Bkav HW32.CDB.70c0 20131005
MicroWorld-eScan Gen:Variant.Graftor.116502 20131007
McAfee RDN/Generic Downloader.x!in 20131007
Malwarebytes Trojan.Delf.UKN 20131007
K7AntiVirus Trojan 20131004
K7GW Trojan 20131004
Symantec WS.Reputation.1 20131007
Norman Troj_Generic.QBBRJ 20131007
TrendMicro-HouseCall TROJ_DLOADE.FCX 20131007
Avast Win32:Malware-gen 20131007
Kaspersky Trojan-Downloader.Win32.Delf.bbcn 20131007
BitDefender Gen:Variant.Graftor.116502 20131007
Agnitum Trojan.DL.Delf!1XVARP0nySk 20131006
Emsisoft Gen:Variant.Graftor.116502 (B) 20131007
Comodo UnclassifiedMalware 20131007
F-Secure Gen:Variant.Graftor.116502 20131007
VIPRE Trojan.Win32.Generic!BT 20131007
AntiVir TR/Graftor.116502 20131007
TrendMicro TROJ_DLOADE.FCX 20131007
McAfee-GW-Edition Heuristic.BehavesLike.Win32.Suspicious-PKR.G 20131006
Sophos Mal/Generic-S 20131007
Panda Trj/CI.A 20131006
Kingsoft Win32.TrojDownloader.Delf.bb.(kcloud) 20130829
Microsoft Trojan:Win32/Orsam!rts 20131007
AhnLab-V3 Downloader/Win32.Delf 20131006
GData Gen:Variant.Graftor.116502 20131007
VBA32 suspected of Trojan.Downloader.gen.h 20131005
ESET-NOD32 a variant of Win32/TrojanDownloader.Delf.RWG 20131007
Ikarus Win32.SuspectCrc 20131007
Fortinet W32/Delf.RWG!tr.dldr 20131007
AVG Downloader.Generic13.BNCS 20131006
Baidu-International Trojan.Win32.Downloader.Delf.RWG 20131006
Payload Details
m.exe
Info: ================================================================================ File Name: m.exe File Size: 211968 byte Compile Time: 2005-03-30 03:17:14 <=== Fakes DLL: False Sections: 4 MD5 hash: 8df1f6f7cf864df50f02cbab508564b0 SHA-1 hash: d015651dbaeb2a43dd70731af2ab0c7a5ddd9086 Anti Debug: Yes Anti VM: None -------------------------------------------------------------------------------- Size: 211968 bytes Type: PE32 executable (GUI) Intel 80386, for MS Windows MD5: 8df1f6f7cf864df50f02cbab508564b0 SHA1: d015651dbaeb2a43dd70731af2ab0c7a5ddd9086 Date: 0x42499BAA [Tue Mar 29 18:17:14 2005 UTC] <== Fakes..Builder made.. EP: 0x404c0c .text 0/4 [SUSPICIOUS] CRC: Claimed: 0x33fe1, Actual: 0x33fe1 -------------------------------------------------------------------------------- 0000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ.............. 0010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@....... 0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0030 00 00 00 00 00 00 00 00 00 00 00 00 80 00 00 00 ................ 0040 0E 1F BA 0E 00 B4 09 CD 21 B8 01 4C CD 21 54 68 ........!..L.!Th 0050 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F is program canno 0060 74 20 62 65 20 72 75 6E 20 69 6E 20 44 4F 53 20 t be run in DOS 0070 6D 6F 64 65 2E 0D 0D 0A 24 00 00 00 00 00 00 00 mode....$....... 0080 50 45 00 00 4C 01 04 00 AA 9B 49 42 00 00 00 00 PE..L.....IB.... 0090 00 00 00 00 E0 00 82 81 0B 01 42 18 00 72 00 00 ..........B..r.. 00A0 00 C6 02 00 00 00 00 00 0C 4C 00 00 00 10 00 00 .........L...... [...] Sections: ================================================================================ Name VirtAddr VirtSize RawSize Entropy -------------------------------------------------------------------------------- .text 0x1000 0x718c 0x7200 4.942657 .rsrc 0x9000 0x29ca4 0x29e00 6.244711 .reloc 0x33000 0x244 0x400 1.173713 .rdata 0x34000 0x2228 0x2400 5.573327 File and URL: ================================================================================ FILE: kernel32.dll FILE: user32.dll FILE: d3d8thk.dll FILE: kernel32.dll FILE: user32.dll FILE: KERNEL32.DLL FILE: OPENGL32.dll FILE: advapi32.dll FILE: d3d8.dll FILE: d3d8thk.dll FILE: reity.exe URL: None Suspicious API Functions: ================================================================================ Func. Name: OpenFileMappingA Func. Name: GetModuleHandleA Func. Name: FindResourceExA Func. Name: GetModuleFileNameA Func. Name: GetComputerNameA Func. Name: VirtualAllocEx <===== Func. Name: VirtualAllocEx <===== Func. Name: GetTempPathA Func. Name: GetModuleFileNameA Func. Name: IsDebuggerPresent Func. Name: FindResourceExW Func. Name: GetVersionExA Func. Name: GetFileAttributesExA Func. Name: GetFileAttributesExA Func. Name: SetWindowsHookExA Func. Name: GetProcAddress Func. Name: FindResourceA Func. Name: ConnectNamedPipe Func. Name: FindFirstFileA Func. Name: VirtualProtectEx Func. Name: GetFileAttributesA Func. Name: GetComputerNameA Suspicious API Anti-Debug: Anti Debug: IsDebuggerPresent Version info ================================================================================ LegalCopyright: Voleter it(c) \xa9 2012 InternalName: ejbnisgj FileVersion: a 2 RC87.44060017.189e CompanyName: Voleter it(c) ProductName: Voleter it(c) ProductVersion: 122.19153 RelC FileDescription: Voleter it(c) OriginalFilename: ejbnisgj.exe Translation: 0x0409 0x04b0I won't write much this in very details, please refer to my previous analysis-->HERE in the binary part, to tell us a lot. Please see the correct statement in VirusTotal behavior analysis here-->HERE, but see the VT summary is below:

The usage of GeoIP: the attempt to download it from MaxMind site and the UDP communication tells usual pattern of ZA.
Again, please refer to this-->HERE for the details.
PoC of ZeroAccess Botnet is up and alive
ZeroAccess network:
When I run it.. below is the DNS communication, I gave ZA all they want to access the botnet (if there is a botnet still up..)
Honestly, why I did not see ANY downtime of these ZeroAccess peer communication?
Now hickups or slowdown in this communication at all, what really was shutdowned??
Later on in the PCAP sample you can count yourself how fast the rotation peer access were called, this is just as per usual speed I saw in previous analysis of ZeroAccess, nothing changed (sadly..)

The ZeroAccess "acompanied" Trojan "A" - downloader: zs.exe
Binary info:
File: ./zs.exe Size: 52736 bytes Type: PE32 executable (GUI) Intel 80386, for MS Windows MD5: 872031e4b8f8abfcadecb754a4f383a2 SHA1: a4b84fb5f160bc68ce6f6200c2aba05648909ec4 Date: 0x5247BBB7 [Sun Sep 29 05:33:43 2013 UTC] EP: 0x42e001 .DB 10/12 [SUSPICIOUS] CRC: Claimed: 0x0, Actual: 0x1a3f8 [SUSPICIOUS] -------------------------------------------------------------------------------- Packer: ASProtect V2.X DLL -> Alexey Solodovnikov - additionalASProtect V2.X DLL -> Alexey Solodovnikov ASPack v2.12 - additionalASPack v2.12 ASPack v2.1 - additional -------------------------------------------------------------------------------- File Name: zs.exe File Size: 52736 byte Compile Time: 2013-09-29 14:33:43 DLL: False Sections: 12 MD5 hash: 872031e4b8f8abfcadecb754a4f383a2 SHA-1 hash: a4b84fb5f160bc68ce6f6200c2aba05648909ec4 Anti Debug: None Anti VM: None --------------------------------------------------------------------------------- Entry Point at 0xbc01 Virtual Address is 0x42e001 0000 4D 5A 50 00 02 00 00 00 04 00 0F 00 FF FF 00 00 MZP............. 0010 B8 00 00 00 00 00 00 00 40 00 1A 00 00 00 00 00 ........@....... 0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0030 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 ................ 0040 BA 10 00 0E 1F B4 09 CD 21 B8 01 4C CD 21 90 90 ........!..L.!.. 0050 54 68 69 73 20 70 72 6F 67 72 61 6D 20 6D 75 73 This program mus 0060 74 20 62 65 20 72 75 6E 20 75 6E 64 65 72 20 57 t be run under W 0070 69 6E 33 32 0D 0A 24 37 00 00 00 00 00 00 00 00 in32..$7........ 0080 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ [...] 00F0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0100 50 45 00 00 4C 01 0C 00 B7 BB 47 52 00 00 00 00 PE..L.....GR.... 0110 00 00 00 00 E0 00 8E 81 0B 01 02 19 00 C2 01 00 ................ 0120 00 62 00 00 00 00 00 00 01 E0 02 00 00 10 00 00 .b.............. 0130 00 E0 01 00 00 00 40 00 00 10 00 00 00 02 00 00 ......@......... [...] Resource entries ================================================================================ Name RVA Size Lang Sublang Type -------------------------------------------------------------------------------- RT_STRING 0x2c218 0x74 LANG_NEUTRAL SUBLANG_NEUTRAL data RT_STRING 0x2c28c 0x298 LANG_NEUTRAL SUBLANG_NEUTRAL data RT_STRING 0x2c524 0xd4 LANG_NEUTRAL SUBLANG_NEUTRAL data RT_STRING 0x2c5f8 0xa4 LANG_NEUTRAL SUBLANG_NEUTRAL data RT_STRING 0x2c69c 0x29c LANG_NEUTRAL SUBLANG_NEUTRAL data RT_STRING 0x2c938 0x368 LANG_NEUTRAL SUBLANG_NEUTRAL empty RT_STRING 0x2cca0 0x288 LANG_NEUTRAL SUBLANG_NEUTRAL empty RT_RCDATA 0x2cf28 0x10 LANG_NEUTRAL SUBLANG_NEUTRAL empty RT_RCDATA 0x2cf38 0x128 LANG_NEUTRAL SUBLANG_NEUTRAL empty Sections ================================================================================ Name VirtAddr VirtSize RawSize Entropy -------------------------------------------------------------------------------- .text 0x1000 0x1c000 0x9800 7.985545 [SUSPICIOUS] .itext 0x1d000 0x1000 0x400 6.023927 .data 0x1e000 0x2000 0xa00 7.169703 [SUSPICIOUS] .bss 0x20000 0x5000 0x0 0.000000 [SUSPICIOUS] .idata 0x25000 0x1000 0x600 6.466433 .didata 0x26000 0x1000 0x200 2.176323 .tls 0x27000 0x1000 0x0 0.000000 [SUSPICIOUS] .rdata 0x28000 0x1000 0x200 0.210826 [SUSPICIOUS] .reloc 0x29000 0x3000 0x0 0.000000 [SUSPICIOUS] .rsrc 0x2c000 0x2000 0x800 6.544777 .DB 0x2e000 0x2000 0x1200 5.804077 .adata 0x30000 0x1000 0x0 0.000000 [SUSPICIOUS] -------------------------------------------------------------------------------- File and URL: FILE: kernel32.dll FILE: user32.dll FILE: kernel32.dll FILE: oleaut32.dll FILE: advapi32.dll FILE: user32.dll FILE: user32.dll URL: None -------------------------------------------------------------------------------- Suspicious API Functions: Func. Name: GetProcAddress Func. Name: GetModuleHandleA Func. Name: LoadLibraryA Func. Name: LoadLibraryA -------------------------------------------------------------------------------- Suspicious Sections: Sect. Name: .text^@^@^@ MD5 hash: 607a461cb659e5a10b566434de7fa3d3 SHA-1 hash: b1bf940acbcb37877a5513d7385765d1937a0ea1 Sect. Name: .data^@^@^@ MD5 hash: 46564b11f19cb7c4fd0da8e27fd4f394 SHA-1 hash: 03f78fc221ae145c9311ef0bfd98b0d6e3acd793 Sect. Name: .bss^@^@^@^@ MD5 hash: d41d8cd98f00b204e9800998ecf8427e SHA-1 hash: da39a3ee5e6b4b0d3255bfef95601890afd80709 Sect. Name: .tls^@^@^@^@ MD5 hash: d41d8cd98f00b204e9800998ecf8427e SHA-1 hash: da39a3ee5e6b4b0d3255bfef95601890afd80709 Sect. Name: .rdata^@^@ MD5 hash: 3dbb241e3190fbd14c8a44da3a00e61b SHA-1 hash: 8247038ba6b52fb73328ca11fe47df8633ced36f Sect. Name: .reloc^@^@ MD5 hash: d41d8cd98f00b204e9800998ecf8427e SHA-1 hash: da39a3ee5e6b4b0d3255bfef95601890afd80709 Sect. Name: .adata^@^@ MD5 hash: d41d8cd98f00b204e9800998ecf8427e SHA-1 hash: da39a3ee5e6b4b0d3255bfef95601890afd80709
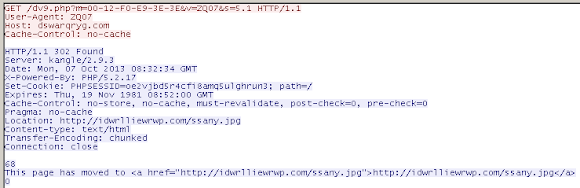
What does it do? Yes, is a downloader, ALIVE one:, it downloaded WHAT LOOKS LIKE IMAGE FILE from dswarqryg.com
You'll see some requests like below:
..with each request session is:
..and redirect you to download these:
PS: BLOCK THESE DOMAINS!!! idwrlliewrwp.com/ssany.jpg sd.newaot.com/xxswq.jpgPoC:

Of course the purpose is the camouflage of PE file download blocking:

We can see it actualy saved in %TEMP%...

As PE binaries of ANOTHER malware file...

We found also others download URL and saved file name in the binary:

And from reversing, it showed it is targeted to below OS version:
32-bit Edition 64-bit Edition Windows Server 2003 Windows Server 2003 R2 Windows Vista Windows Server 2008 Windows 7 Windows Server 2008 R2 Windows 2000 Windows XP
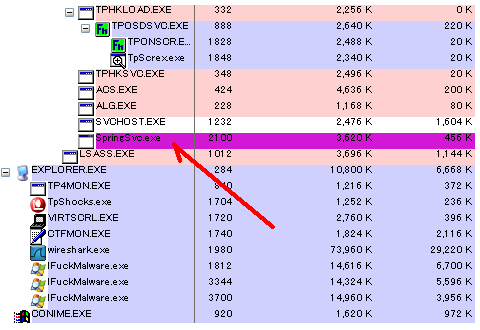
Zero Access "Accompanied" Trojan "B" - the Backdoor as Service: "SpringSvc.exe"
Well, the binary downloaded to be saved in the %WINDOWS% directory with below VT details:
URL: https://www.virustotal.com/en/file/0ddb20210558a5d95aa90ebbda3c666b46321af1c70319ce8aebbc1dfcfd754e/analysis/
SHA256:0ddb20210558a5d95aa90ebbda3c666b46321af1c70319ce8aebbc1dfcfd754e
SHA1: 6388534e59b78f1d68165ab454f3f5bfd3803fde
MD5: 9b34ca74c08a890af5b9f692d68516c3
File size: 354.0 KB ( 362496 bytes )
File name: SpringSvc.exe
File type: Win32 EXE
Tags: peexe
Detection ratio: 23 / 48
Analysis date: 2013-10-07 11:27:28 UTC ( 2 minutes ago )
--------------------------------------------------------------------------
Antivirus Result Update
--------------------------------------------------------------------------
Bkav HW32.CDB.B3ff 20131007
MicroWorld-eScan Gen:Trojan.Heur.FU.wS0@aKIipfmj 20131007
CAT-QuickHeal (Suspicious) - DNAScan 20131007
McAfee Artemis!9B34CA74C08A 20131007
Malwarebytes Trojan.Agent.EDC 20131007
K7AntiVirus Trojan 20131004
K7GW Trojan 20131004
Symantec WS.Reputation.1 20131007
TrendMicro-HouseCall TROJ_GEN.R0CBH07J613 20131007
Kaspersky Trojan.Win32.Agent.acbkp 20131007
BitDefender Gen:Trojan.Heur.FU.wS0@aKIipfmj 20131007
Agnitum Suspicious!SA 20131006
Sophos Mal/Generic-S 20131007
F-Secure Gen:Trojan.Heur.FU.wS0@aKIipfmj 20131007
AntiVir TR/Spy.362496.35 20131007
McAfee-GW-Edition Heuristic.LooksLike.Win32.SuspiciousPE.C 20131007
Emsisoft Gen:Trojan.Heur.FU.wS0@aKIipfmj (B) 20131007
Panda Suspicious file 20131007
GData Gen:Trojan.Heur.FU.wS0@aKIipfmj 20131007
AhnLab-V3 Trojan/Win32.Agent 20131007
ESET-NOD32 a variant of Win32/Spy.Wagiclas.AC 20131007
Fortinet W32/Agent.ACBKP!tr 20131007
AVG PSW.Generic12.AYU 20131007
..and the binary was compiled by Borland-base Builder/SDK
FastMM Borland Edition 2004, 2005 Pierre le Riche / Professional Software Development SOFTWARE\Borland\Delphi\RTL Software\Borland\Locales Software\Borland\Delphi\Locales
OK.. OK..OK, got it! But WHAT does it Do??
This downloaded file will be executed by the previous downloader:
And does the process injection the reside as service:
PoC of service calls from reversing:
StartServiceA StartServiceCtrlDispatcherA CreateServiceAAnd then this SpringSvc.exe contacts mothership in kdsousom.com / 67.198.168 .115 which poking for "package":


And a grabber:
<form name=" name= type="hidden" type=hidden <input value= /select> /textarea> </form Elements Item Forms Length tagName INPUT type text Name Value...of the phishing credential data:
NAME FIRST title LAST PHONE ZIP MAIL BIRTH YYYY yyyy password checkbox checked radio checked checked TEXTAREA call me,Thank you. not sure SELECT sex options length text selectedindex onchange value selectedindex SUBMIT SEARCH Value LOGIN SIGN IN submit Click
Yes, is a backdoor requesting and passing credentials which we're sure there's nothing good in it..
Epilogue
Friends, my point is simple, ZeroAccess is out there still lurking at us.
These samples and network are fresh and new.. this post is a PoC of the existance of ZeroAccess in the wild.
Any of the bad domains mentioned are exposed as target to be shutdown.
I will share the samples shortly, after sorting things out. Stay secure!
Additional
@threatintel @artem_i_baranov you guys are aware that Zerokit (also named Rovnix) is a bootkit and has nothing to do with ZeroAccess?
— Peter Kleissner (@Kleissner) October 3, 2013
@Trojan7Sec @unixfreaxjp Damn no it's not dead yet. more than 1100 hits today (on ~2000 in average when it *was up*) http://t.co/Wn2XTAT7Xc
— Tigzy (@TigzyRK) October 7, 2013
@MalwareMustDie @essachin @CERTGIB There are probably thousands of 'em, but here are some more - http://t.co/TQx52dac8U
— Conrad Longmore (@ConradLongmore) October 7, 2013
Samples Download
We share the samples and the malicious botnet traffic with trojan callback traffic for raising detection ratio and research purpose only to known researchers.
I will ask many questions to share the sample above to none of the described criteria.
Here's the downloads, click the picture to access:
Samples/PE Binaries
(password needed - ask by DM to @malwaremustdie in twitter)
Traffic in PCAP:
(no password)
#MalwareMustDie!